1. Which weapons of mass destruction do most experts predict terrorists will use?
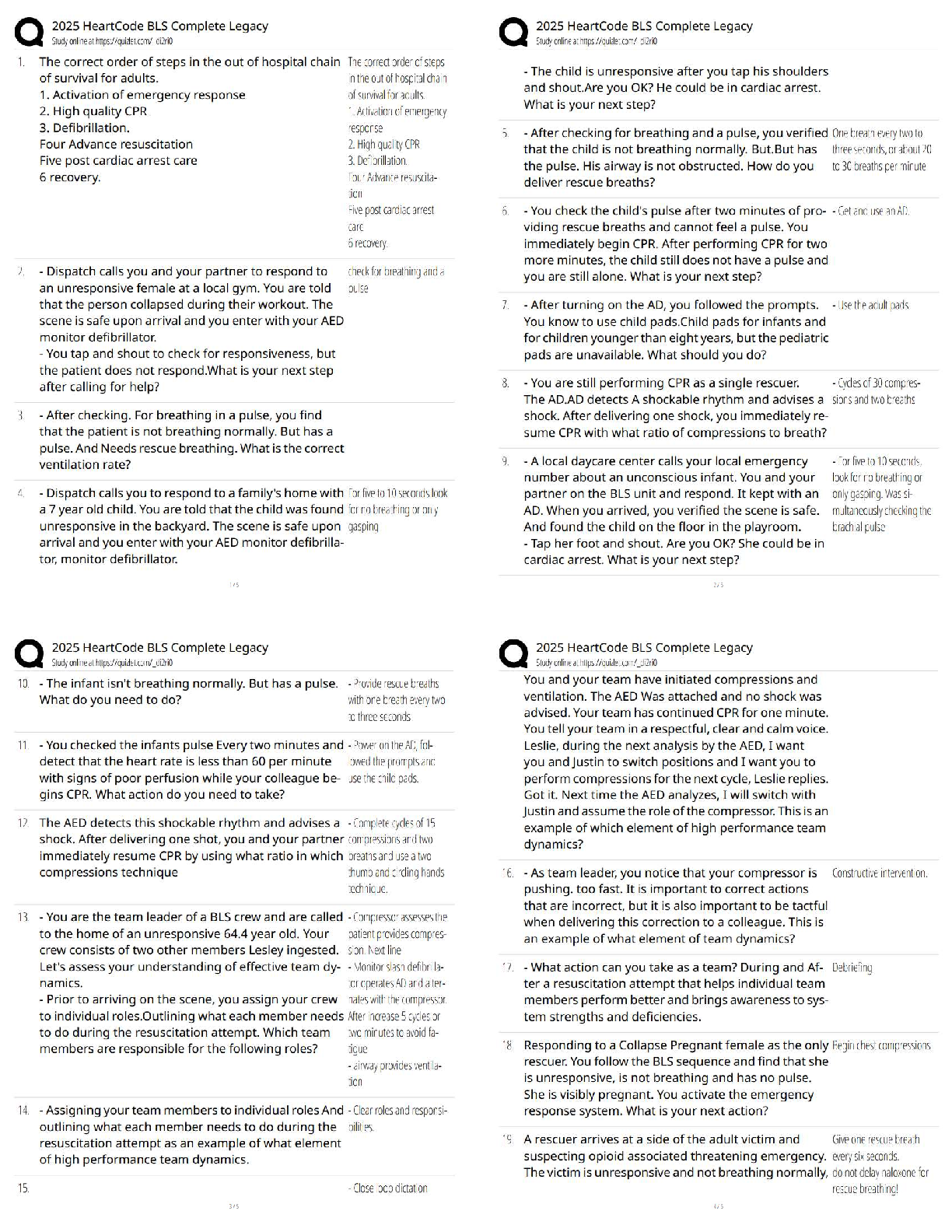
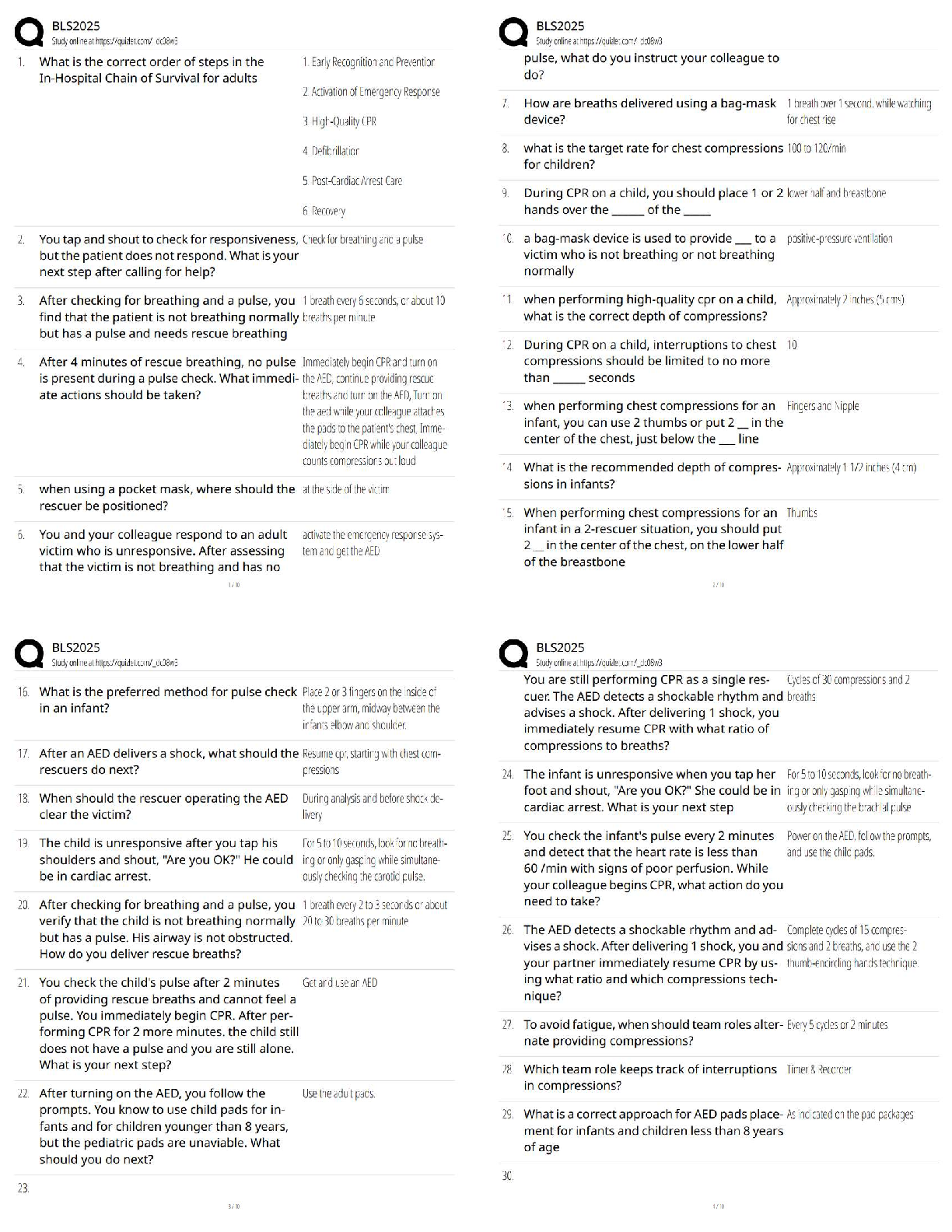
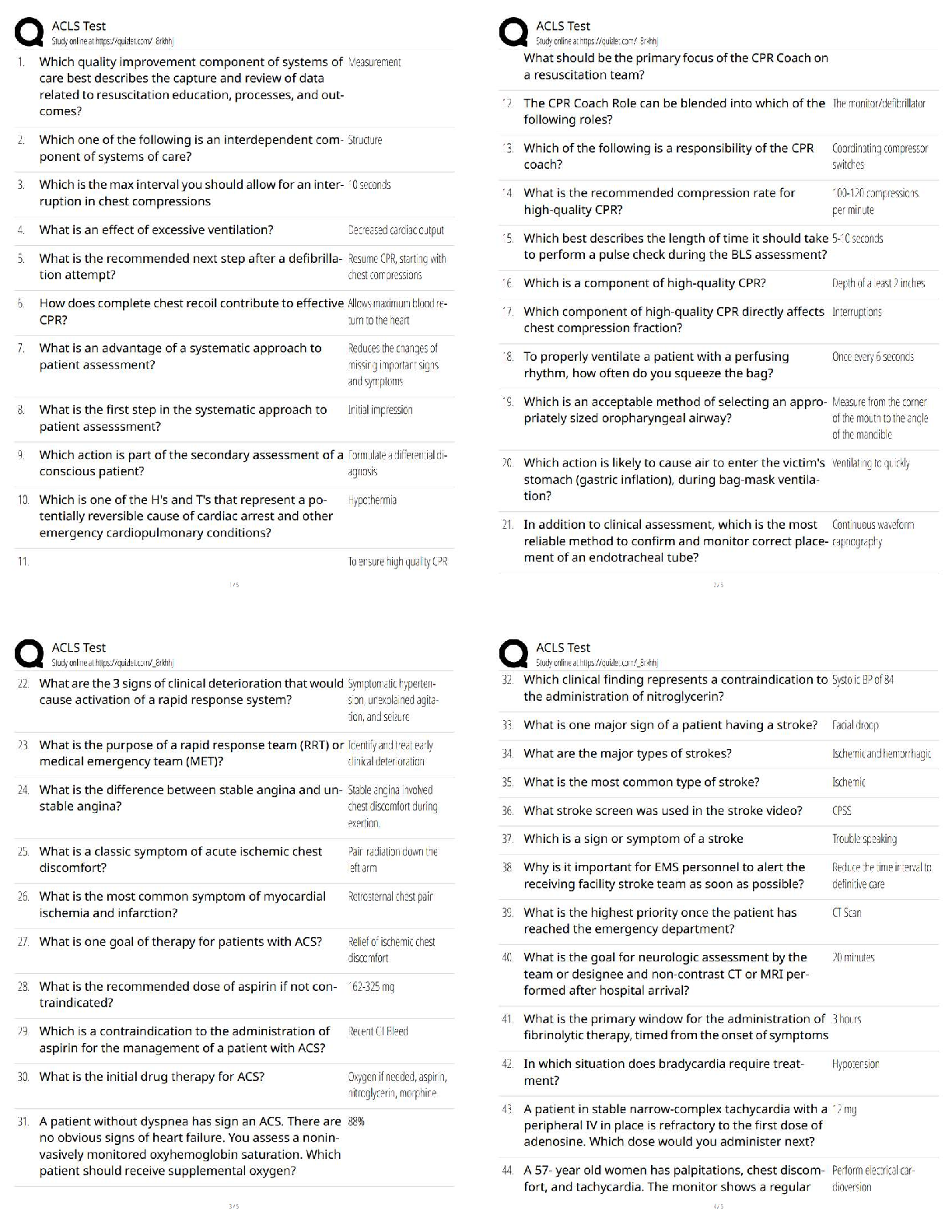
