SC-900: Microsoft Security, Compliance, and Identity Fundamentals. Tests. Q&A Plus Explanations in 60 Pages.
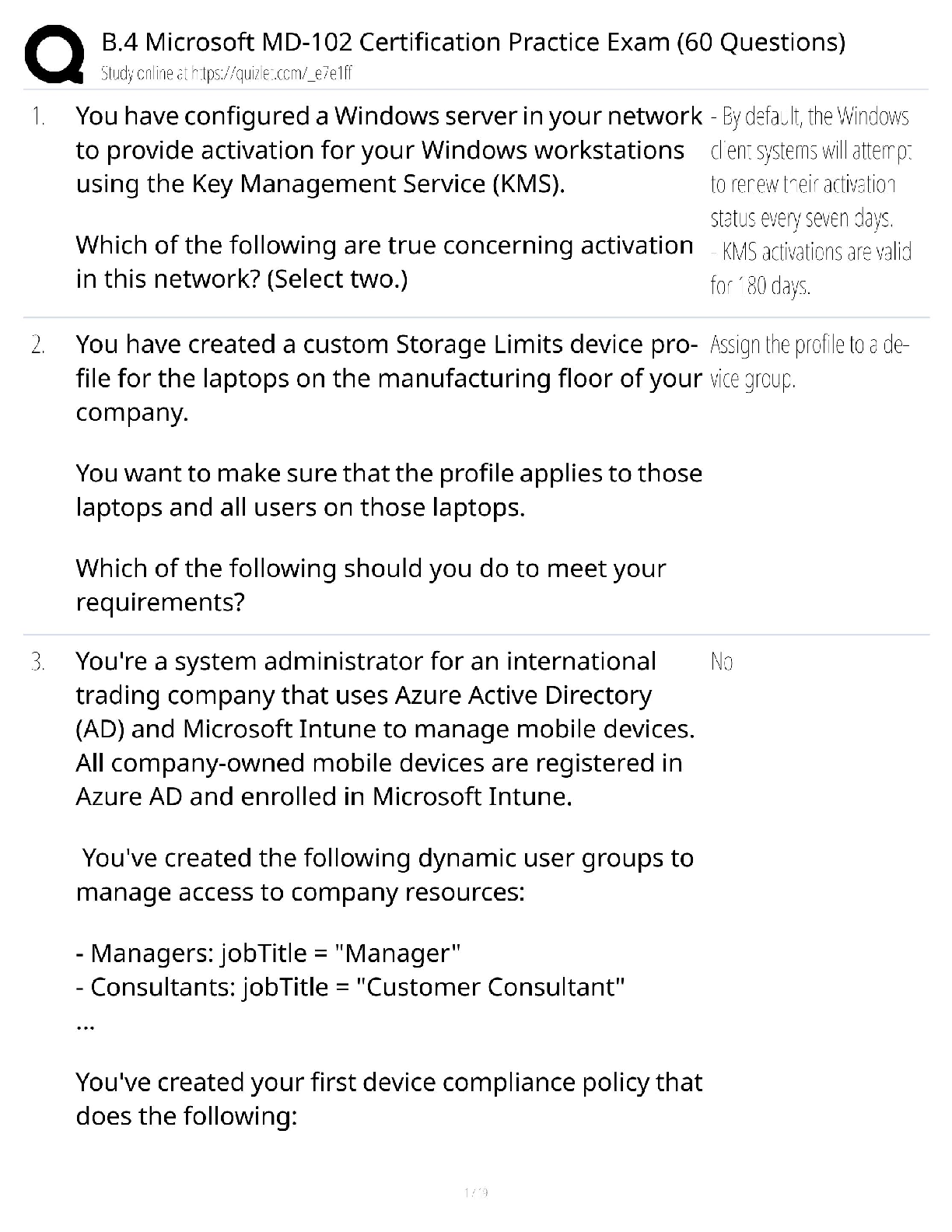
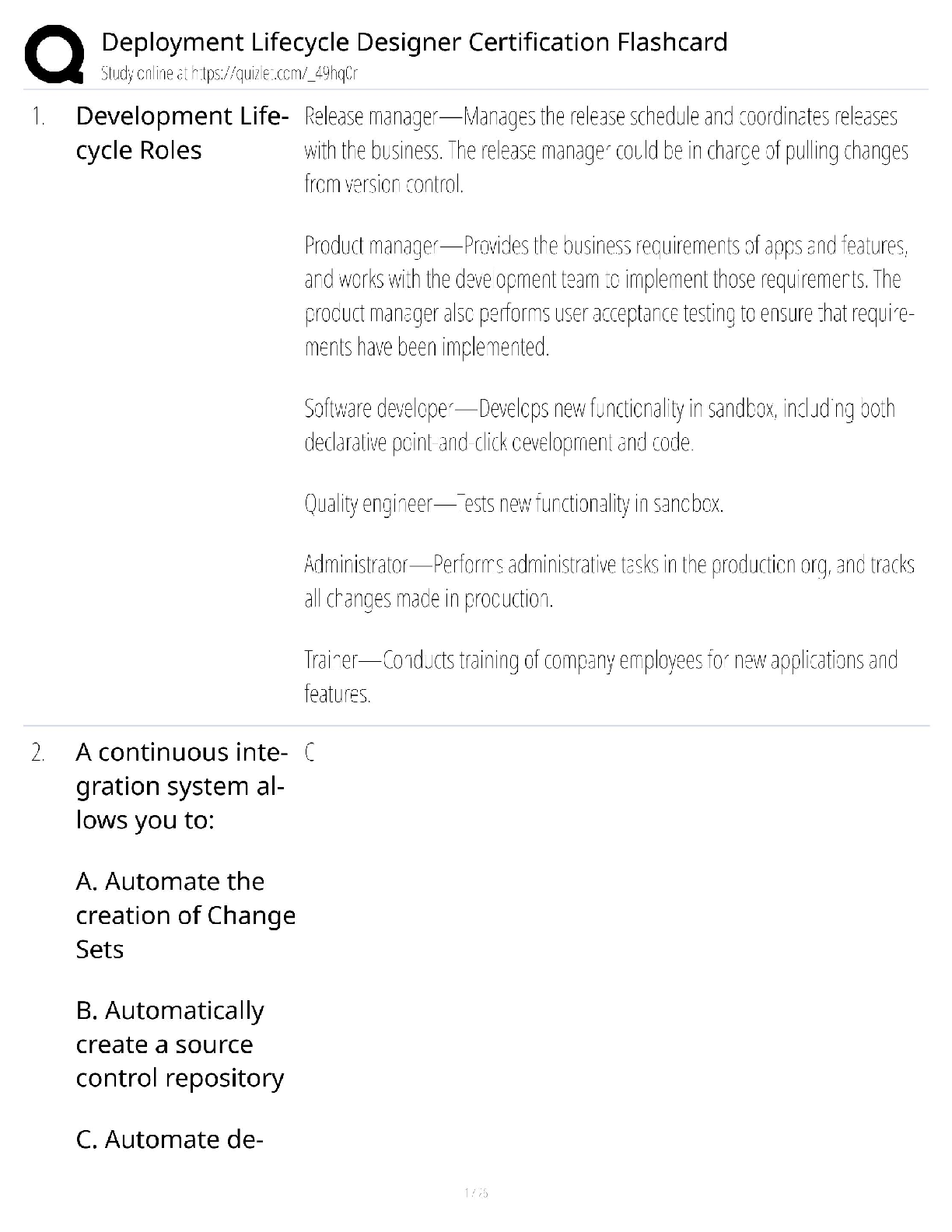
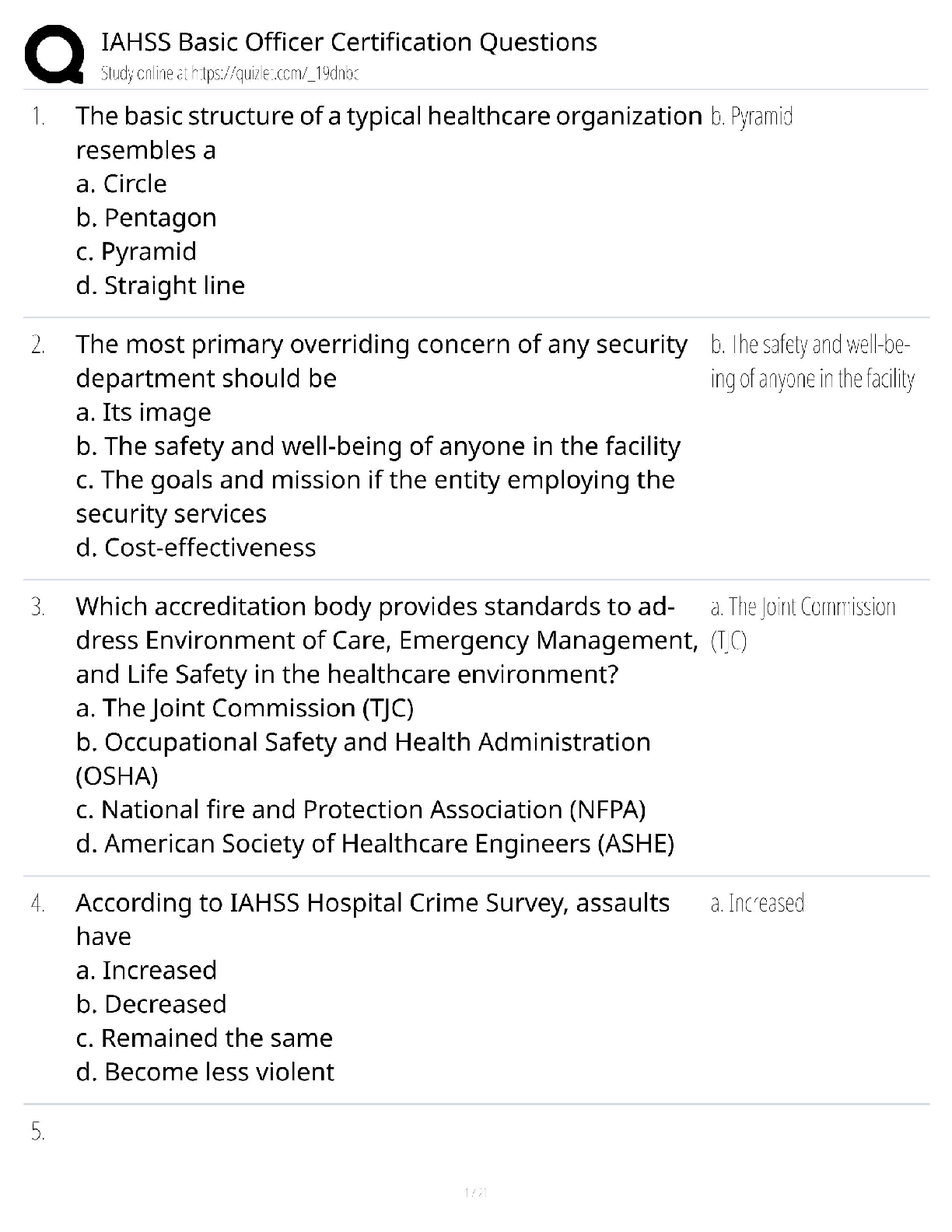
Document Content and Description Below
SC-900: Microsoft Security, Compliance, and Identity Fundamentals
- Expert Veri¦ed, Online, Free.
� Custom View Settings
Topic 1 - Single Topic
Question #1 Topic 1
HOTSPOT -
For each of the fol
...
lowing statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Question #2 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Reference:
https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/get-started/
Question #3 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Reference:
https://docs.microsoft.com/en-us/azure/security/fundamentals/customer-lockbox-overview
Question #4 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Next Questions a
- Expert Veri¦ed, Online, Free.
� Custom View Settings
Question #5 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Federation is a collection of domains that have established trust.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/whatis-fed
Question #6 Topic 1
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Box 1: Yes -
System updates reduces security vulnerabilities, and provide a more stable environment for end users. Not applying updates leaves unpatched
vulnerabilities and results in environments that are susceptible to attacks.
Box 2: Yes -
Box 3: Yes -
If you only use a password to authenticate a user, it leaves an attack vector open. With MFA enabled, your accounts are more secure.
