University of the Cumberlands EMISS ISOL532 Telecommunications and network security. Lab 10 Assessment Quiz. 20 Q&A
Document Content and Description Below
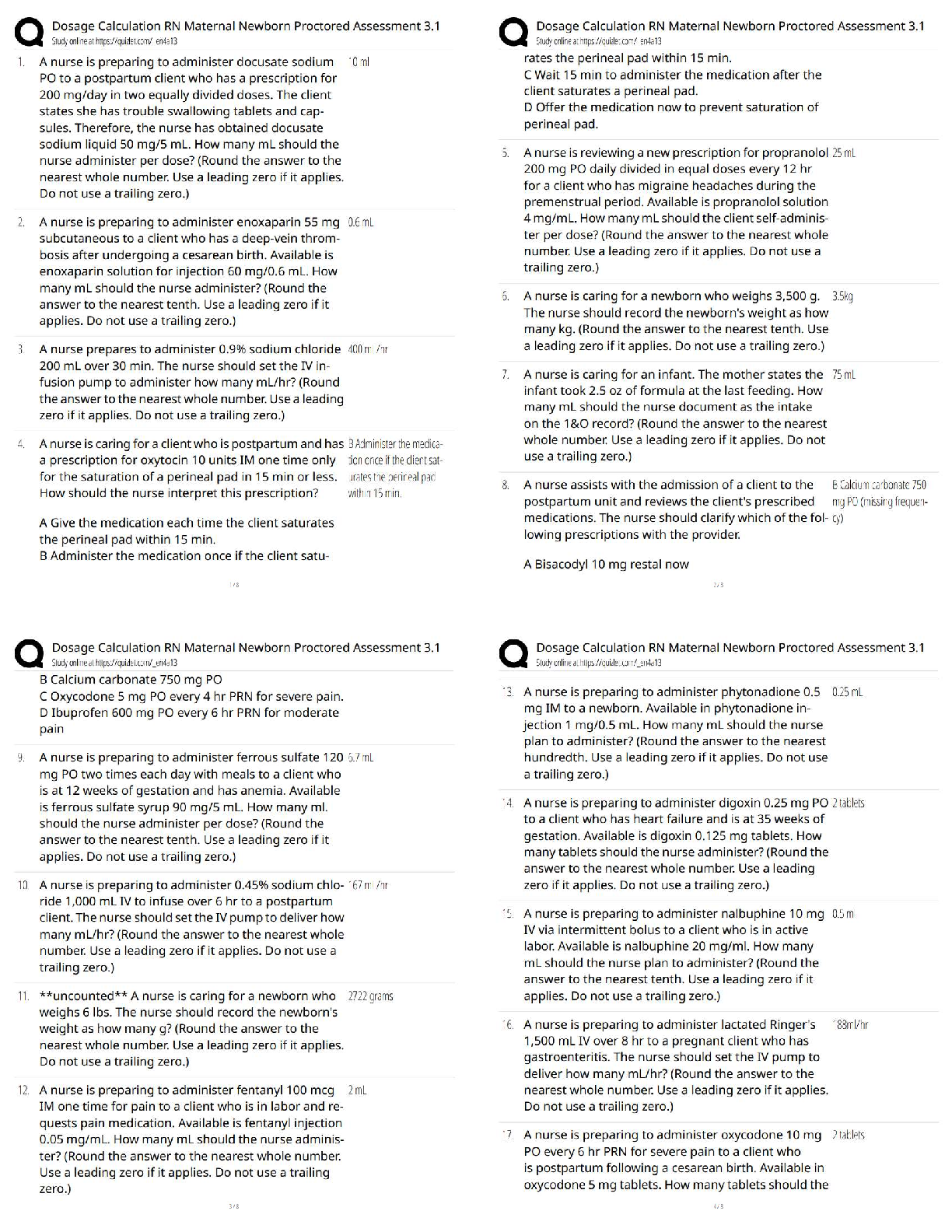
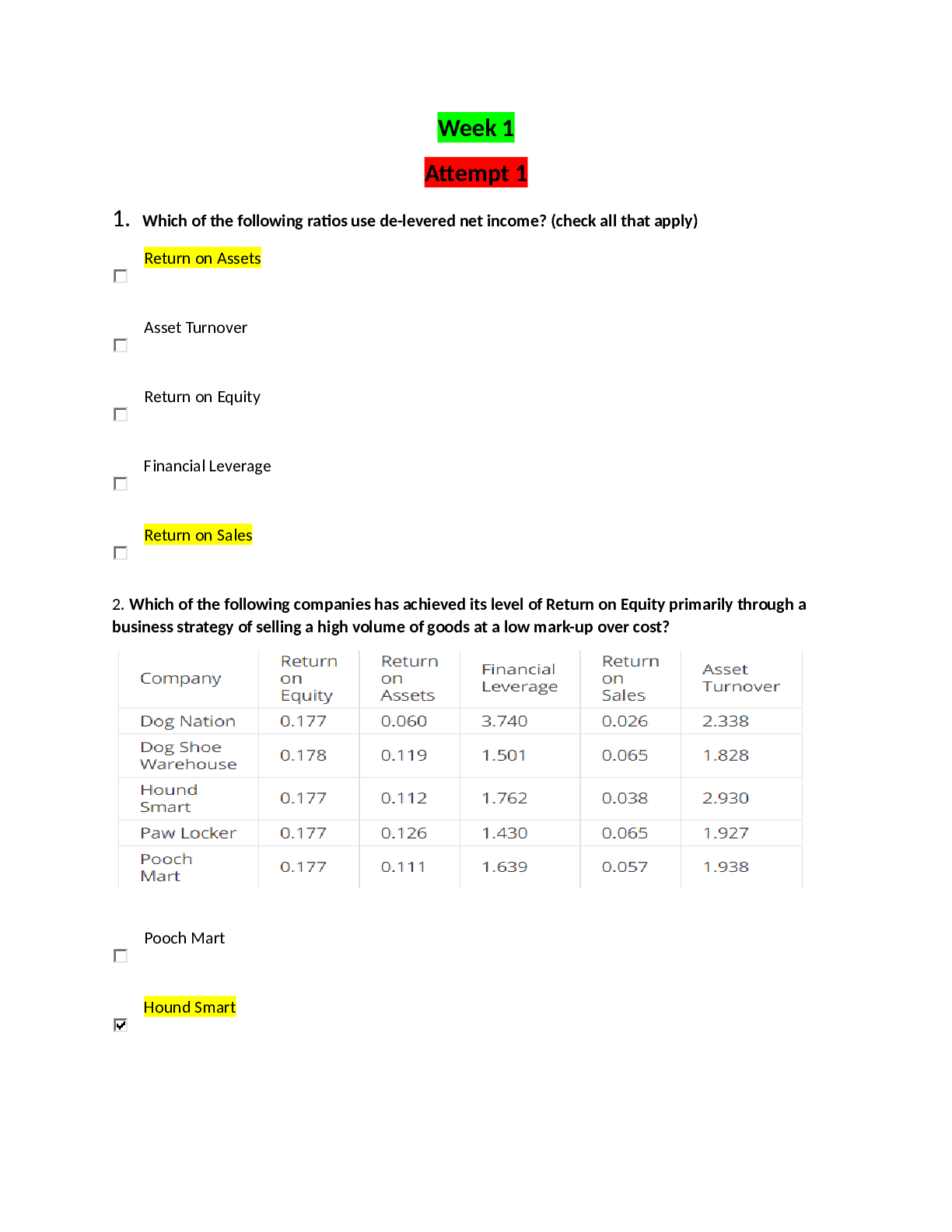
QUESTION 1
1. Microsoft Baseline Security Analyzer (MBSA) is a system scanning tool
that scans workstations and servers running:
any operating system.
Linux.
Windows.
Linux, Apple OS X, or
Wind
...
ows.
5.00000 points
QUESTION 2
1. Microsoft Baseline Security Analyzer (MBSA) is a:
system configuration
tool.
system information
tool.
system administration
tool.
system analysis tool.
5.00000 points
QUESTION 3
1. Processes, Performance, Users, Details, and Services are the five types
of system information that can be obtained from the:
Windows Task Manager.
