Business Law > QUESTIONS & ANSWERS > Chapter 9 Criminal Law and Cyber Crime. All Answers (All)
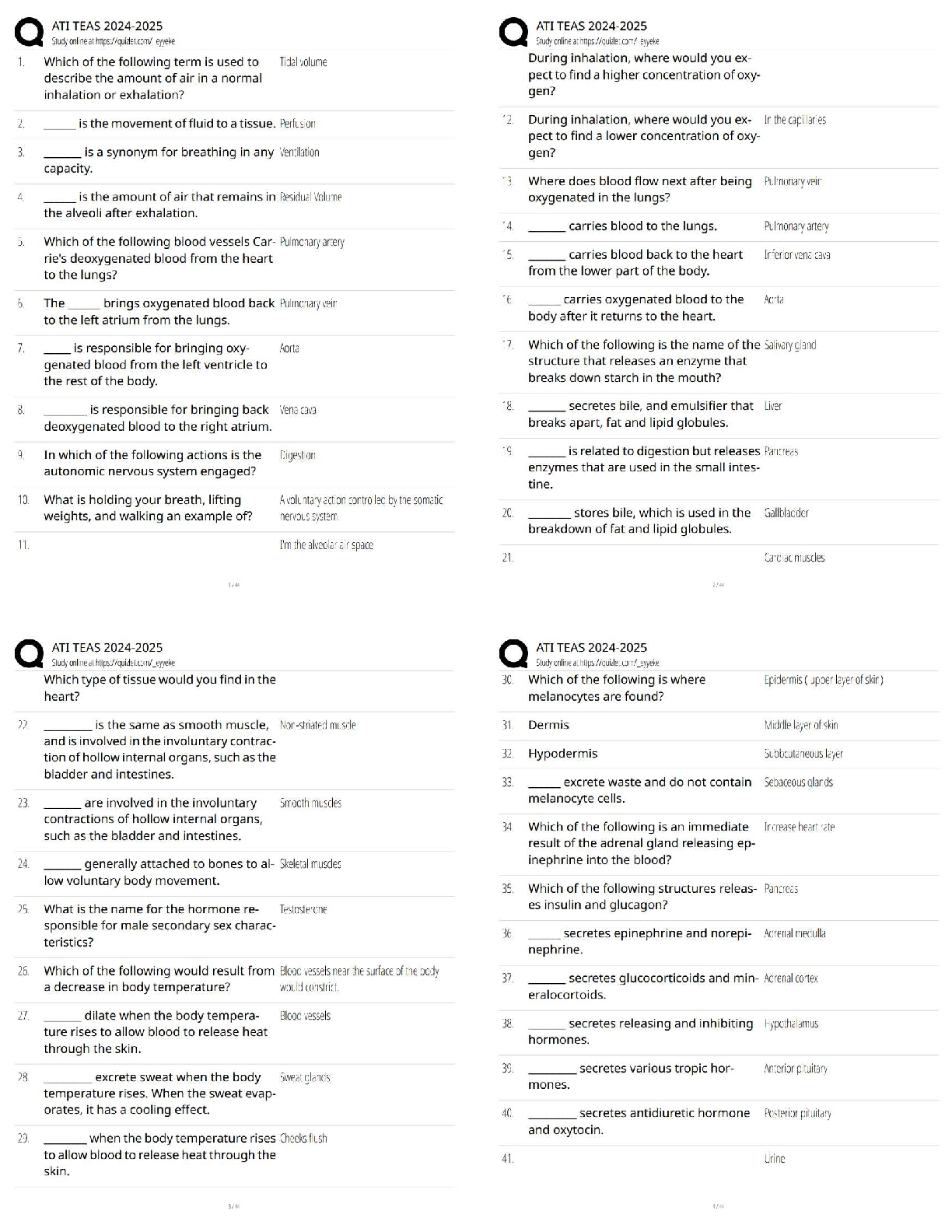
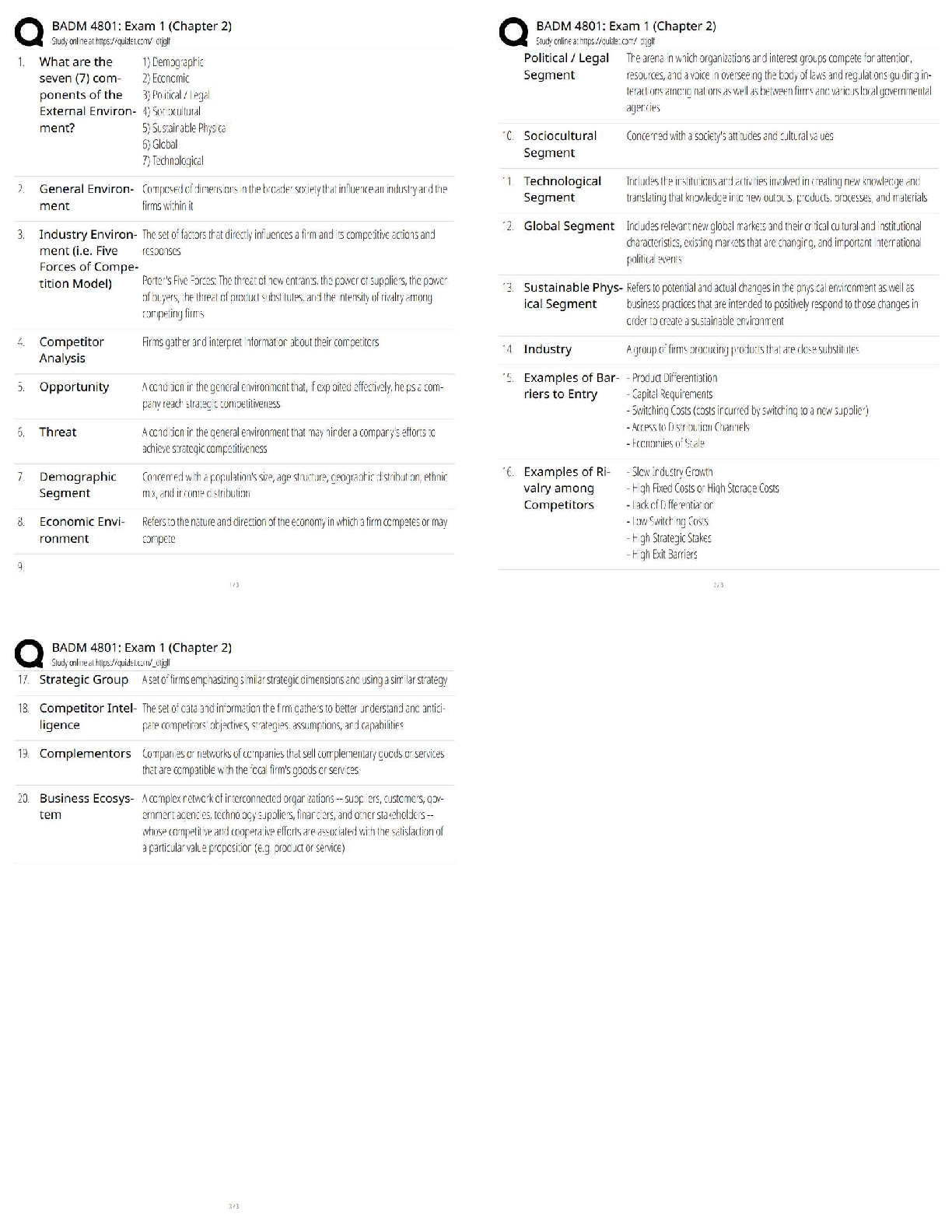
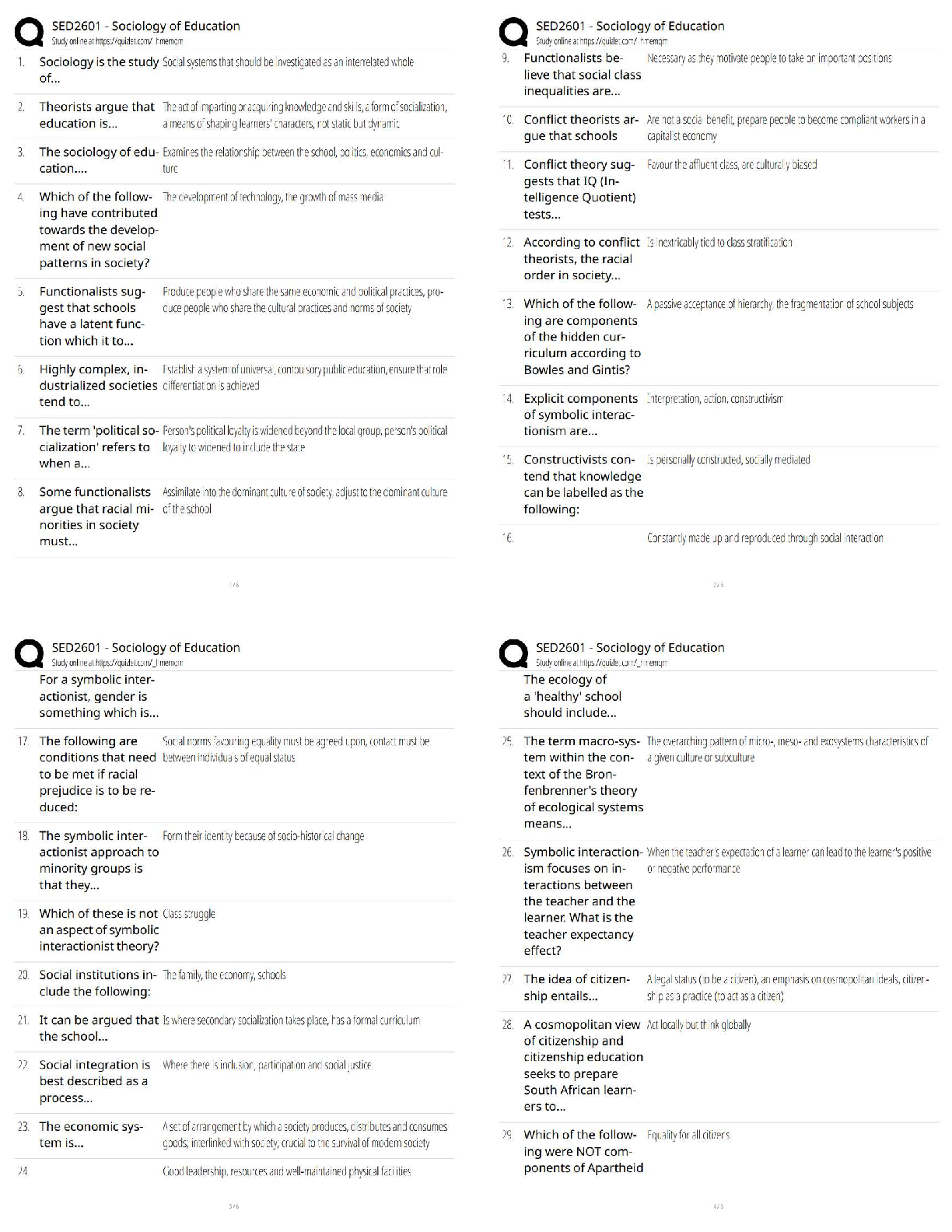
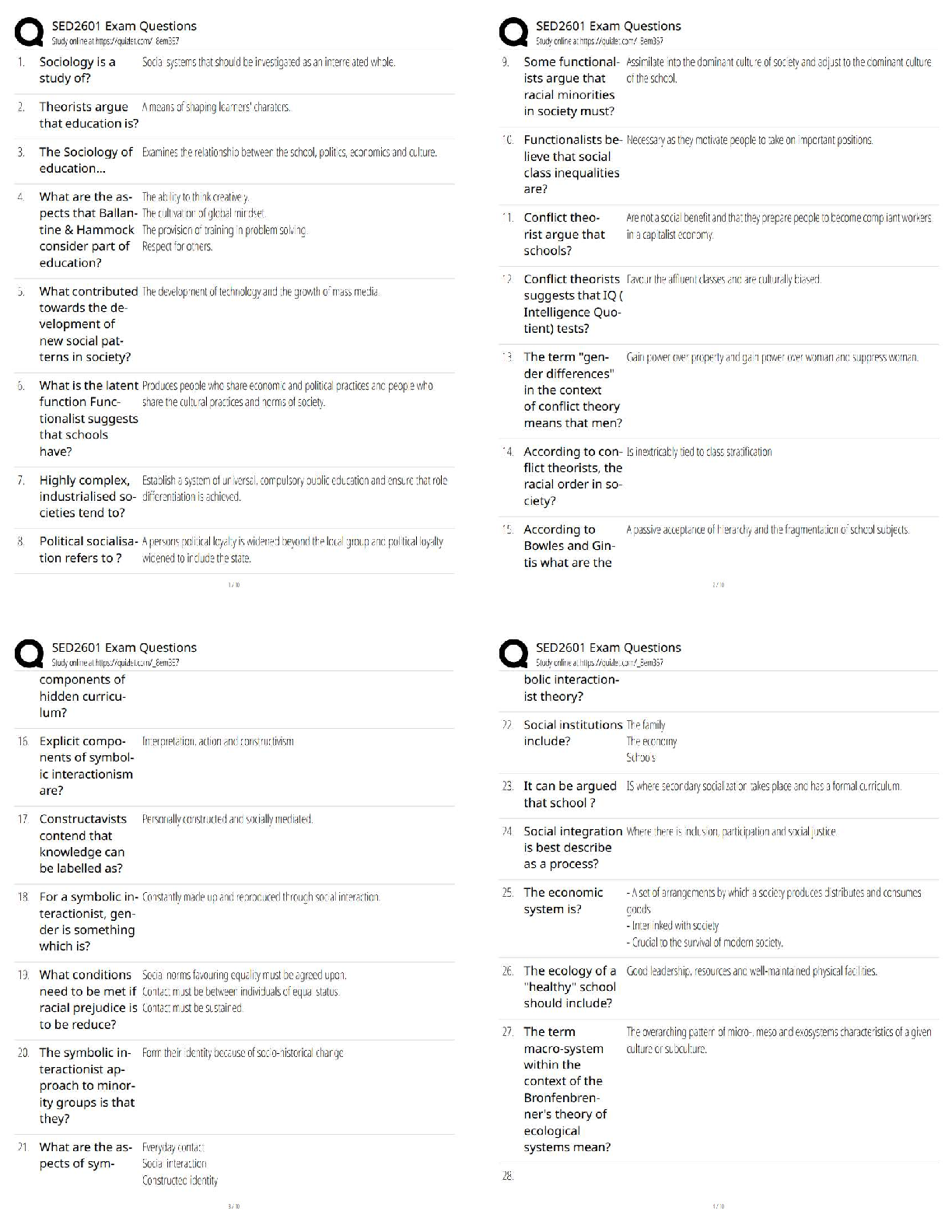
Chapter 9 Criminal Law and Cyber Crime. All Answers
Document Content and Description Below
Chapter 9 Criminal Law and Cyber Crime N.B.: TYPE indicates that a question is new, modified, or unchanged, as follows. N A question new to this edition of the Test Bank. + A questi ... on modified from the previous edition of the Test Bank. = A question included in the previous edition of the Test Bank. A1. A misdemeanor is a crime punishable only by a fine. F 175 TYPE: N NAT: AACSB Analytic AICPA Legal A2. Thinking about killing someone constitutes the crime of attempted murder. F 176 TYPE: N NAT: AACSB Reflective AICPA Legal A3. A wrongful mental state is typically required for criminal liability. T 177 TYPE: N NAT: AACSB Analytic AICPA Legal A4. Picking pockets is not robbery. T 178 TYPE: N NAT: AACSB Reflective AICPA Legal A5. A person who commits larceny can be sued under tort law. T 178 TYPE: N NAT: AACSB Reflective AICPA Legal A6. It may be a crime to take another’s property, but it is not a crime to receive stolen goods. F 179 TYPE: N NAT: AACSB Analytic AICPA Legal A7. Changing a trademark is forgery. T 179 TYPE: N NAT: AACSB Analytic AICPA Legal A8. A person’s intent to return embezzled property is a defense to the crime of embezzlement. F 180 TYPE: N NAT: AACSB Analytic AICPA Legal A9. A kickback for a special favor or service is not considered a bribe. F 182 TYPE: N NAT: AACSB Reflective AICPA Legal A10. A defendant may be relieved of liability by showing that a criminal act was necessary to prevent an even greater harm. T 186 TYPE: N