Information Technology > QUESTIONS & ANSWERS > ITSA 270 Business Continuity and Disaster Recovery Quiz 1 Current Score: 12 out of 12 | Baltimore C (All)
ITSA 270 Business Continuity and Disaster Recovery Quiz 1 Current Score: 12 out of 12 | Baltimore City Community College
Document Content and Description Below
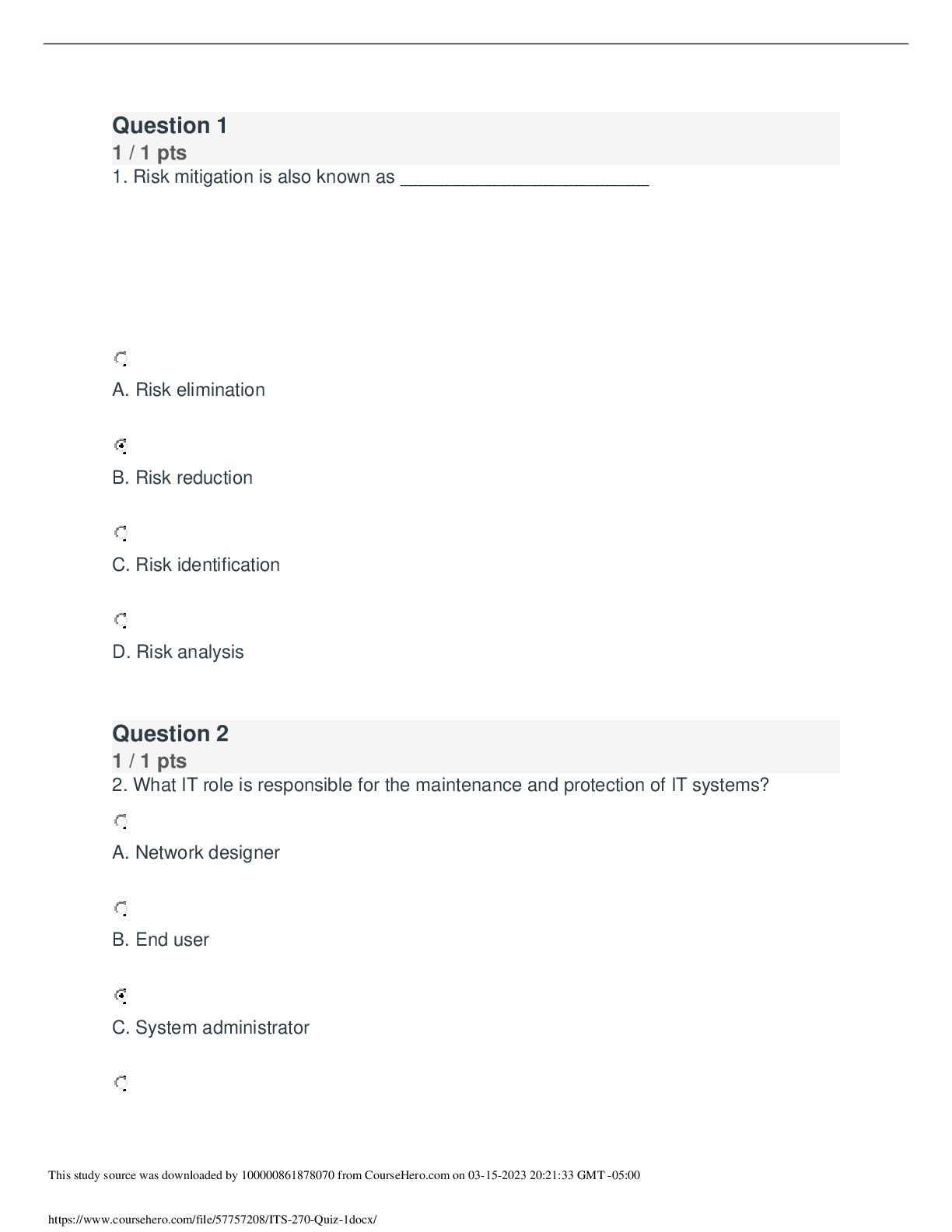
Question 1 1 / 1 pts 1. Risk mitigation is also known as ________________________ A. Risk elimination B. Risk reduction C. Risk identification D. Risk analysis Question 2 1 / 1 pts 2. What IT... role is responsible for the maintenance and protection of IT systems? A. Network designer B. End user C. System administrator D. Upper management Question 3 1 / 1 pts 3. Physical security and training personnel are detective controls whereas antivirus software are preventive controls. True False Question 4 1 / 1 pts 4. _________________ is an activity that represents a possible danger. A. Loss B. Vulnerability C. Threat D. Asset value Question 5 1 / 1 pts 5. __________________ are often the weakest link in IT security. A. Networks B. Firewalls C. People D. Operating systems Question 6 3 / 3 pts 6. What are some of the categories of threats? (select three) A. Loss of reputation B. Vulnerability exploited C. Natural or man - made D. Intentional or accidental E. External or internal Question 7 1 / 1 pts 7. If the wireless network is not an important asset for an organization, and therefore that organization decides to remove that function, what type of risk is implemented? A. Transfer B. Avoidance C. Removal D. Mitigation Question 8 1 / 1 pts 8. Systematically tackling the threats and vulnerabilities in the seven individual domains of a typical IT infrastructure helps you: A. Prioritize the routine tasks and functions performed by employees within the organization. B. Organize the roles, responsibilities, and accountabilities for risk management and risk mitigation. C. Identify the employees most likely to perform an insider attack on the organization. D. Answer the "why" questions regarding potential areas of attack and the motives of attackers. Question 9 1 / 1 pts 9. Because human behavior is unreliable and influenced by factors uncontrolled by policy, which domain represents the greatest risk and uncertainty to an organization? A. LAN-to-WAN Domain B. User Domain C. Remote Access Domain D. Workstation Domain Question 10 1 / 1 pts 10. After performing the cost-benefit analysis, if the benefits outweigh the costs, then the control is often ____________________________. A. Rejected B. Avoided C. Selected D. Deleted Quiz Score: 12 out of 12 Last Attempt Details: Time: 6 minutes Current Score: 12 out of 12 Kept Score: 12 out of 12 1 More Attempt available Take the Quiz Again (Will keep the highest of all your Question 