RESEARCH METHODS NOTES CM SIR-1.pdf | Download for quality grades |
$ 10

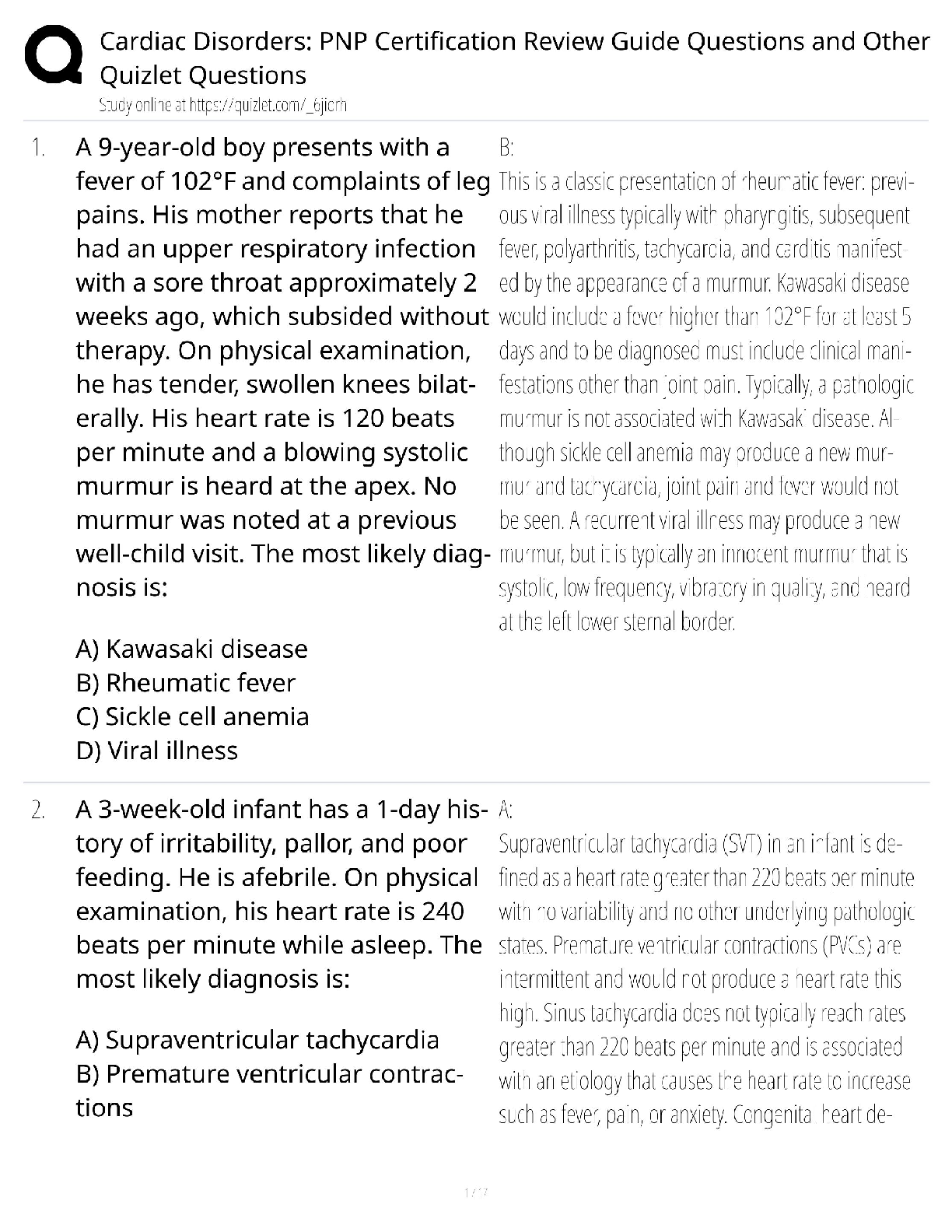
eBook (EPUB) PDF Fundamentals Of Aerospace Medicine 5th Edition