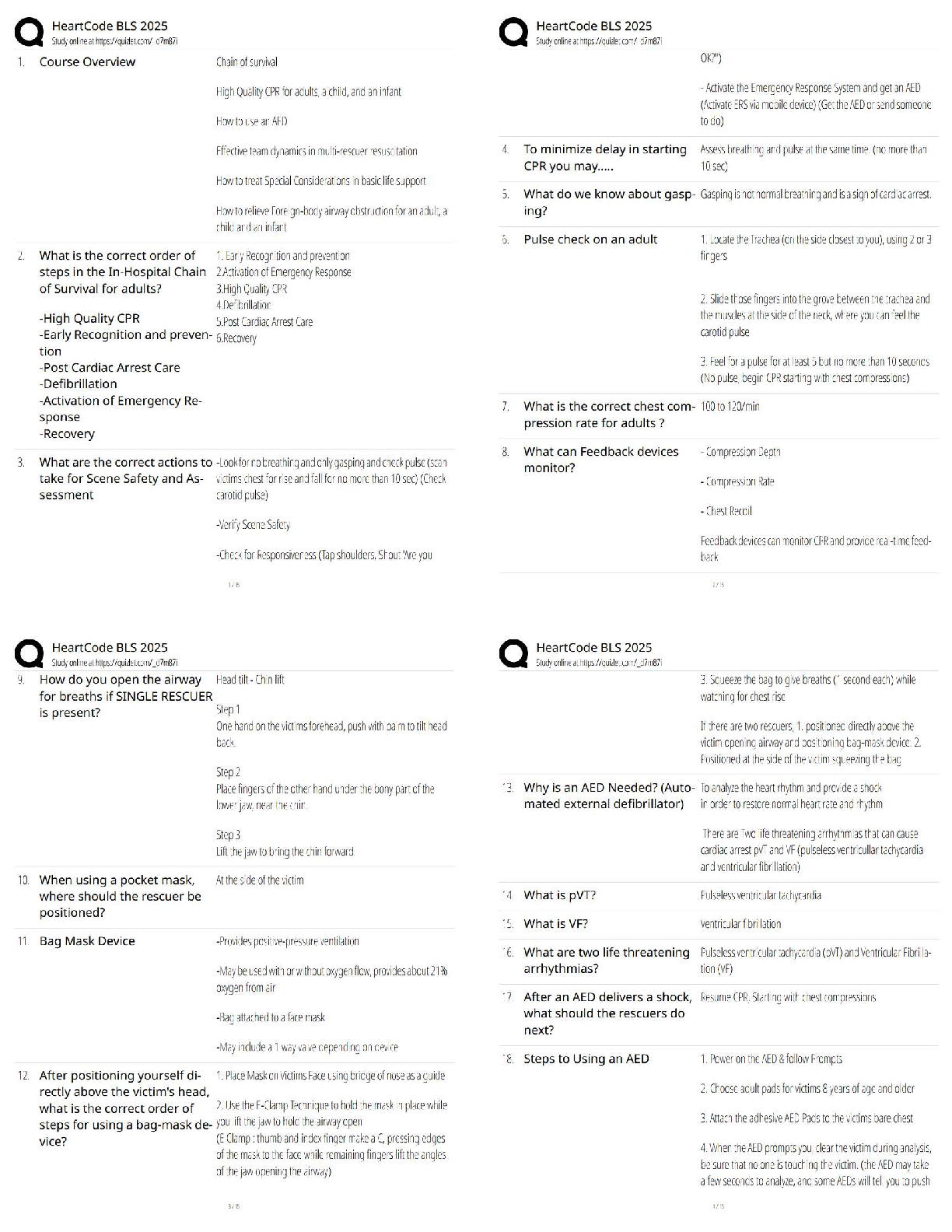
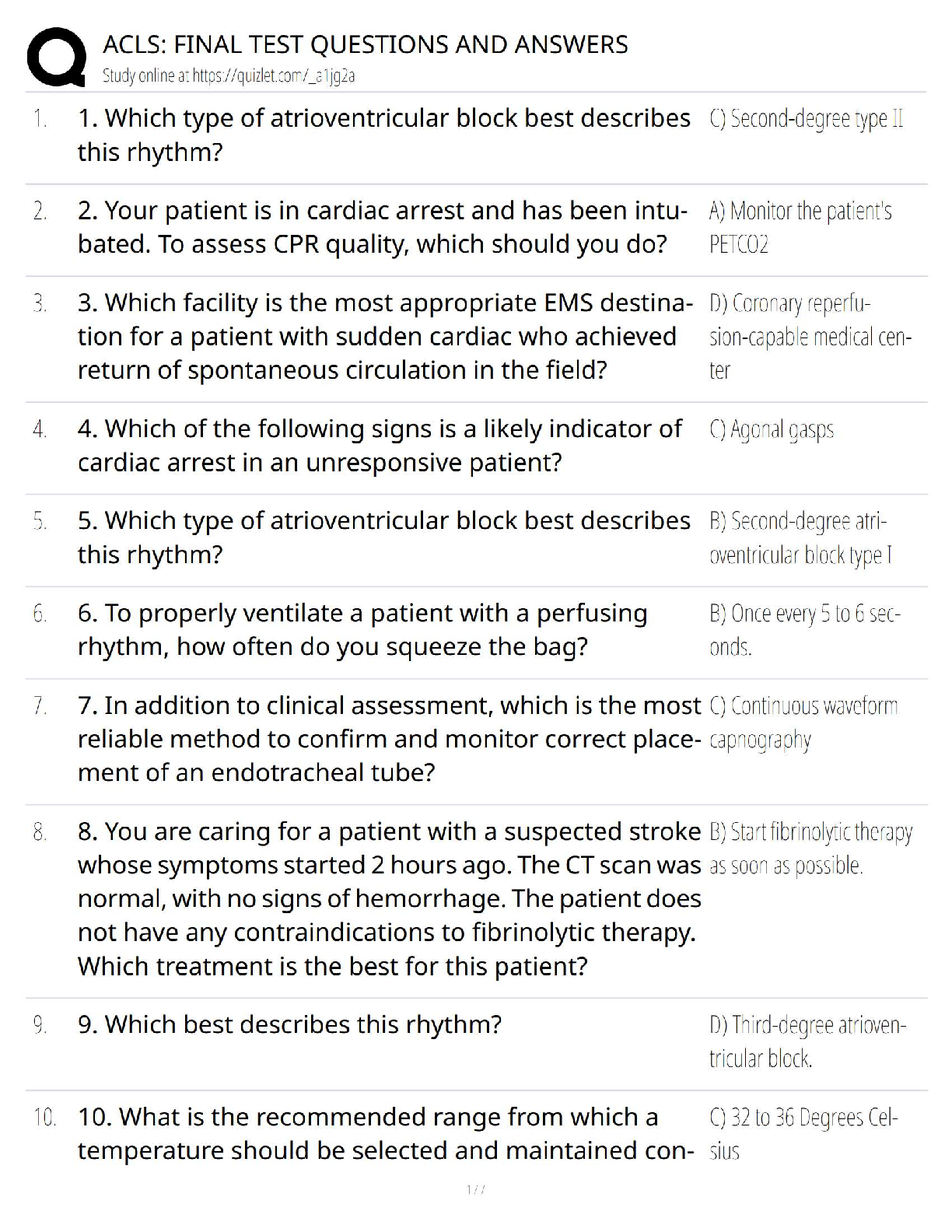
a. Nuclear
b. Biological
c. Explosives
d. Computers
2. According to the text, which of the following is not an act
...
