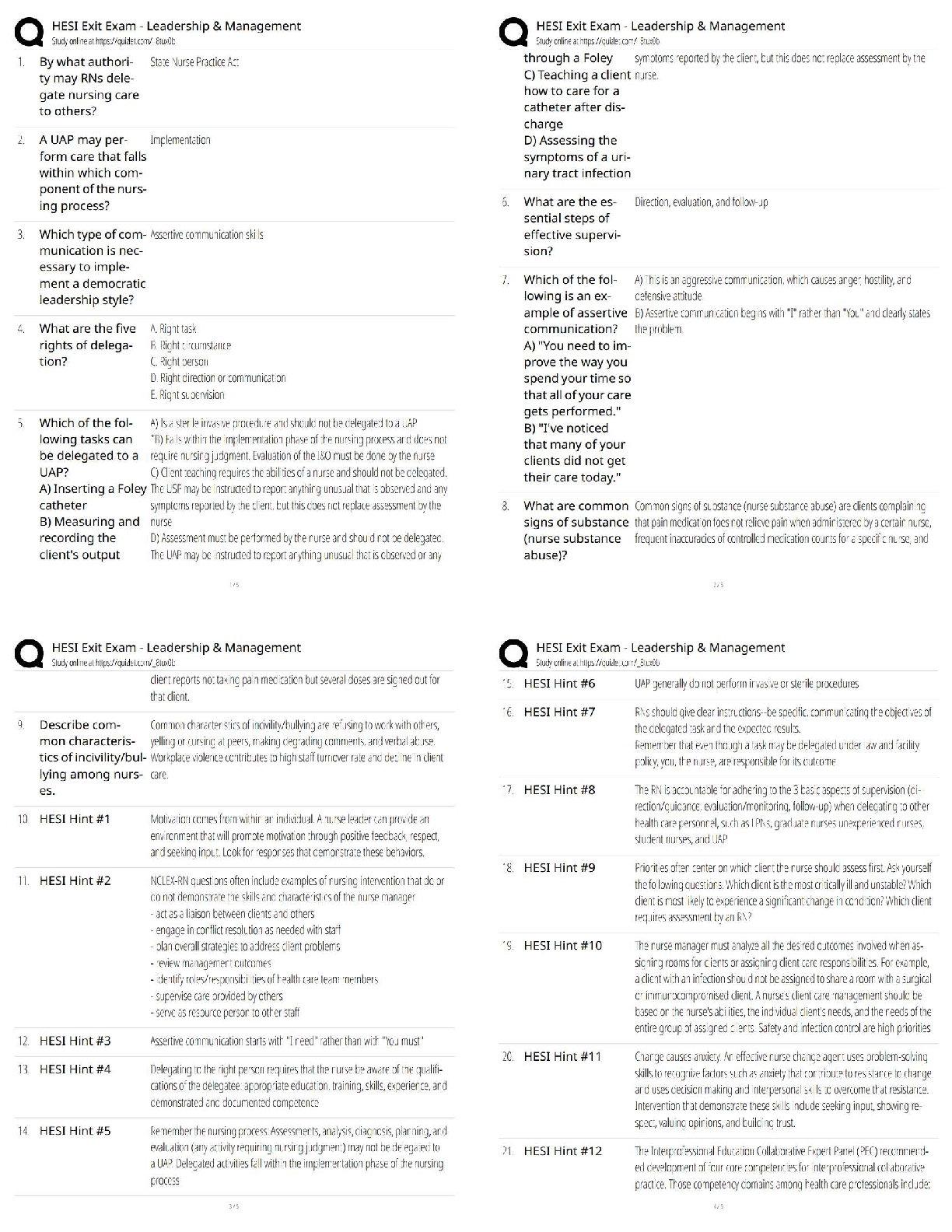
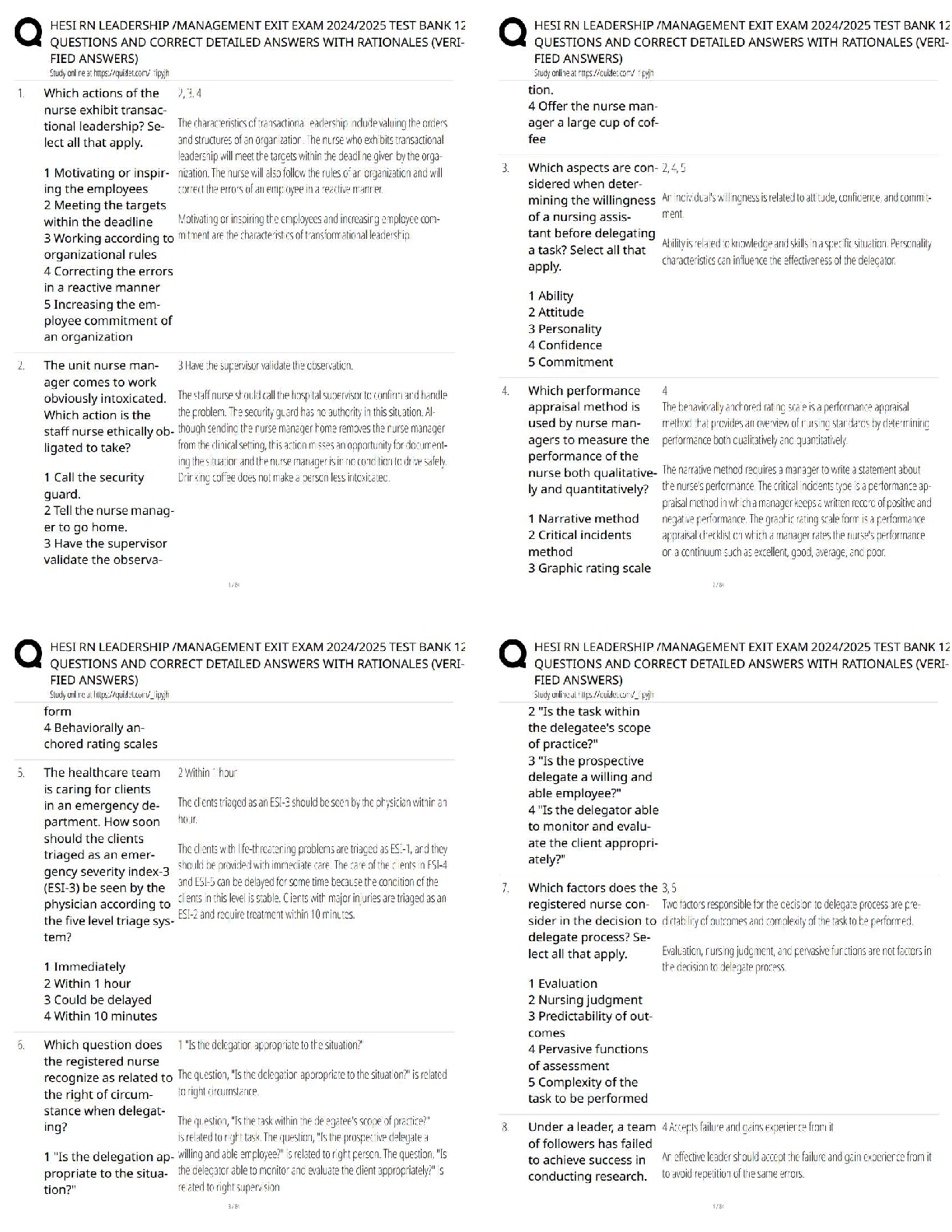
{SOLVED} NR534 Week 2: Advanced Communications in Leadership Systems Chamber 2021
$ 7