Reference:
https://docs.microsoft.com/en-us/azure/security-center/secure-score-security-controls
Question #7 Topic 1
Which score measures an organization's progress in completing actions that help reduce risks associated to data protection and regulatory
standards?
A. Microsoft Secure Score
B. Productivity Score
C. Secure score in Azure Security Center
D. Compliance score
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-manager?view=o365-worldwide https://docs.microsoft.com/enus/microsoft-365/compliance/compliance-score-calculation?view=o365-worldwide
Question #8 Topic 1
What do you use to provide real-time integration between Azure Sentinel and another security source?
A. Azure AD Connect
B. a Log Analytics workspace
C. Azure Information Protection
D. a connector
To on-board Azure Sentinel, you ¦rst need to connect to your security sources. Azure Sentinel comes with a number of connectors for Microsoft
solutions, including Microsoft 365 Defender solutions, and Microsoft 365 sources, including O¨ce 365, Azure AD, Microsoft Defender for
Identity, and Microsoft Cloud App
Security, etc.
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/overview
` Next Questions a
- Expert Veri¦ed, Online, Free.
� Custom View Settings
Question #9 Topic 1
Which Microsoft portal provides information about how Microsoft cloud services comply with regulatory standard, such as International
Organization for
Standardization (ISO)?
A. the Microsoft Endpoint Manager admin center
B. Azure Cost Management + Billing
C. Microsoft Service Trust Portal
D. the Azure Active Directory admin center
The Microsoft Service Trust Portal contains details about Microsoft's implementation of controls and processes that protect our cloud services
and the customer data therein.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/get-started-with-service-trust-portal?view=o365-worldwide
Question #10 Topic 1
In the shared responsibility model for an Azure deployment, what is Microsoft solely responsible for managing?
A. the management of mobile devices
B. the permissions for the user data stored in Azure
C. the creation and management of user accounts
D. the management of the physical hardware
Question #11 Topic 1
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Box 1: Yes -
Box 2: Yes -
Box 3: No -
The Zero Trust model does not assume that everything behind the corporate ¦rewall is safe, the Zero Trust model assumes breach and veri¦es
each request as though it originated from an uncontrolled network.
Reference:
https://docs.microsoft.com/en-us/security/zero-trust/
Question #12 Topic 1
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Reference:
https://privacy.microsoft.com/en-US/
` Next Questions a
- Expert Veri¦ed, Online, Free.
� Custom View Settings
Question #13 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Question #14 Topic 1
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Box 1: Yes -
A certi¦cate is required that provides a private and a public key.
Box 2: Yes -
The public key is used to validate the private key that is associated with a digital signature.
Box 3: Yes -
The private key, or rather the password to the private key, validates the identity of the signer.
Reference:
https://support.microsoft.com/en-us/o¨ce/obtain-a-digital-certi¦cate-and-create-a-digital-signature-e3d9d813-3305-4164-a820-2e063d86e512
https://docs.microsoft.com/en-us/dynamics365/¦n-ops-core/¦n-ops/organization-administration/electronic-signature-overview
Question #15 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Question #16 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Reference:
https://docs.microsoft.com/en-us/azure/app-service/overview-authentication-authorization
` Next Questions a
- Expert Veri¦ed, Online, Free.
� Custom View Settings
Question #17 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/external-identities/what-is-b2b
Question #18 Topic 1
In the Microsoft Cloud Adoption Framework for Azure, which two phases are addressed before the Ready phase? Each correct answer presents a
complete solution.
NOTE: Each correct selection is worth one point.
A. Plan
B. Manage
C. Adopt
D. Govern
E. De¦ne Strategy
Reference:
https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/overview
Question #19 Topic 1
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Question #20 Topic 1
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
` Next Questions a
- Expert Veri¦ed, Online, Free.
� Custom View Settings
Question #21 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Reference:
https://docs.microsoft.com/en-us/security/benchmark/azure/baselines/cloud-services-security-baseline
Question #22 Topic 1
What is an example of encryption at rest?
A. encrypting communications by using a site-to-site VPN
B. encrypting a virtual machine disk
C. accessing a website by using an encrypted HTTPS connection
D. sending an encrypted email
Reference:
https://docs.microsoft.com/en-us/azure/security/fundamentals/encryption-atrest
Question #23 Topic 1
What can you use to provide a user with a two-hour window to complete an administrative task in Azure?