1. Which weapons of mass destruction do most experts predict terrorists will use?
a. Nuclear
b. Biological
c. Explosives
d. Computers
2. According to the text, which of the following is not an act of terrorism?
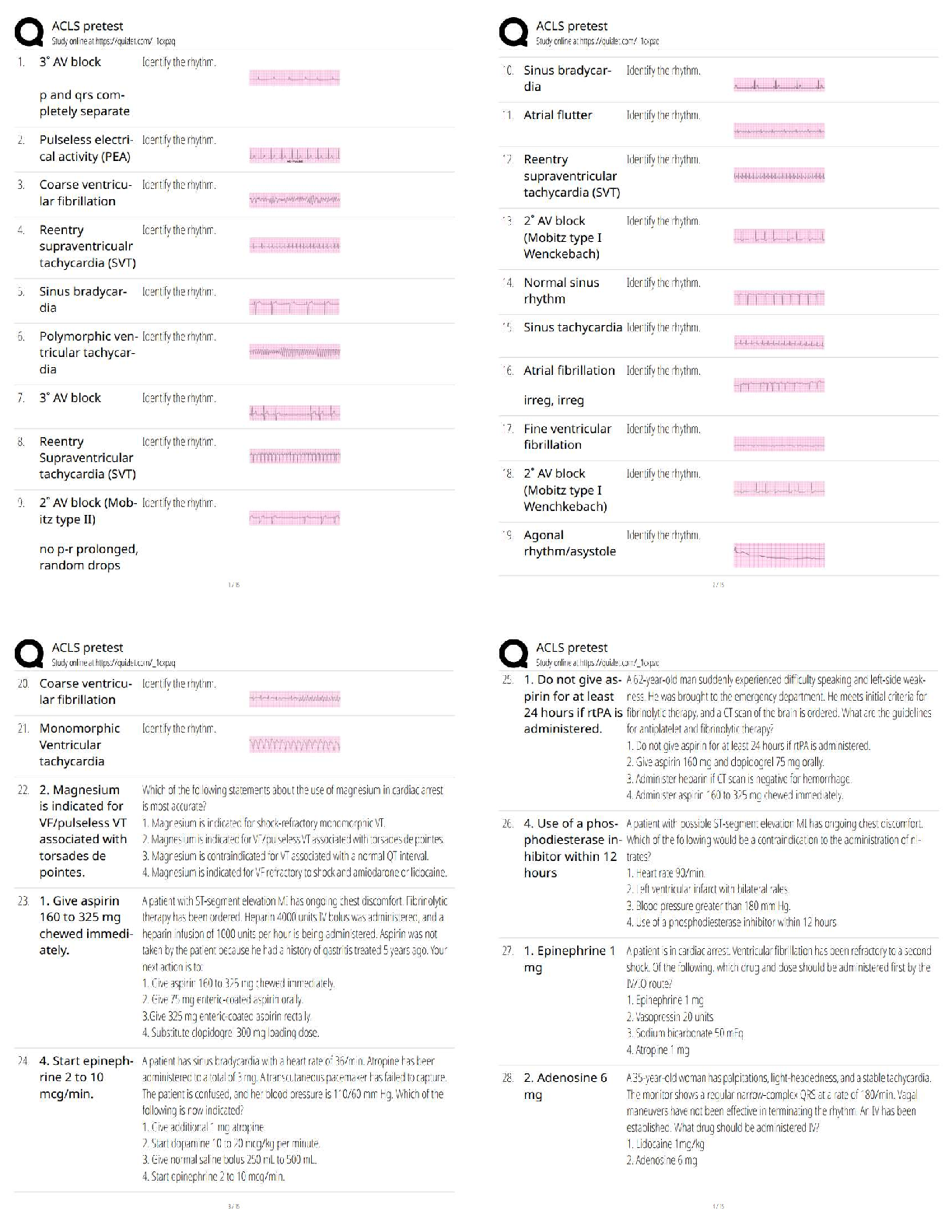
a. Million Man March on Washington, DC
b. Assassination of a political leader
c. Bombing of an abortion clinic
d. Criminal lynching of blacks in the South
3. According to the text, all of the following are considered terrorist acts except:
a. Arson
b. Bombings
c. Kidnapping
d. Speeding
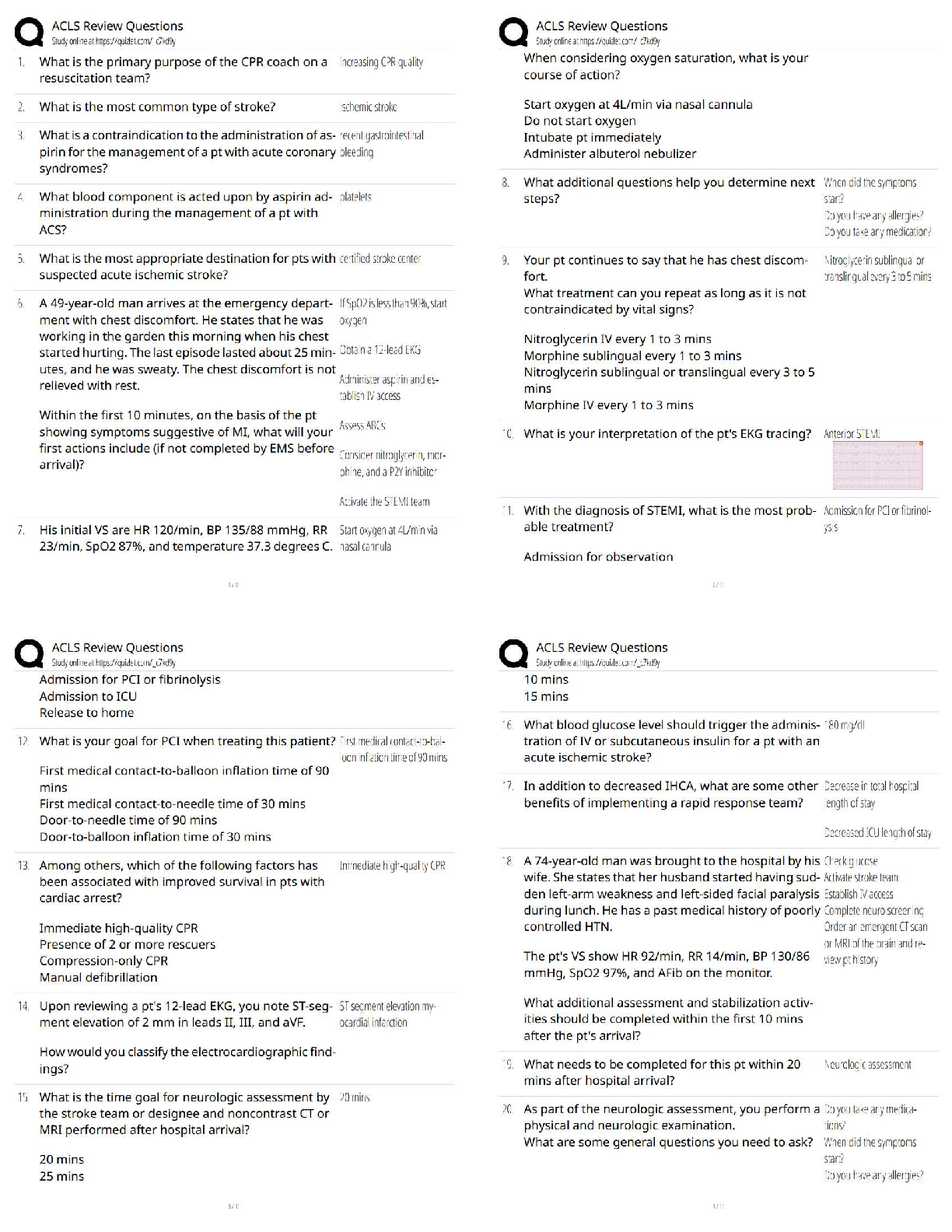
4. The ________________ program supports federal, state, and local law enforcement efforts to combat criminal activity, including terrorism.
a. NIMS
b. RISS
c. NCISP
d. SIMS
5. When a weaker group attacks a stronger group, this is referred to as
a. bisymmetric warfare.
b. lateral warfare.
c. symmetric warfare.
d. asymmetric warfare.
6. Bioterrorism involves such biological weapons of mass destruction as all of the following except:
a. Botulism
b. Flu
c. Plague
d. Smallpox
7. When discussing domestic terrorism, a number of reasons have been given for the acts committed on U.S. soil. Which among the reasons listed below was not mentioned in the text?
a. Opposition to the government
b. Opposition to taxation
c. Opposition to abortion
d. All of the above were mentioned in the text.