Pearson VUE practice test Questions with accurate answers, 100% Acurrate. Verified.
$ 11

ART HISTORY I - SOPHIA LEARNING - UNIT 1 CHALLENGE 2 QUESTIONS AND ANSWERS / SOPHIA LEARNING – ART HISTORY I UNIT 1 CHALLENGE 2
$ 8

Test Bank for Concepts for Nursing Practice 3rd Edition by Jean Foret Giddens - Complete Elaborated and Latest Test Bank. ALL Chapters(1-57)Included and Updated
$ 30

OCR AS LEVEL 2022 COMPUTER SCIENCE QUESTION PAPER H046-02 PAPER 2-H046/02 Algorithms and problem solving
$ 14.5

CPA Australia (ACCOUNTING CORE 2) UPDATED QUESTIONS AND ANSWERS for A+
$ 7.5

AQA A-LEVEL PHYSICS 7408/3A Paper 3 Section A Mark scheme June 2022 Version: 1.0 Final
$ 7

Predictor_Test_1_Typed_Questions 2022
$ 14

MAE 1351 Test 4 Questions and Answers
$ 7

Pearson Edexcel Level 3 GCE 9HI0/2D History Advanced PAPER 2: Depth study Option 2D.1: The unification of Italy, c1830–70 Option 2D.2: The unification of Germany, c1840–71 question paper optio n 2d 1 2 june 2023 + mark scheme
$ 10

AHIP – 3 Questions and Answers with Complete Solutions
$ 4
.png)
Chapter 05: Medication Errors: Preventing and RespondingTest Bank
$ 6

eBook [PDF] Leading Through Bias 5 Essential Skills to Block Bias and Improve Inclusion at Work 1st Edition By Poornima Luthra, Sara Louise Muhr
$ 29

>_ GCE Further Mathematics A Y541/01: Pure Core 2 || Mark Scheme OCT 2021
$ 6

(ASU) MAT 210 BRIEF CALCULUS FINAL EXAM GUIDE QNS & ANS
$ 13

Fission and Fusion Atomic Structure. QUESTIONS PAPER. GRADED A+
$ 7

Test Bank for Inquiry into Physics 8th Edition by Ostdiek-a comprehensive study guide-2022
$ 17