Windows Desktop.
Windows Event Viewer.
Microsoft Baseline Security Analyzer
(MBSA).
5.00000 points
QUESTION 4
1. The five-step formula that serves as the basis for incident response
processes and procedures includes:
accept, adjust, adapt, acclimate, and relate to security
incidents.
refute, deter, discourage, defend, and correct security
incidents.
identify, research, reject, process, and detail security
incidents.
prevent, detect, respond, control, and document
security incidents.
5.00000 points
QUESTION 5
1. What types of automated tools are used to scan an operating system
and key software applications for security issues?
System configuration
tools
System information
tools
System administration
tools
System analysis tools
5.00000 points
QUESTION 6
1. What types of automated tools provide information about the current
operating state of a computer system?
System configuration
tools
System information
tools
System administration
tools
System analysis tools
5.00000 points
QUESTION 7
1. Which Windows log contains information about system security status?
The Setup Log
The Security Log
The Application
Log
The System Log
5.00000 points
QUESTION 8
1. Which Windows log contains information about system startup,
shutdown, and status changes for key system processes?
The Setup Log
The Security Log
The Application
Log
The System Log
5.00000 points
QUESTION 9
1. Which Windows log records information about events, including
successful operations, system warnings, error messages about failed
operations, and information about both successful and unsuccessful logon
attempts?
The Setup Log
The Security Log
The Application
Log
The System Log
5.00000 points
QUESTION 10
1. Which of the following provides brief descriptions of services and their
statuses and also provides the name and process ID (PID) for each service
that is running?
Microsoft Baseline Security Analyzer
(MBSA)
Windows Application Manager
Windows Computer Management
Windows Task Manager
5.00000 points
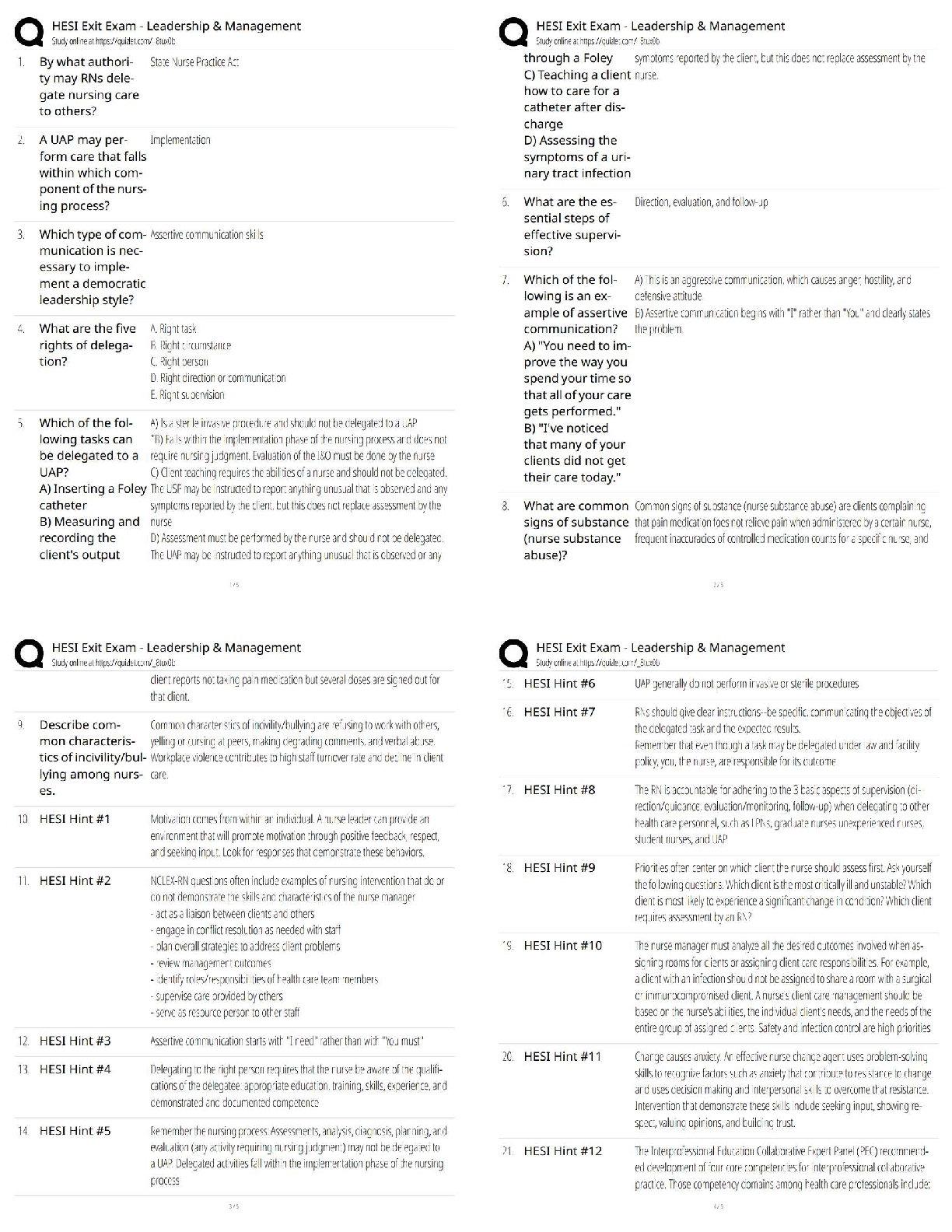
QUESTION 11
1. Which of the following provides detailed information about each
service and also provides the startup type (automatic, automatic/delayed
start, disabled, manual) and logon information (logon as local service, local