1 1 / 1 pts 1. Risk mitigation is also known as ________________________ A. Risk elimination B. Risk reduction C. Risk identification D. Risk analysis Question 2 1 / 1 pts 2. What IT role is responsible for the maintenance and protection of IT systems? A. Network designer B. End user C. System administrator D. Upper management Question 3 1 / 1 pts 3. Physical security and training personnel are detective controls whereas antivirus software are preventive controls. True False Question 4 1 / 1 pts 4. _________________ is an activity that represents a possible danger. A. Loss B. Vulnerability C. Threat D. Asset value Question 5 1 / 1 pts 5. __________________ are often the weakest link in IT security. A. Networks B. Firewalls C. People D. Operating systems Question 6 3 / 3 pts 6. What are some of the categories of threats? (select three) A. Loss of reputation B. Vulnerability exploited C. Natural or man - made D. Intentional or accidental E. External or internal Question 7 1 / 1 pts 7. If the wireless network is not an important asset for an organization, and therefore that organization decides to remove that function, what type of risk is implemented? A. Transfer B. Avoidance C. Removal D. Mitigation Question 8 1 / 1 pts 8. Systematically tackling the threats and vulnerabilities in the seven individual domains of a typical IT infrastructure helps you: A. Prioritize the routine tasks and functions performed by employees within the organization. B. Organize the roles, responsibilities, and accountabilities for risk management and risk mitigation. C. Identify the employees most likely to perform an insider attack on the organization. D. Answer the "why" questions regarding potential areas of attack and the motives of attackers. Question 9 1 / 1 pts 9. Because human behavior is unreliable and influenced by factors uncontrolled by policy, which domain represents the greatest risk and uncertainty to an organization? A. LAN-to-WAN Domain B. User Domain C. Remote Access Domain D. Workstation Domain Question 10 1 / 1 pts 10. After performing the cost-benefit analysis, if the benefits outweigh the costs, then the control is often ____________________________. A. Rejected B. Avoided C. Selected D. Deleted Quiz Score: 12 out of 12 Last Attempt Details: Time: 6 minutes Current Score: 12 out of 12 Kept Score: 12 out of 12 1 More Attempt available Take the Quiz Again (Will keep the highest of all your [Show More]
Last updated: 3 months ago
Preview 1 out of 6 pages
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$9.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Mar 16, 2023
Number of pages
6
Written in
Additional information
This document has been written for:
Uploaded
Mar 16, 2023
Downloads
0
Views
148




.png)
.png)
.png)
.png)
.png)
.png)
.png)