TESOL Questions and Answers Already Passed
$ 10
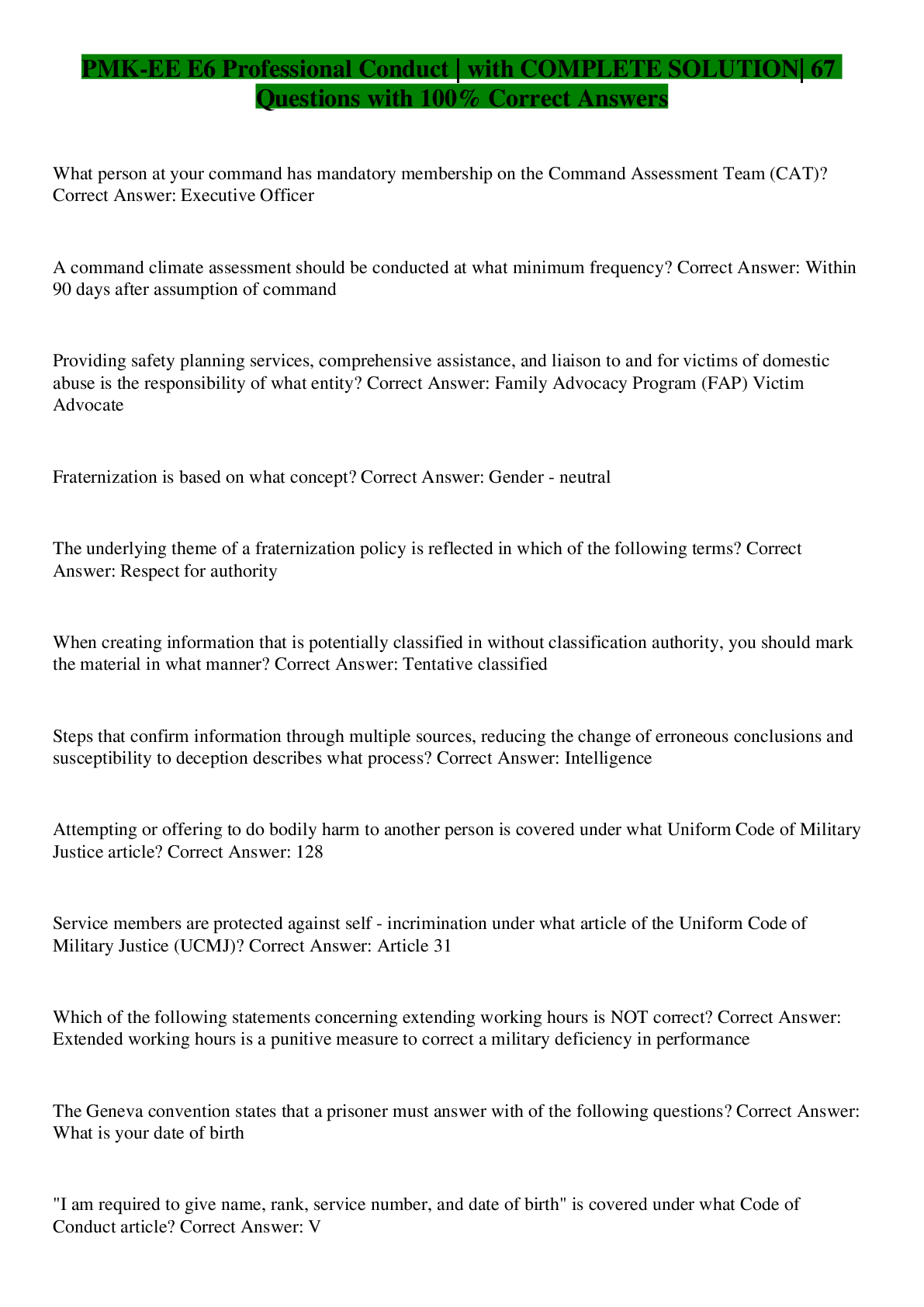
PMK-EE E6 Professional Conduct | with COMPLETE SOLUTION| 67 Questions with 100% Correct Answers
$ 9