system, and network service)?
Microsoft Baseline Security Analyzer
(MBSA)
Windows Application Manager
Windows Computer Management
Windows Task Manager
5.00000 points
QUESTION 12
1. Which of the following statements is true regarding Microsoft Baseline
Security Analyzer (MBSA)?
In the lab, you used MBSA to scan Internet Explorer and Microsoft Office
for vulnerabilities.
MBSA can be configured to check for missing updates and recommended
security settings on Linux servers.
Windows Update is more powerful than MBSA because it checks system
and software settings in the registry in addition to checking for required
software updates.
MBSA generates a report that identifies security issues and provides
recommendations for system configuration changes.
5.00000 points
QUESTION 13
1. Which of the following statements is true regarding filtering log files?
Filters should not be used on log files during an investigation into a
security incident.
Most log files are easily scanned by eye when looking for evidence.
Using a filter can help an analyst to quickly find events of interest.
The drawback to using filtering is that it increases the number of
entries.
5.00000 points
QUESTION 14
1. Which of the following statements is true regarding gathering system
performance information?
System performance information supplements information gathered by
automated tools.
It is poor practice for an IT Help Desk to ask an end user to perform any
information gathering tasks.
A support technician should not provide instruction to a user on how to
enable remote desktop services.
A support technician should not use a remote log in to gather information
and run tests on a user’s workstation.
5.00000 points
QUESTION 15
1. Which of the following statements is true regarding remote desktop
services?
Remote desktop services should not be used to gather system
performance information.
Remote desktop services typically cost an organization a significant
amount of time and money.
Remote desktop services typically require several desk-side support visits
by IT Help Desk technicians.
Remote login services can become a vulnerability that is exploited both
internally and externally.