A. Azure Active Directory (Azure AD) Privileged Identity Management (PIM) Most Voted
B. Azure Multi-Factor Authentication (MFA)
C. Azure Active Directory (Azure AD) Identity Protection
D. conditional access policies
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/concept-conditional-access-policy-common
Question #24 Topic 1
In a hybrid identity model, what can you use to sync identities between Active Directory Domain Services (AD DS) and Azure Active Directory
(Azure AD)?
A. Active Directory Federation Services (AD FS)
B. Azure Sentinel
C. Azure AD Connect
D. Azure Ad Privileged Identity Management (PIM)
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/whatis-azure-ad-connect
` Next Questions a
- Expert Veri¦ed, Online, Free.
� Custom View Settings
Question #25 Topic 1
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Box 1: Yes -
Azure AD supports custom roles.
Box 2: Yes -
Global Administrator has access to all administrative features in Azure Active Directory.
Box 3: No -
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/roles/concept-understand-roles https://docs.microsoft.com/en-us/azure/activedirectory/roles/permissions-reference
Question #26 Topic 1
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Box 1: No -
Azure Active Directory (Azure AD) is a cloud-based user identity and authentication service.
Box 2: Yes -
Microsoft 365 uses Azure Active Directory (Azure AD). Azure Active Directory (Azure AD) is included with your Microsoft 365 subscription.
Box 3: Yes -
Azure Active Directory (Azure AD) is a cloud-based user identity and authentication service.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/enterprise/about-microsoft-365-identity?view=o365-worldwide
Question #27 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Biometrics templates are stored locally on a device.
Reference:
https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-overview
Question #28 Topic 1
What is the purpose of Azure Active Directory (Azure AD) Password Protection?
A. to control how often users must change their passwords
B. to identify devices to which users can sign in without using multi-factor authentication (MFA)
C. to encrypt a password by using globally recognized encryption standards
D. to prevent users from using speci¦c words in their passwords
Azure AD Password Protection detects and blocks known weak passwords and their variants, and can also block additional weak terms that are
speci¦c to your organization.
With Azure AD Password Protection, default global banned password lists are automatically applied to all users in an Azure AD tenant. To
support your own business and security needs, you can de¦ne entries in a custom banned password list.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-password-ban-bad-on-premises
` Next Questions a
- Expert Veri¦ed, Online, Free.
� Custom View Settings
Question #29 Topic 1
Which Azure Active Directory (Azure AD) feature can you use to evaluate group membership and automatically remove users that no longer require
membership in a group?
A. access reviews Most Voted
B. managed identities
C. conditional access policies
D. Azure AD Identity Protection
Azure Active Directory (Azure AD) access reviews enable organizations to e¨ciently manage group memberships, access to enterprise
applications, and role assignments.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/governance/access-reviews-overview
Question #30 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Multi-factor authentication is a process where a user is prompted during the sign-in process for an additional form of identi¦cation, such as to
enter a code on their cellphone or to provide a ¦ngerprint scan.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-mfa-howitworks
Question #31 Topic 1
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Box 1: Yes -
Box 2: No -
Conditional Access policies are enforced after ¦rst-factor authentication is completed.
Box 3: Yes -
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/overview
Question #32 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Reference:
https://docs.microsoft.com/en-us/defender-for-identity/what-is
` Next Questions a
- Expert Veri¦ed, Online, Free.
� Custom View Settings
Question #33 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Microsoft Defender for Identity is a cloud-based security solution that leverages your on-premises Active Directory signals to identify, detect,
and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization.
Reference:
https://docs.microsoft.com/en-us/defender-for-identity/what-is
Question #34 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Azure Active Directory (Azure AD) is a cloud-based user identity and authentication service.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/enterprise/about-microsoft-365-identity?view=o365-worldwide
Question #35 Topic 1
Which Azure Active Directory (Azure AD) feature can you use to provide just-in-time (JIT) access to manage Azure resources?