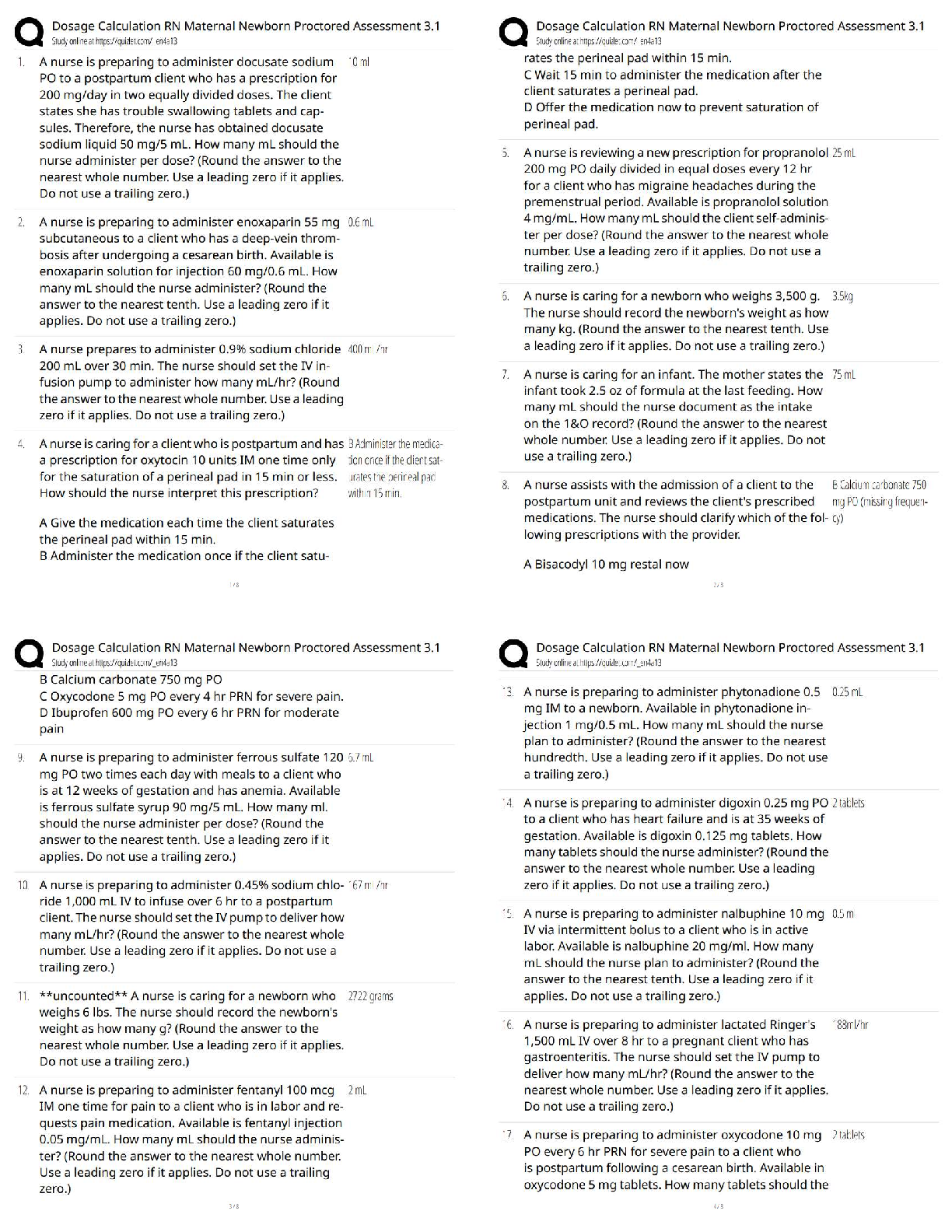
Maternal Newborn ATI Questions - Exam 1 Leave the first rating. Get the best grades with less strive. Graded A+
$ 8

Nursing Concepts Beginning Test WITH CORRECT QUESTIONS AND ANSWERS 2022 LATEST.
$ 18