By Jeffrey Davis, Jan Stepanek, Jennifer Fogarty, Rebecca Blue
$ 29

FIN2030 Introduction to Finance Finals Exam (Qns & Ans) 2025 SU
$ 11

[eBook] (EPUB) [PDF] Assistive Technologies Principles and Practice 6th Edition By Janice Miller Polgar, Pedro Encarnação, Emma Smith, Albert Cook
$ 30
.png)
WGU Academy US History 1 - Exam 1 Already Passed, Updated 2022
$ 4

WELL AP WEEK 1 QUIZ
$ 10

A&P 1/ BIOD 151 Module 5 Exam Questions and Answers solutions (100% correct) | Portage Learning
$ 14
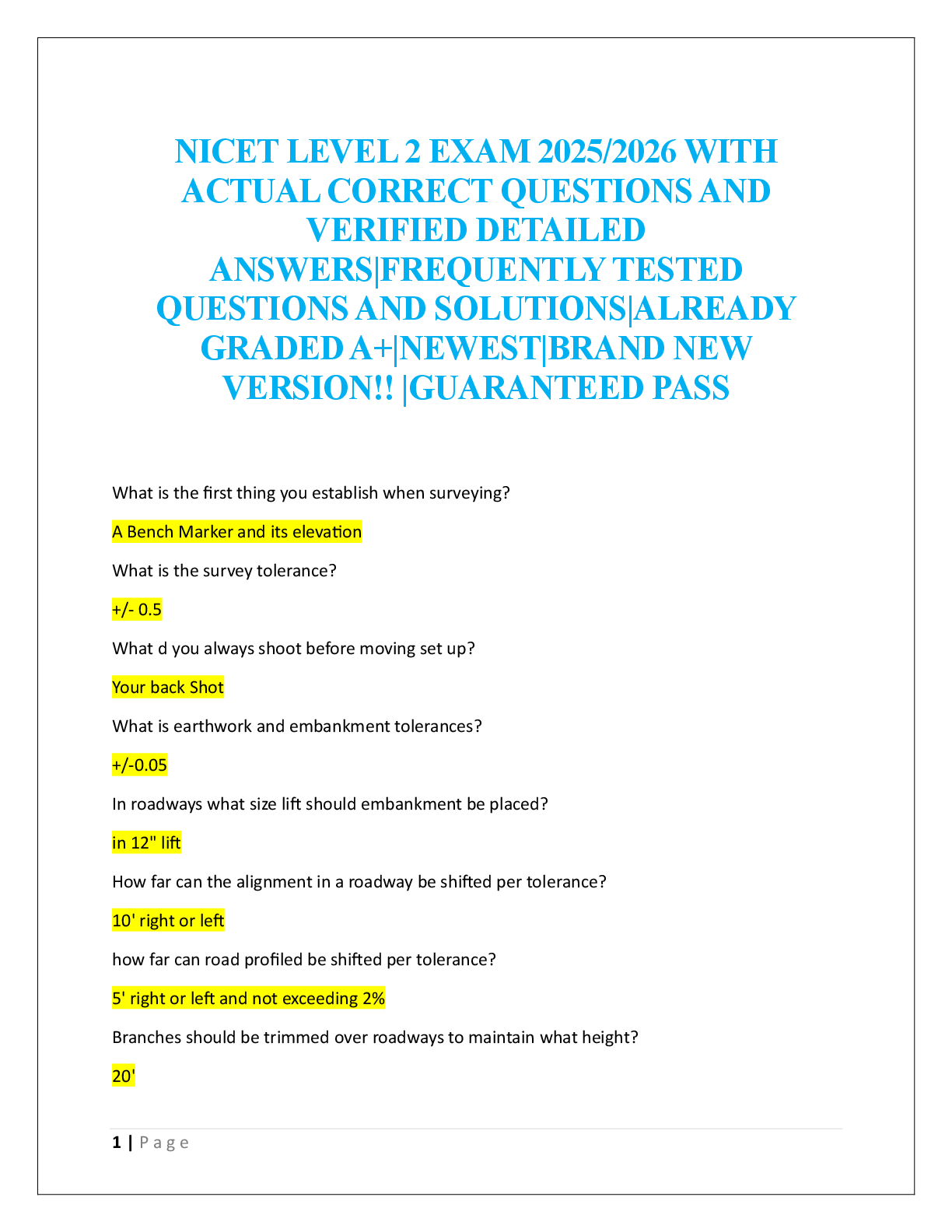