NAT: AACSB Analytic AICPA Legal A11. Ordinarily, “ignorance of the law is an excuse,” or a valid defense to criminal liability. F 186 TYPE: N NAT: AACSB Analytic AICPA Legal A12. A suspect cannot be tried twice in the same court for the same crime. T 187 TYPE: N NAT: AACSB Analytic AICPA Legal A13. The purpose of the exclusionary rule is to encourage criminals to provide exclusive evidence of their crimes. F 188 TYPE: N NAT: AACSB Analytic AICPA Legal A14. Any crime that requires knowledge of computer technology for its investigation is a computer crime. T 193 TYPE: N NAT: AACSB Analytic AICPA Legal A15. Most cyber crimes are “new” crimes. F 193 TYPE: N NAT: AACSB Analytic AICPA Legal A16. It is not identity theft to use a fabricated identity to access financial resources online. F 194 TYPE: N NAT: AACSB Analytic AICPA Legal A17. Dishing is phishing that involves voice communication. T 194 TYPE: N NAT: AACSB Analytic AICPA Legal A18. A stolen credit card is more likely to hurt a consumer than a merchant. F 195 TYPE: N NAT: AACSB Reflective AICPA Legal A19. A hacker is someone who uses one computer to break into another. T 195 TYPE: N NAT: AACSB Analytic AICPA Legal A20. A cyberterrorist might target a government agency, but not a business. F 196 TYPE: N NAT: AACSB Reflective AICPA Risk Analysis MULTIPLE CHOICE QUESTIONS A1. Gail is a “payday” lender charged with filing false claims in bankruptcy proceedings against her debtors. The standard of proof to find a defendant who has been charged with a crime guilty is a. a preponderance of the evidence. b. beyond all doubt. c. beyond a reasonable doubt. d. clear and convincing evidence. C 174 TYPE: = NAT: AACSB Reflective AICPA Legal A2. Domino causes a disturbance at El Nino Cafe. He is arrested and charged with disorderly conduct, a misdemeanor. A