8. An example of religiously motivated terrorists is
a. antiabortionists.
b. Red Army faction.
c. Islamic extremists.
d. environmentalists.
9. An example of politically motivated terrorists is
a. antiabortionists.
b. Red Army faction.
c. Islamic extremists.
d. environmentalists.
10. According to the text, the coverage of terrorism inspiring more terrorism is called the
a. realistic coverage effect.
b. contagion effect.
c. jihadi effect.
d. visibility effect.
11. The contagion effect is that
a. terrorism will spread unchecked.
b. terrorism is contained in the same way contagion is contained.
c. media coverage of terrorism inspires more terrorism.
d. biological terrorism will spread geographically.
12. According to the text, ________________ terrorism is foreign based or directed by countries or groups outside the United States against the United States.
a. domestic
b. violent
c. religious
d. international
13. As stated by the authors, terrorism is by nature ________________ because it involves acquiring and using power to force others to submit to terrorist demands.
a. economic
b. philosophical
c. social
d. political
14. What bombings highlight the threat of domestic terrorists?
a. World Trade Center and Centennial Olympic Park
b. Alfred P. Murrah Building and Centennial Olympic Park
c. Alfred P. Murrah Building and the Twin Towers
d. World Trade Center and the Twin Towers
15. The training of police and private security officers to identify terrorists to help them identify potential terrorist targets is conducted and funded under
a. the Critical Incident Project.
b. the Terrorism Identification Project.
c. the Save Our Streets Project.
d. the Safe Cities Project.
16. Jihad refers to what?
a. Hate the Americans
b. Fight until death
c. Kill the Americans
d. Holy war
17. ________________ warfare refers to combat in which a weaker group attacks a superior group by not attacking the stronger adversary head-on but rather attacking areas where the adversary least expects to be hit, causing great psychological shock.
a. International
b. Asymmetric
c. Symmetric
d. Group
18. The Department of Homeland Security (DHS) was established by Executive Order on October 8, 2001 and integrated ________________ different federal departments and -agencies.
a. 31
b. 22
c. 12
d. 18
19. On October 26, 2001, this law was signed into law by President George W. Bush, giving police unprecedented ability to search, seize, detain, or eavesdrop in their pursuit of possible terrorists:
a. US-VISIT Act
b. Homeland Security Act
c. USA PATRIOT Act
d. Executive Order 21
20. Who was the Unabomber?
a. Ramzi Ahmed Yousef
b. Timothy McVeigh
c. Lucas Helder
d. Theodore Kaczynski
21. It has been estimated that approximately ________________ % of the country’s critical infrastructure is protected by private security.
a. 35
b. 65
c. 85
d. 25
22. In 1996, the FBI established what organization to combat terrorism?
a. Homeland Security
b. Counterterrorism Center
c. SEAL Teams
d. FEMA
23. The Department of Homeland Security has established a ________________-level, color-coded threat system used to communicate with public safety officials and the public at large.
a. five
b. four
c. three
d. seven
24. The current color-coded security advisory system has been replaced by a ________________ National Terrorism Advisory System.
a. three-level
b. four-level
c. two-level
d. six-level
25. The first guiding principle of the Department of Homeland Security is to protect
a. citizens of the United States.
b. key government officials.
c. key infrastructure.
d. civil rights.
26. The events of September 11, 2001, led to the development of the ________________, the country’s first standardized management approach unifying federal, state and local governments for incident response.
a. National Corroborative Management System
b. National Incident Management System
c. National Incident Reference System
d. None of the above
27. The IACP has identified five key principles that should form the basis for a national homeland security strategy. Which of the following is one of those key principles?
a. All terrorism is local.
b. Prevention is paramount.
c. Hometown security is homeland security.
d. All of the above
28. Terrorism by nature is
a. religious.
b. political.
c. racial.
d. territorial.
29. ________________ is a proactive program used by the police to identify critical infrastructure locations in Los Angeles and develop a multiagency response.
a. Watch LA
b. L.A.W.
c. Archangel
d. CompStat
30. Local law enforcement can take several steps to prevent racial profiling and/or discrimination against Arab Americans. Which of the following is not a step law enforcement can take?
a. Increase communication and dialogue
b. Develop person-to-person contact
c. Identify community needs
d. Go undercover in mosques
31. According to the text, the first principle of the Department of Homeland Security is to
a. protect and defend America.
b. protect the rights of the accused.
c. protect civil rights and liberties.
d. use any means available to stop terrorism.