5.00000 points
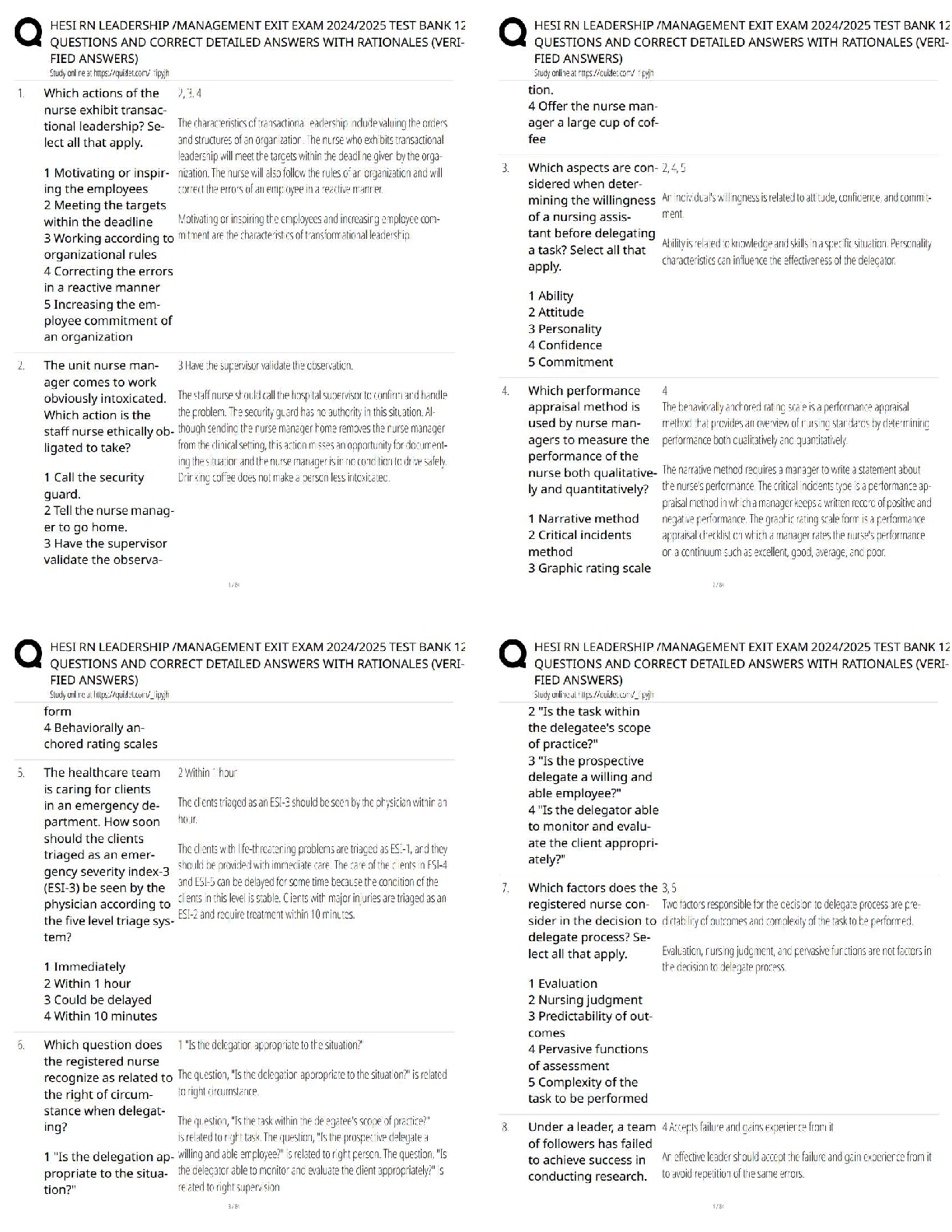
QUESTION 16
1. Which of the following statements is true regarding security incidents?
Security incidents cannot occur when security measures such as firewalls,
properly configured VPNs, and secure network procedures are in place.
Security incidents can arise from a number of sources, including human
error or mistakes.
Deliberate actions that cause loss or harm to the organization are not
considered security incidents.
Organizations must simply learn to live with the impact and associated
costs of security incidents.
5.00000 points
QUESTION 17
1. Which tool checks for system administration and misconfiguration
problems, application software issues including missing patches and
updates, and missing or partially installed system security updates?
Microsoft Baseline Security Analyzer
(MBSA)
Windows Computer Management
Windows 2012
Windows Task Manager
5.00000 points
QUESTION 18
1. Which tool provides detailed information about the system, including
lists of services and their current state, computer hardware configuration,
security and system events, and scheduled tasks?