A. conditional access policies
B. Azure AD Identity Protection
C. Azure AD Privileged Identity Management (PIM) Most Voted
D. authentication method policies
Azure AD Privileged Identity Management (PIM) provides just-in-time privileged access to Azure AD and Azure resources
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-con¦gure
Question #36 Topic 1
Which three authentication methods can be used by Azure Multi-Factor Authentication (MFA)? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. text message (SMS)
B. Microsoft Authenticator app
C. email veri¦cation
D. phone call
E. security question
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-authentication-methods
` Next Questions a
- Expert Veri¦ed, Online, Free.
� Custom View Settings
Question #37 Topic 1
Which Microsoft 365 feature can you use to restrict communication and the sharing of information between members of two departments at your
organization?
A. sensitivity label policies
B. Customer Lockbox
C. information batteries
D. Privileged Access Management (PAM)
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/information-barriers
Question #38 Topic 1
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/overview
Question #39 Topic 1
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Box 1: Yes -
Conditional access policies can be applied to all users
Box 2: No -
Conditional access policies are applied after ¦rst-factor authentication is completed.
Box 3: Yes -
Users with devices of speci¦c platforms or marked with a speci¦c state can be used when enforcing Conditional Access policies.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/overview
Question #40 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
When you register an application through the Azure portal, an application object and service principal are automatically created in your home
directory or tenant.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/develop/howto-create-service-principal-portal
` Next Questions a
- Expert Veri¦ed, Online, Free.
� Custom View Settings
Question #41 Topic 1
Which three authentication methods does Windows Hello for Business support? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. ¦ngerprint
B. facial recognition
C. PIN
D. email veri¦cation
E. security question
Reference:
https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-how-it-works-authentication
Question #42 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/fundamentals/concept-fundamentals-security-defaults
Question #43 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Reference:
https://docs.microsoft.com/en-us/cloud-app-security/what-is-cloud-app-security
Question #44 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Reference:
https://docs.microsoft.com/en-us/azure/ddos-protection/ddos-protection-overview
` Next Questions a
1/9/22, 3:05 PM SC-900 Exam – Free Actual Q&As, Page 12 | ExamTopics
https://www.examtopics.com/exams/microsoft/sc-900/view/12/ 1/3
- Expert Veri¦ed, Online, Free.
� Custom View Settings
Question #45 Topic 1
What should you use in the Microsoft 365 security center to view security trends and track the protection status of identities?
A. Attack simulator
B. Reports
C. Hunting
D. Incidents
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/o¨ce-365-security/reports-and-insights-in-security-and-compliance?view=o365-
worldwide
Question #46 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender/incidents-overview?view=o365-worldwide
1/9/22, 3:05 PM SC-900 Exam – Free Actual Q&As, Page 12 | ExamTopics
https://www.examtopics.com/exams/microsoft/sc-900/view/12/ 2/3
Question #47 Topic 1
What are two capabilities of Microsoft Defender for Endpoint? Each correct selection presents a complete solution.
NOTE: Each correct selection is worth one point.
A. automated investigation and remediation
B. transport encryption
C. shadow IT detection
D. attack surface reduction
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/microsoft-defender-endpoint?view=o365-worldwide
Question #48 Topic 1
DRAG DROP -
Match the Azure networking service to the appropriate description.
To answer, drag the appropriate service from the column on the left to its description on the right. Each service may be used once, more than
once, or not at all.
NOTE: Each correct match is worth one point.
Select and Place:
Box 1: Azure Firewall -
Azure Firewall provide Source Network Address Translation and Destination Network Address Translation.
Box 2: Azure Bastion -
Azure Bastion provides secure and seamless RDP/SSH connectivity to your virtual machines directly from the Azure portal over TLS.
Box 3: Network security group (NSG)
You can use an Azure network security group to ¦lter network tra¨c to and from Azure resources in an Azure virtual network.
Reference:
https://docs.microsoft.com/en-us/azure/networking/fundamentals/networking-overview https://docs.microsoft.com/enus/azure/bastion/bastion-overview https://docs.microsoft.com/en-us/azure/¦rewall/features https://docs.microsoft.com/en-us/azure/virtualnetwork/network-security-groups-overview
1/9/22, 3:05 PM SC-900 Exam – Free Actual Q&As, Page 12 | ExamTopics
https://www.examtopics.com/exams/microsoft/sc-900/view/12/ 3/3
` Next Questions a
- Expert Veri¦ed, Online, Free.