MSSC QUALITY POST TEST QUESTIONS AND ANSWERS RATED A.
$ 15

Chapter 11: CNN Exam 18 Questions with Verified Answers,100% CORRECT
$ 7.5

AS Level English Language H070/01 Exploring language May 2023 QP
$ 4
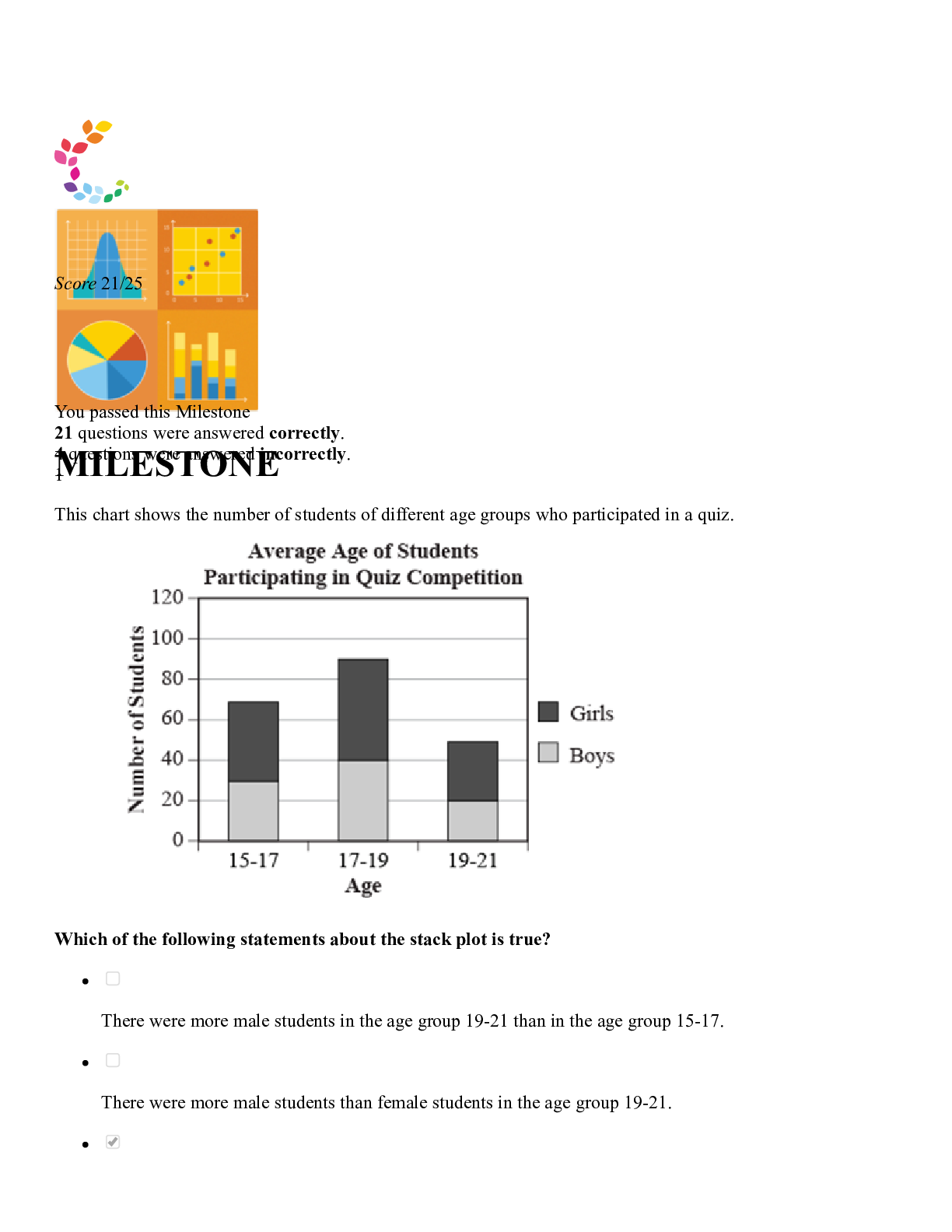