Microsoft Baseline Security Analyzer
(MBSA)
Windows Computer Management
Windows 2012
Windows Task Manager
5.00000 points
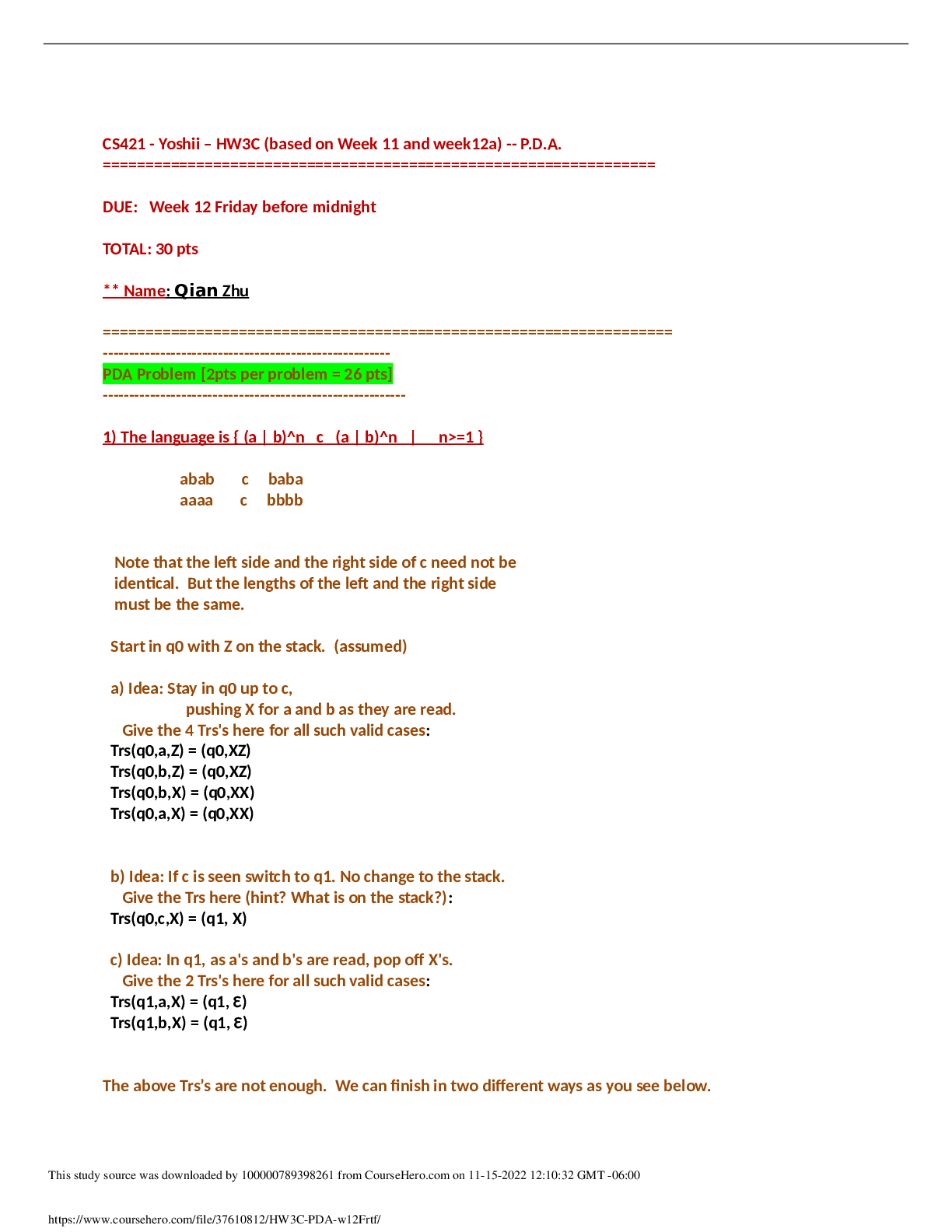
QUESTION 19
1. Which tool provides information about currently running tasks, use of
system resources, and system performance?
Microsoft Baseline Security Analyzer
(MBSA)
Windows Computer Management
Windows 2012
Windows Task Manager
5.00000 points
QUESTION 20
1. Windows Computer Management and Windows Task Manager are what
type of tools?
System configuration
tools
System information
tools
System administration
tools
System analysis tools
[Show More]
Last updated: 3 years ago
Preview 1 out of 6 pages
, Question Answers, Correct , Correct Answers.png)


.png)
.png)








.png)
.png)
.png)
.png)
.png)
.png)
.png)