misdemeanor is a crime punish-able by a. a fine only. b. imprisonment up to one year. c. imprisonment up to six months. d. imprisonment up to ten days. B 175 TYPE: + NAT: AACSB Reflective AICPA Legal A3. Plato works for Quirky Squirters, Inc. During work hours, Plato “steals” his employer’s computer time to start up his own business, Rowdy Drenchers. This is a. burglary. b. robbery. c. larceny. d. no crime. C 178 TYPE: N NAT: AACSB Reflective AICPA Legal A4. Rock pushes Sylvia to the ground, grabbing her purse as she falls. The use of force or fear is required for this act to constitute a. burglary. b. forgery. c. larceny. d. robbery. D 178 TYPE: = NAT: AACSB Reflective AICPA Legal A5. Ivan signs Jeb’s name, without his authorization, to the back of a check. This is a. no crime. b. forgery. c. larceny. d. robbery. B 179 TYPE: + NAT: AACSB Reflective AICPA Legal A6. Sven receives an MP3 player stolen from Tomas. To be criminally liable, Sven must know a. the player is stolen. b. Tomas is the true owner. c. how to operate an MP3 player. d. what an MP3 player is. A 179 TYPE: + NAT: AACSB Reflective AICPA Legal A7. Riley, a Sterling Bank employee, deposits into his account checks that are given to him by bank customers to deposit into their accounts. This is a. burglary. b. embezzlement. c. larceny. d. money laundering. B 179 TYPE: = NAT: AACSB Reflective AICPA Legal A8. Mona offers Ned, a building inspector, money to overlook the violations in her new warehouse. Ned accepts the money and overlooks the viola¬tions. Mona is charged with the crime of bribery. The crime occurred when a. Mona decided to offer the bribe. b. Mona offered the bribe. c. Ned accepted the bribe. d. Ned overlooked the violations. B 182 TYPE: = NAT: AACSB Reflective AICPA Legal A9. Cameron manages an illegal gambling