� Custom View Settings
Question #49 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Microsoft Azure Sentinel is a scalable, cloud-native, security information event management (SIEM) and security orchestration automated
response (SOAR) solution.
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/overview
Question #50 Topic 1
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Box 1: Yes -
Azure Defender provides security alerts and advanced threat protection for virtual machines, SQL databases, containers, web applications, your
network, your storage, and more
Box 2: Yes -
Cloud security posture management (CSPM) is available for free to all Azure users.
Box 3: Yes -
Azure Security Center is a uni¦ed infrastructure security management system that strengthens the security posture of your data centers, and
provides advanced threat protection across your hybrid workloads in the cloud - whether they're in Azure or not - as well as on premises.
Reference:
https://docs.microsoft.com/en-us/azure/security-center/azure-defender https://docs.microsoft.com/en-us/azure/security-center/defender-forstorage-introduction https://docs.microsoft.com/en-us/azure/security-center/security-center-introduction
Question #51 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender/threat-analytics?view=o365-worldwide
Question #52 Topic 1
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
You can use an Azure network security group to ¦lter network tra¨c to and from Azure resources in an Azure virtual network. A network
security group contains security rules that allow or deny inbound network tra¨c to, or outbound network tra¨c from, several types of Azure
resources. For each rule, you can specify source and destination, port, and protocol.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
` Next Questions a
1/9/22, 3:13 PM SC-900 Exam – Free Actual Q&As, Page 14 | ExamTopics
https://www.examtopics.com/exams/microsoft/sc-900/view/14/ 1/3
- Expert Veri¦ed, Online, Free.
� Custom View Settings
Question #53 Topic 1
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Reference:
https://docs.microsoft.com/en-us/mem/intune/fundamentals/what-is-intune https://docs.microsoft.com/enus/mem/intune/fundamentals/what-is-device-management
1/9/22, 3:13 PM SC-900 Exam – Free Actual Q&As, Page 14 | ExamTopics
https://www.examtopics.com/exams/microsoft/sc-900/view/14/ 2/3
Question #54 Topic 1
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Reference:
https://docs.microsoft.com/en-us/azure/bastion/bastion-overview https://docs.microsoft.com/en-us/azure/bastion/tutorial-create-host-portal
1/9/22, 3:13 PM SC-900 Exam – Free Actual Q&As, Page 14 | ExamTopics
https://www.examtopics.com/exams/microsoft/sc-900/view/14/ 3/3
Question #55 Topic 1
What feature in Microsoft Defender for Endpoint provides the ¦rst line of defense against cyberthreats by reducing the attack surface?
A. automated remediation
B. automated investigation
C. advanced hunting
D. network protection
Network protection helps protect devices from Internet-based events. Network protection is an attack surface reduction capability.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/network-protection?view=o365-worldwide
Question #56 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/overview
` Next Questions a
- Expert Veri¦ed, Online, Free.
� Custom View Settings
Question #57 Topic 1
Which two types of resources can be protected by using Azure Firewall? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. Azure virtual machines Most Voted
B. Azure Active Directory (Azure AD) users
C. Microsoft Exchange Online inboxes
D. Azure virtual networks Most Voted
E. Microsoft SharePoint Online sites
Question #58 Topic 1
You plan to implement a security strategy and place multiple layers of defense throughout a network infrastructure.
Which security methodology does this represent?
A. threat modeling
B. identity as the security perimeter
C. defense in depth
D. the shared responsibility model
C @
Reference:
https://docs.microsoft.com/en-us/learn/modules/secure-network-connectivity-azure/2-what-is-defense-in-depth
Question #59 Topic 1
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Question #60 Topic 1
What can you use to scan email attachments and forward the attachments to recipients only if the attachments are free from malware?
A. Microsoft Defender for O¨ce 365
B. Microsoft Defender Antivirus
C. Microsoft Defender for Identity
D. Microsoft Defender for Endpoint
Reference:
https://docs.microsoft.com/en-us/o¨ce365/servicedescriptions/o¨ce-365-advanced-threat-protection-service-description
` Next Questions a
- Expert Veri¦ed, Online, Free.