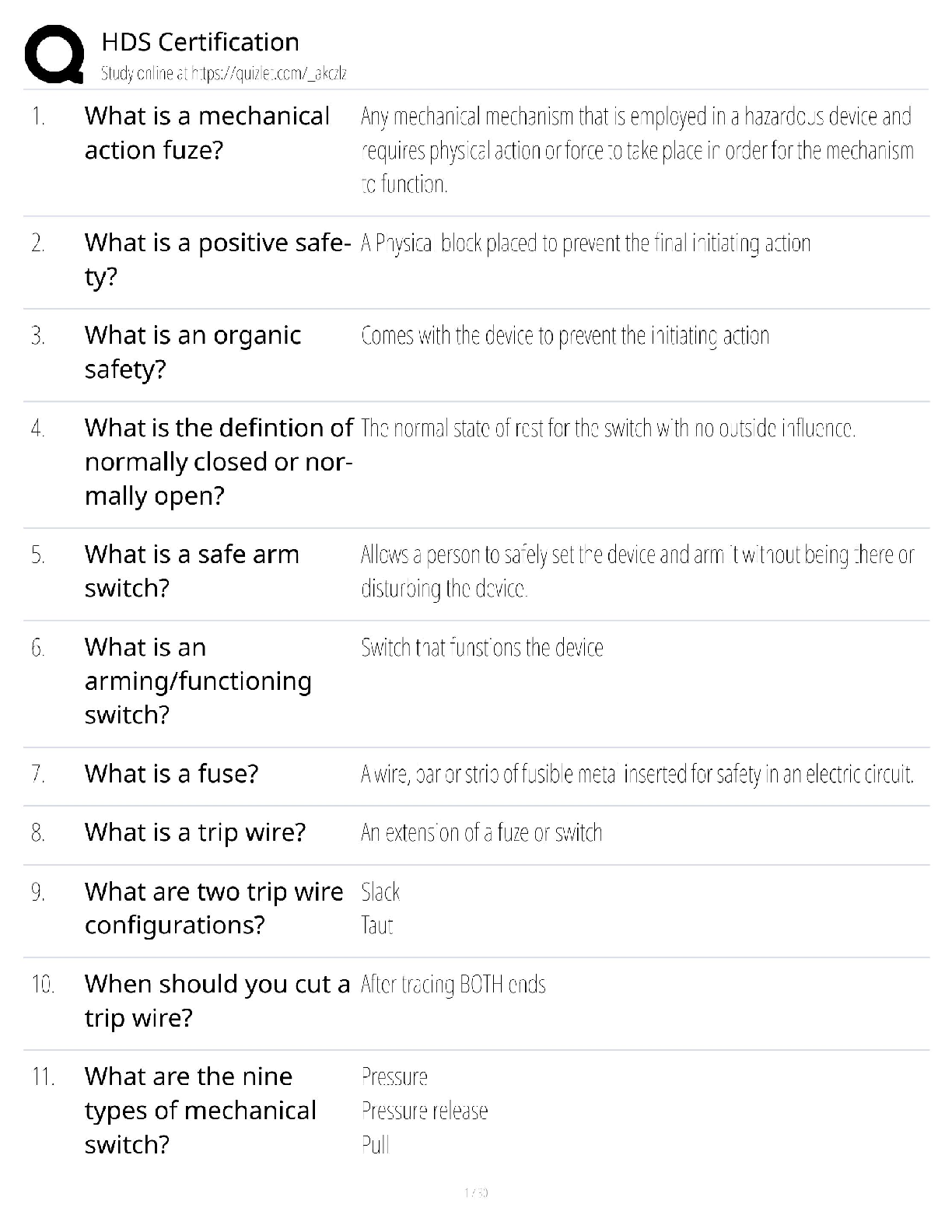
NICET LEVEL 2 EXAM
$ 21
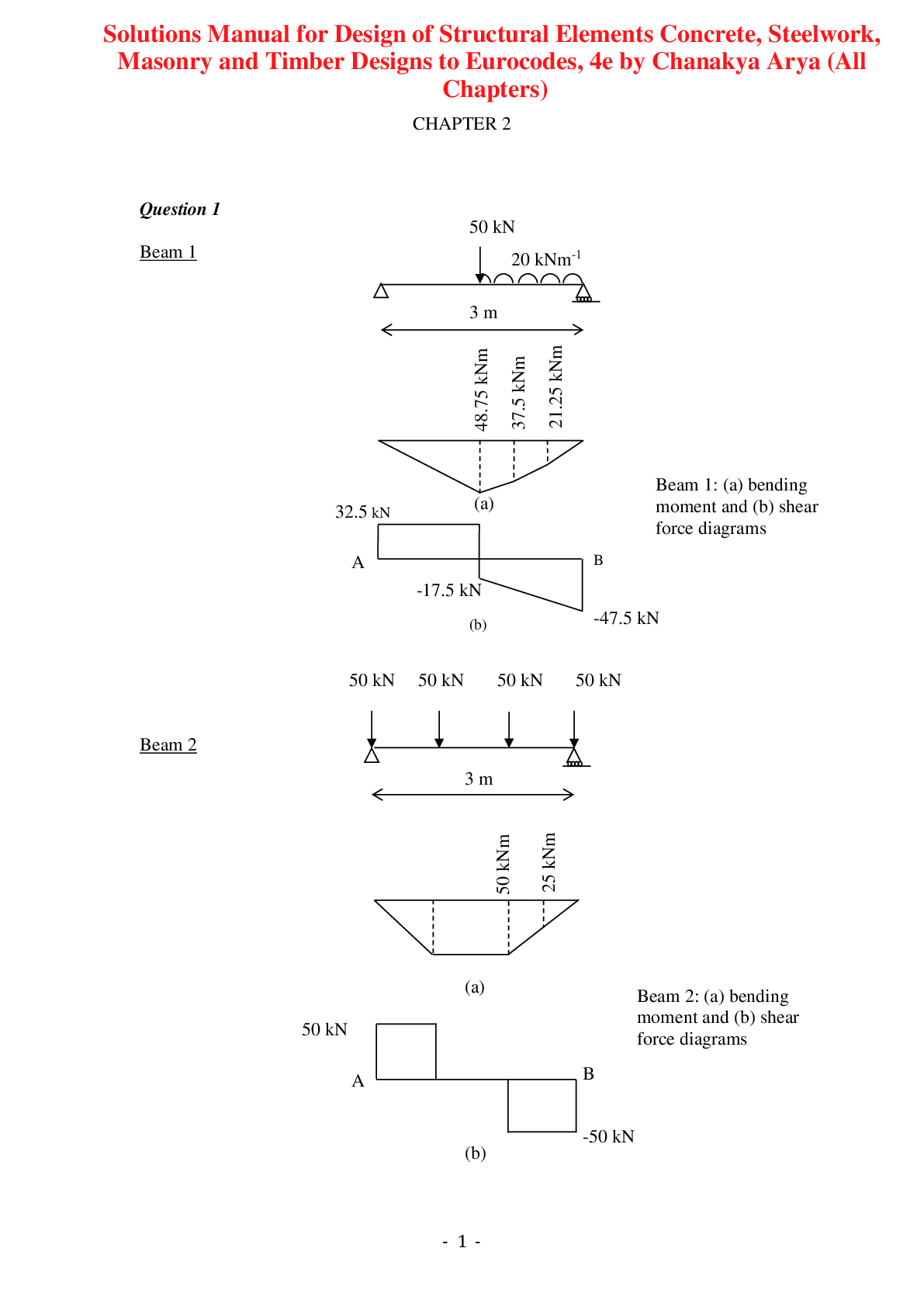
Design of Structural Elements Concrete, Steelwork, Masonry and Timber Designs to