Sophia Statistics Final Milestone 2022 Questions and Answers -All Answers Are Correct -Graded 100%
$ 12
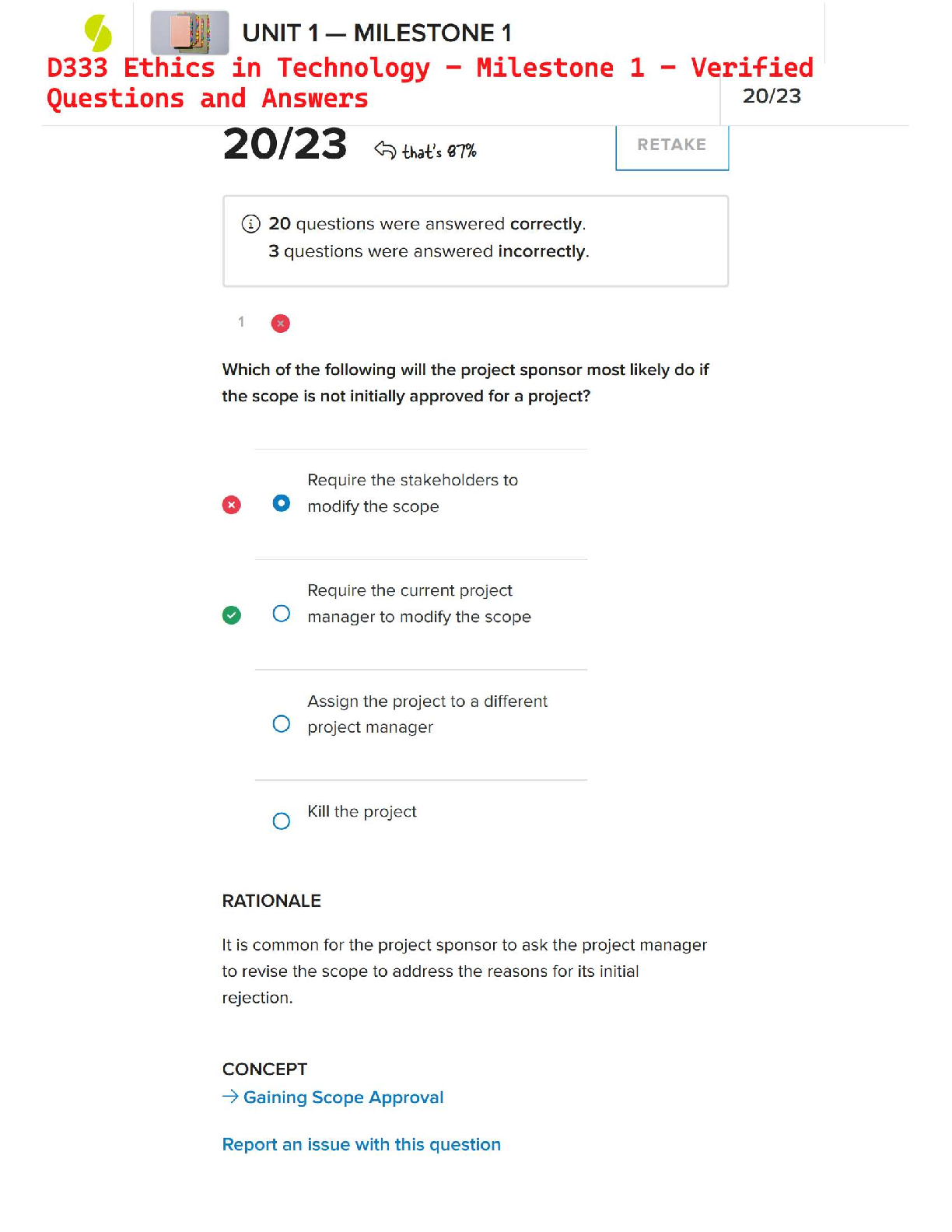
D333 Ethics in Technology – Milestone 1 – Verified Questions and Answers | Western Governors University
$ 15