� Custom View Settings
Question #61 Topic 1
Which feature provides the extended detection and response (XDR) capability of Azure Sentinel?
A. integration with the Microsoft 365 compliance center
B. support for threat hunting
C. integration with Microsoft 365 Defender
D. support for Azure Monitor Workbooks
Reference:
https://docs.microsoft.com/en-us/microsoft-365/security/defender/eval-overview?view=o365-worldwide
Question #62 Topic 1
What can you use to provide threat detection for Azure SQL Managed Instance?
A. Microsoft Secure Score
B. application security groups
C. Azure Defender
D. Azure Bastion
Question #63 Topic 1
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Question #64 Topic 1
Which Azure Active Directory (Azure AD) feature can you use to restrict Microsoft Intune-managed devices from accessing corporate resources?
A. network security groups (NSGs)
B. Azure AD Privileged Identity Management (PIM)
C. conditional access policies
D. resource locks
` Next Questions a
1/9/22, 3:24 PM SC-900 Exam – Free Actual Q&As, Page 17 | ExamTopics
https://www.examtopics.com/exams/microsoft/sc-900/view/17/ 1/3
- Expert Veri¦ed, Online, Free.
� Custom View Settings
Question #65 Topic 1
Which two tasks can you implement by using data loss prevention (DLP) policies in Microsoft 365? Each correct answer presents a complete
solution.
NOTE: Each correct selection is worth one point.
A. Display policy tips to users who are about to violate your organization€™גs policies.
B. Enable disk encryption on endpoints.
C. Protect documents in Microsoft OneDrive that contain sensitive information.
D. Apply security baselines to devices.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/dlp-learn-about-dlp?view=o365-worldwide
Question #66 Topic 1
HOTSPOT -
Select the answer that correctly completes the sentence.
Hot Area:
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-score-calculation?view=o365-worldwide#how-compliance-managercontinuously- assesses-controls
1/9/22, 3:24 PM SC-900 Exam – Free Actual Q&As, Page 17 | ExamTopics
https://www.examtopics.com/exams/microsoft/sc-900/view/17/ 2/3
Question #67 Topic 1
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Box 1: Yes -
You can use sensitivity labels to provide protection settings that include encryption of emails and documents to prevent unauthorized people
from accessing this data.
Box 2: Yes -
You can use sensitivity labels to mark the content when you use O¨ce apps, by adding watermarks, headers, or footers to documents that have
the label applied.
Box 3: Yes -
You can use sensitivity labels to mark the content when you use O¨ce apps, by adding headers, or footers to email that have the label applied.
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels?view=o365-worldwide
Question #68 Topic 1
Which Microsoft 365 compliance feature can you use to encrypt content automatically based on speci¦c conditions?
A. Content Search
B. sensitivity labels
C. retention policies
D. eDiscovery
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/information-protection?view=o365-worldwide
1/9/22, 3:24 PM SC-900 Exam – Free Actual Q&As, Page 17 | ExamTopics
https://www.examtopics.com/exams/microsoft/sc-900/view/17/ 3/3
` Next Questions a
- Expert Veri¦ed, Online, Free.
� Custom View Settings
Question #69 Topic 1
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Box 1: No -
Compliance Manager tracks Microsoft managed controls, customer-managed controls, and shared controls.
Box 2: Yes -
Box 3: Yes -
Reference:
https://docs.microsoft.com/en-us/microsoft-365/compliance/compliance-manager?view=o365-worldwide
Question #70 Topic 1
HOTSPOT -
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Reference:
https://docs.microsoft.com/en-us/azure/governance/policy/overview
Question #71 Topic 1
What is a use case for implementing information barrier policies in Microsoft 365?
A. to restrict unauthenticated access to Microsoft 365
B. to restrict Microsoft Teams chats between certain groups within an organization Most Voted
C. to restrict Microsoft Exchange Online email between certain groups within an organization
D. to restrict data sharing to external email recipients
[Show More]
Last updated: 5 months ago
Preview 6 out of 60 pages


.png)















.png)
.png)
.png)
.png)
.png)
.png)
.png)