Ethical Hacking > QUESTIONS & ANSWERS > CIS 3250 Ethics and Computer Science CIS 3250 EXAM #2 guide | Florida State University (All)
CIS 3250 Ethics and Computer Science CIS 3250 EXAM #2 guide | Florida State University
Document Content and Description Below
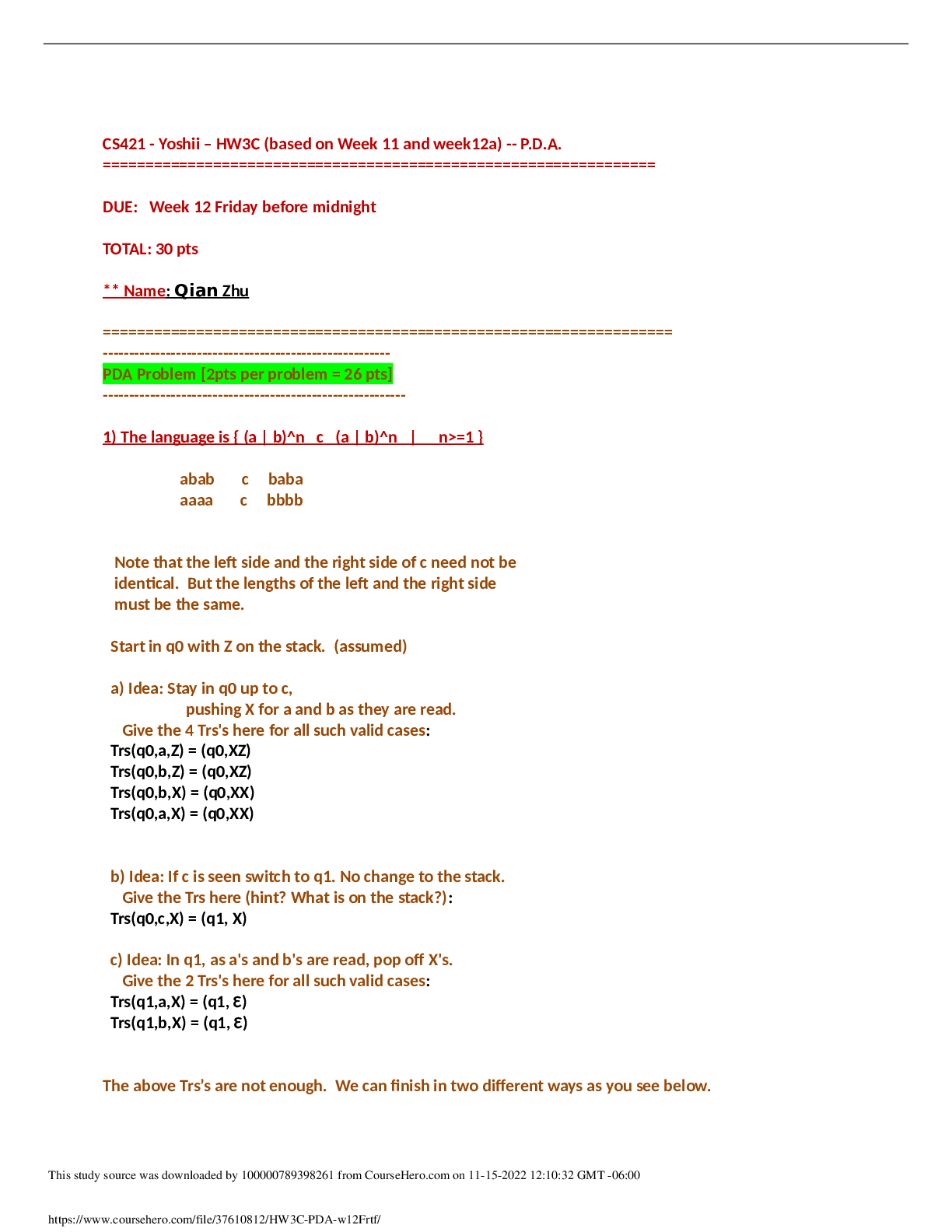
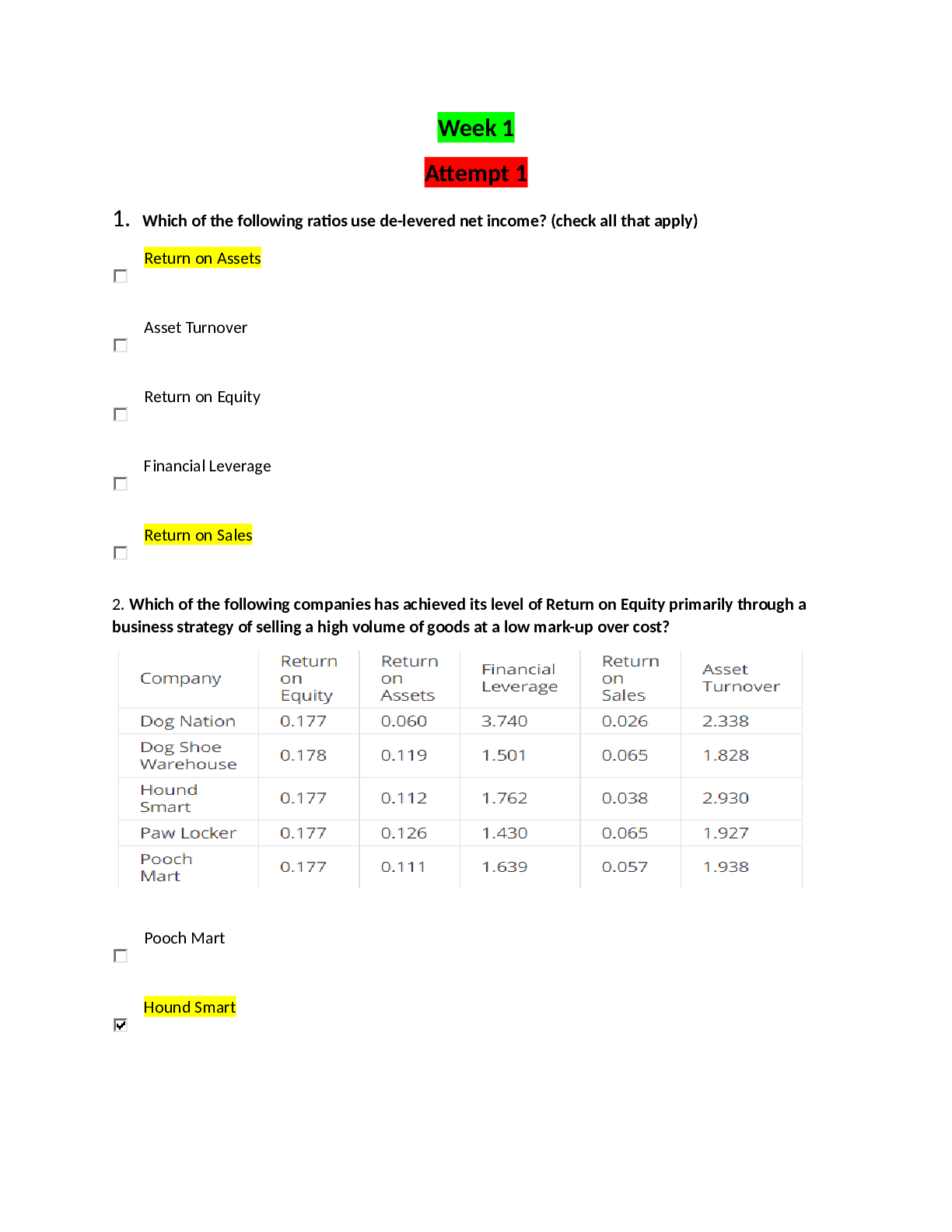
Florida State University CIS 3250 CIS 3250 EXAM #2 guide CIS 3250 EXAM #2 Quiz #3 The legal guidelines for determining whether material is obscene include all of the following EXCEPT… ... Which of the following requirements was a key provision of the Children's Internet Protection Act (CIPA)? Which of the following limits deceptive commercial email and outlines spammers' responsibilities: What areas is covered by the topics of Free Speech? Which one of the media areas has the most First Amendment protection? Anonymizers allow a user to: Quiz #4 One of the reasons the court ruled against Napster was: There are four factors to consider in deciding whether a use of copyrighted material is a fair use. Which of the following is not one of those factors? In the term "Free Software", "free" implies all of the following except one. Which one? Which of the following is not a way for software to be protected against copyright infringement? When was the first U.S. copyright law passed? The "safe harbor" provisions of _______________ protect Websites from lawsuits and criminal charges for copyright infringement when users post infringing material. Sega v. Accolade, Inc. (1992) helped determine that reverse engineering was allowable (fair research use) in order to make a compatible product. All peer-to-peer technologies were found to be illegal as a result of the Napster case. "Anticircumvention" and "safe harbor" are the two significant parts of the Digital Millennium Copyright Act. The Digital Millennium Copyright Act gives companies ways to threaten fair use, freedom