32. The Justice Department has issued regulations that allow monitoring inmate-attorney communication if reasonable suspicion exists that the communication will further terrorist actions. This regulation may conflict with which Constitutional Amendment?
a. First
b. Fifth
c. Fourth
d. Sixth
33. The idea that coverage of terrorism will lead to more terrorism is called what?
a. The echo effect
b. The copy-cat effect
c. The contagion effect
d. The proliferation effect
34. The FBI categorizes terrorism in the United States as either domestic or international terrorism.
a. True
b. False
35. The Department of Homeland Security established a five-level, color-coded threat system used to communicate with public safety officials and the public at large.
a. True
b. False
36. The first line of defense against terrorism is the patrol officer in the field.
a. True
b. False
37. According to the text, the single challenge in combating violence facing community policing is countering terrorism while continuing to address crime and disorder.
a. True
b. False
38. The number of domestic terrorist attacks is almost triple the number of international acts of terrorism.
a. True
b. False
39. Terrorists may use arson, explosives and bombs, weapons of mass destruction (biological, chemical or nuclear agents), and technology.
a. True
b. False
40. Cyberterrorism is defined as the intimidation of civilian enterprise through the use of high technology to bring about political, religious, or ideological aims, actions that result in disabling or deleting critical infrastructure data or information.
a. True
b. False
41. The September 11th attacks undoubtedly shifted the priorities of policing.
a. True
b. False
42. According to the text, trafficking in illicit goods and commodities, such as cigarettes, by terrorists and their supporters is a critical element in generating funds.
a. True
b. False
43. As a result of 9/11, the Department of Homeland Security was established, reorganizing the departments of the federal government.
a. True
b. False
44. At the federal level, the FBI is the lead agency for responding to acts of domestic terrorism. The Department of Homeland Security is the lead agency for consequence management (after an attack).
a. True
b. False
45. The fight against terrorism begins in our own backyards—our own communities, our own neighborhoods—and police chiefs need to prepare themselves, their officers and their communities—the people they’ve sworn to protect—against terrorism.
a. True
b. False
46. According to the text, civil libertarians are not concerned that valued American freedoms are being sacrificed in the interest of national safety.
a. True
b. False
47. As stated by the authors, although the federal government has increased its efforts in the area of terrorism prevention and response, a large degree of responsibility for responding to threats of terrorism rests at the local level.
a. True
b. False
48. Terrorism can survive without publicity, and the media generates much of this publicity.
a. True
b. False
49. Concerns that civil rights may be violated or people of Middle Eastern descent could be discriminated against must be considered by law enforcement when addressing terrorism.
a. True
b. False
50. The Pew Research Center conducted a poll in 2011 that showed Muslim Americans were not concerned about Islamic extremism.
a. True
b. False
51. A barrier to improved relations between police and Arab Americans found in a survey of policing Arab American communities was persistent mutual distrust.
a. True
b. False
52. Recruitment of more Arab Americans into policing is seen as a way to improve police-Arab American relations.
a. True
b. False
53. Describe the role media plays in the perpetuation of terrorism. How can law enforcement use this?
54. According to the FBI, ________________ involves violent acts or acts dangerous to human life that violate the criminal laws of the United States or any state or that would be a criminal violation if committed within the jurisdiction of the United States or any state.
55. ________________ is defined by the FBI as “terrorism that initiates, or threatens to initiate, the exploitation of or attack on information systems.”
56. The ________________ is where the coverage of terrorism inspires more terrorism.
57. According to the text, most terrorist acts result from dissatisfaction with a ________________, political, or social system or policy and frustration resulting from an inability to change it through acceptable, nonviolent means.
58. On February 23, 1998, ________________ declared jihad, a holy war on the United States, calling on “every Muslim who believes in God and wishes to be rewarded to comply with God’s order to kill Americans and plunder their money wherever and whenever they find it.”
59. According to the text, the most common threats include ________________ agents, ________________ agents, and ________________ exposure.
60. ________________ involves such biological weapons of mass destruction (WMDs) as anthrax, botulism, and smallpox.
61. A subtitle of the Homeland Security Act of 2002, called the Homeland Security Information Sharing Act, required the president to develop new procedures for ________________, as well as unclassified but otherwise sensitive information, with state and local police.
62. One of the keys to combating terrorism lie with the local ____________ and the intelligence they can provide to federal authorities.
63. Although jurisdictions necessarily focus efforts on protecting logical, high-profile targets for terrorist attacks, ____________ should not be overlooked.
64. Describe the process of ideological development.
65. Describe the types of methods of launching attacks used by terrorists. Identify their most common and dangerous methods.
66. Describe the USA PATRIOT Act and its purpose.
67. List and describe the methods used by terrorists to further their cause and how the United States can and should respond.
68. Describe the role media plays in the perpetuation of terrorism. How can law enforcement use this?
[Show More]








.png)
.png)
.png)