ISYE 6501 Final Quiz - Verified Answers(This quiz consists of frequently tested question )
$ 11

Psychiatric-Mental Health Nurse Practitioner Certification Exam Practice Questions – Course Code PMHNP 2025/2026 – American Nurses Credentialing Center
$ 12.5

ECONOMIE- INFLATIE IS DE SLUIPMOORDENAAR VAN ONS ECONOMIE -2023 TO 2024
$ 5

AQA AS BUSINESS 7131/2 Paper 2 Business 2 Mark scheme June 2020 Version: 1.0 Final Mark Scheme
$ 6.5

prup u Chapter 9 questions with correct answers to boost your grades
$ 13.5
.png)
ECET-105 Week 5 Lab: Designing Adders and Subtractors (GRADED A+)
$ 15

GRADY HARRIS IHUMAN CASE STUDY “TUMMY ACHE”
$ 20

Pharmacology 2019 ATI Questions and Answers Already Passed
$ 7
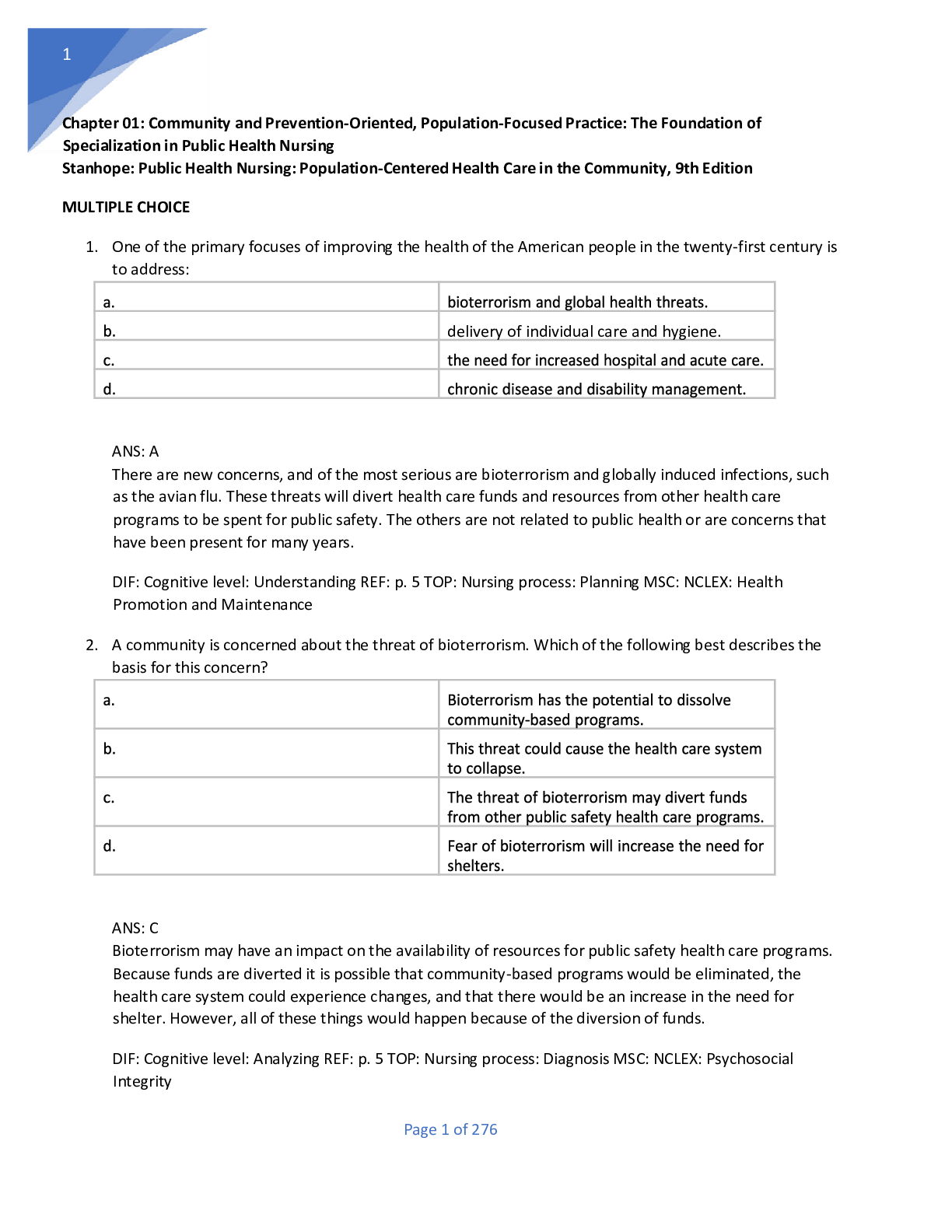
Test Bank for Public Health Nursing: Population-Centered Health Care in the Community, 9th Edition by Marcia Stanhope, Jeanette Lancaster
$ 22

2024 Bonent Exam Study Questions with Complete Solutions
$ 17

eBook PDF Medical Presentations 1st Edition By Terry Irwin, Julie Terberg, Echo Swinford







.png)
.png)
.png)
.png)
.png)
.png)
.png)