of speech, research, competition, reverse engineering, and innovation. Which of the following is not an exclusive right (subject to some exceptions) granted by copyright law? A: Profit from the work Copyright law protects processes and inventions, while patent law protects the Quiz #5 In its early years, Internet security was a primary design concern. A broad interpretation of the Computer Fraud and Abuse Act might criminalize common activities of millions of people. Phone phreaking is a form of hacking that involves manipulating the telephone system. Stuxnet was a sophisticated worm, that targeted a particular type of control system. Honey pots is defined as which of the following? In 1999, a French court ordered Yahoo! to block access by French people to Phishing is defined as which of the following? Which of the following is an example of biometrics: In the early days of computing (1960's to the early 1970's), a "hacker" was: Libel tourism does NOT have which of the following characteristics? White hat hackers use their skills to demonstrate system vulnerabilities and improve security. The term hacker was a creative programmer who wrote very elegant or clever programs until the 1970s. Hacktivism is Pharming is defined as which of the following? Web sites that look attractive to hackers, but are closely monitored so that everything the hacker does at the site is recorded and studied are known as: Denial-of-Service (DOS) is defined as which of the following? In 1878, women telephone operators were hired as a result of phone phreakers. [Show More]
Last updated: 2 months ago
Preview 1 out of 4 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$7.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Nov 07, 2022
Number of pages
4
Written in
Additional information
This document has been written for:
Uploaded
Nov 07, 2022
Downloads
0
Views
107




.png)
.png)
.png)
.png)
.png)
.png)
.png)