Eurocodes, 4e by Chanakya Arya (Solutions Manual)




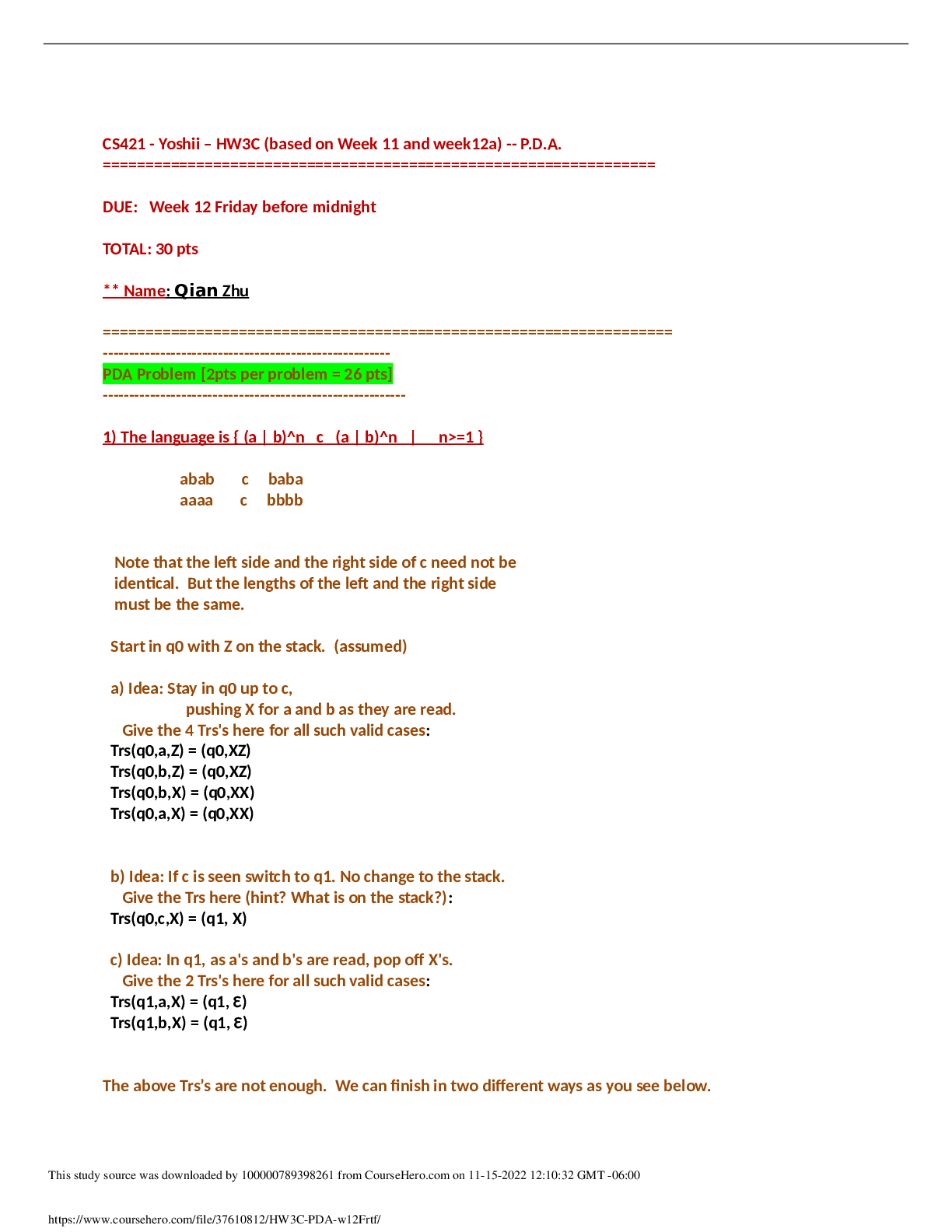


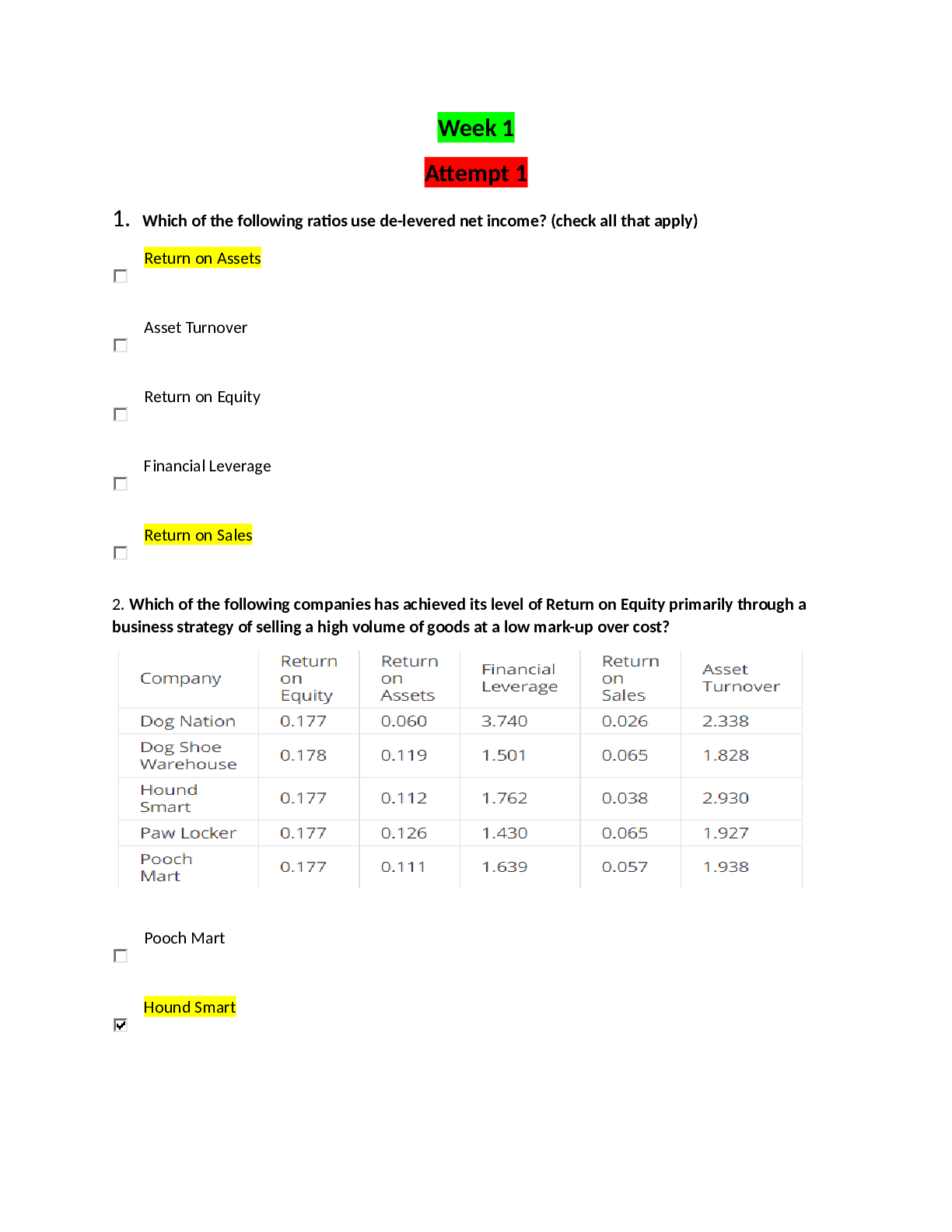
.png)
.png)
.png)
.png)
.png)
.png)
.png)