operation in his BBQ Bar & Grill. Cameron reports the profits of the gambling operation as income from BBQ’s legitimate activities on its tax returns. This is a. embezzlement. b. larceny. c. money laundering. d. no crime. C 184 TYPE: = NAT: AACSB Reflective AICPA Legal A10. Davis points a gun at Eton, threatening to shoot him if he does not steal from his employer, Freddy’s Convenience Store, and give the stolen funds to Davis. Charged with theft, Eton can successfully claim, as a defense a. nothing. b. duress. c. entrapment. d. self-defense. B 187 TYPE: + NAT: AACSB Reflective AICPA Legal A11. Vance points a gun at Workman, threatening to shoot him. Workman hits Vance, causing his death. Charged with homicide, Workman can successfully claim as a defense a. nothing. b. duress. c. entrapment. d. self-defense. D 187 TYPE: + NAT: AACSB Reflective AICPA Legal A12. Ollie, an employee of Payroll Management Corporation, is arrested at work. A grand jury issues a formal charge against Ollie for larceny. This charge is a. an arraignment. b. an indictment. c. an information. d. an inquisition. B 192 TYPE: = NAT: AACSB Reflective AICPA Legal A13. Jean sends e-mail to Irwin promising a percentage of the amount in an African bank account for assistance in transferring the funds to a U.S. bank account. Irwin forwards his account number, but the funds are never sent. Instead, Jean quickly withdraws the funds in Irwin’s account. This is a. online greed but not fraud. b. an online “fool-me-once, shame on you” occurrence but not fraud. c. online gambling but not fraud. d. online fraud. D 193 TYPE: N NAT: AACSB Reflective AICPA Legal A14. Harvey puts up a guitar for bids on eWay, a Web auction site. Faith makes the highest bid and sends the payment, which Harvey receives, but he does not send the guitar to her. This is online a. auction fraud. b. puffery. c. retail fraud. d. frustration but not fraud. A 194 TYPE: N NAT: AACSB Reflective AICPA Legal A15. Posing as Platinum Bank, Oswald e-mails Nadia, asking her to update her personal banking information through a link in the e-mail. She clicks on the link and types in the data, which Oswald promptly sells to Moe. This is a. no crime. b. employment fraud. c. phishing. d. vishing. C 194 TYPE: N NAT: AACSB Reflective AICPA Legal Fact Pattern 9-1 (Questions A16–A17 apply) Minka uses her computer to secretly install software on hundreds of personal computers without their owners’ knowledge. A16. Refer to Fact Pattern 9-1. Minka’s secretly installed software allows her to forward transmissions from her unauthorized network to even more systems. This network is a. a hacker. b. a bot. c. a botnet. d. a worm. C 195 TYPE: N NAT: AACSB Reflective AICPA Legal A17. Refer to Fact Pattern 9-1. Minka’s software is harmful to the computers on which she installed it. This program is a. malware. b. badware. c. harmware. d. infectware. A 195 TYPE: N NAT: AACSB Reflective AICPA Legal A18. Posing as a representative of Global Games Company, Ferris e-mails Evan, a job seeker, asking him to forward personal banking information so that if he is hired, payroll checks can be deposited directly into his account. Evan supplies the data, which Ferris promptly sells to Dixie. This is a. no crime. b. employment fraud. c. phishing. d. vishing. B 195 TYPE: N NAT: AACSB Reflective AICPA Legal A19. Via the Internet, Rocky sabotages the computer system of Quik Chik’n Company, a food manufacturer, with the purpose of altering the levels of ingredients of the company’s products so that consumers of the food become ill. Rocky is a. a cyberterrorist. b. a botnet. c. a virus. d. a worm. A 196 TYPE: N NAT: AACSB Reflective AICPA Legal A20. Rashad accesses Quant Company’s computer system without authority to obtain protected financial data. Under federal law, this is a. a felony if it is committed for a commercial purpose. b. a felony if Quant brings a civil suit against Rashad. c. not a crime. d. a crime, but not a felony. A 196 TYPE: N NAT: AACSB Reflective AICPA Legal ESSAY QUESTIONS A1. Sophie is the president of Tasty Foods Corporation, a wholesale grocery company. An inspection by Uri, a government agent, uncovers unsani¬tary conditions caused by Vic, a Tasty Foods employee, in the company’s ware-house. Will, a Tasty Foods vice president, assures Uri that the situation will be corrected, but a later inspection reveals no such corrections. Sophie knows nothing about any of this. Can Tasty Foods be convicted of a crime in these circumstances? Can Sophie be held personally liable? A2. Good Health & Life Insurance Corporation suffers a security breach in its computer network. Before the company discovers the breach, the perpetrator obtains corporate financial records and other confidential data, including marketing plans. Is this a crime? If so, what are its elements? What steps might Good Health & Life take to ensure that going forward only authorized users access the data on its computers? Whose efforts—those of the federal government or Good Health & Life—are most important in securing the company’s computer infrastructure and why? [Show More]
Last updated: 3 years ago
Preview 1 out of 18 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$7.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Dec 08, 2019
Number of pages
18
Written in
All
Additional information
This document has been written for:
Uploaded
Dec 08, 2019
Downloads
0
Views
198





.png)
.png)
.png)
.png)
.png)