Telecommunication and Information Technology > QUESTIONS & ANSWERS > University of the Cumberlands EMISS ISOL532 Telecommunications and network security. Chapter 9 & 10 (All)
University of the Cumberlands EMISS ISOL532 Telecommunications and network security. Chapter 9 & 10 Quiz. 20 Q&A
Document Content and Description Below
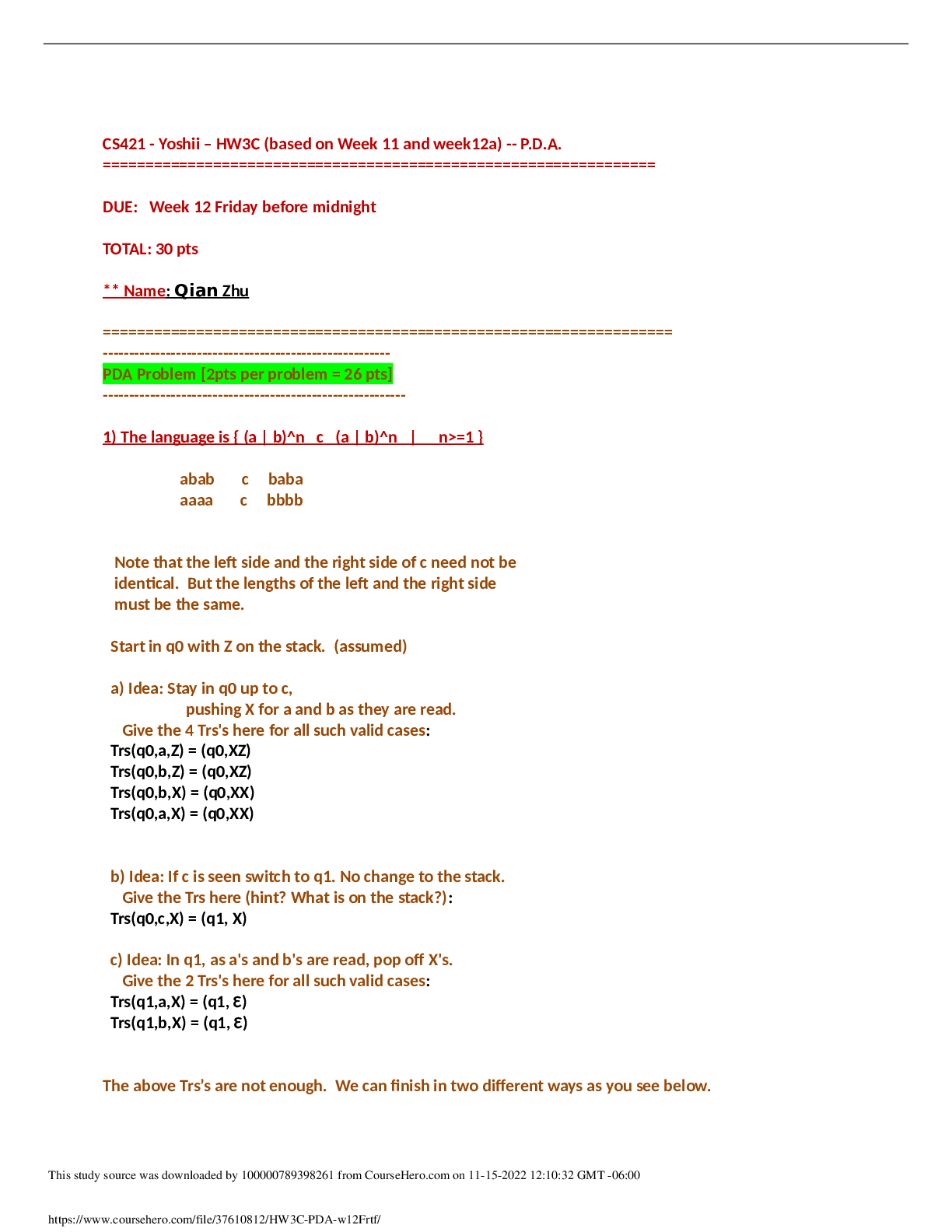
QUESTION 1 1. Which of the following is not true of security for a SOHO? Cost effective Easy to implement Not as vulnerable as corporate offices Have a higher risk than corporate offices 5.000... 00 points QUEST ION 2 1. What term describes a small text file used by Web browsers and servers to track Web sessions? Web-based service Web browser Popup blocker Cookie filter 5.00000 points QUEST ION 3 1. Windows Firewall is a native operating system firewall. True False 5.00000 points QUEST ION 4 1. In theory, the use of a software firewall as a replacement for a network appliance can work as long as the host OS's network communication is routed through which type of firewall? Virtual firewall Appliance firewall Hardware firewall Commercial firewall 5.00000 points QUEST ION 5 1. When troubleshooting firewalls, which of the following is not something you should do after you attempt a fix? Make multiple fixes. Repeat the failure. Test after each attempt. Reverse or undo solution failures. 5.00000 points QUESTION 6 1. Which of the following describes a native firewall? A small text file used by Web browsers and servers to track Web sessions A firewall in an operating system or hardware device that is placed there by the vendor or manufacturer Open-source and commercial software firewalls for most operating systems Windows 7 host software firewall 5.00000 points QUESTION 7 1. Netcat is a hacker tool that creates network communication links using UDP or TCP ports that support the transmission of standard input and output. True False 5.00000 points QUESTION 8 1. Which of the following describes any harmful code or site that depends upon the user’s actions to be accessed or activated? Native firewall Active threat Passive threat Cookie filter 5.00000 points QUESTION 9 1. Wireshark is a free packet capture, protocol analyzer, and sniffer that can analyze packets and frames as they enter or leave a firewall. True False 5.00000 points QUESTION 10 1. Which of the following command-line tools will list the current open, listening, and connection sockets on a system as well as the service related to each socket? TCPVie w Fport Netstat Nmap 5.00000 points QUESTION 11 1. Which of the following are documents that can help you to review and assess your organization’s status and state of security? Firewall checklists Risk assessment Security Technical Implementation Guides (STIGs) Incident response plan 5.00000 points QUESTION 12 1. Which one of the following is not a third-party software firewall but is a security suite? eConceal Pro Look ’n’ Stop Lavasoft Personal Firewall McAfee Personal Firewall Plus 5.00000 points QUEST ION 13 1. The Detection phase of an incident response plan confirms breaches. True False 5.00000 points QUEST ION 14 1. Which of the following is disabled by default and requires an invitation? The Onion Router (TOR) Remote Desktop Protocol (RDP) and Remote Assistance SubSeven Netcat 5.00000 points QUESTION 15 1. Which of the following is hardware that connects a local network—or even a single computer—to a telco’s carrier network to access the Internet? IPFire ISP connection device DSL line SOHO 5.00000 points QUESTION 16 1. Linux distributions automatically come with a native software firewall. True False 5.00000 points QUESTION 17 1. A native firewall is not necessarily installed by default, but can be added to a system through an update or patch installation. True False 5.00000 points QUESTION 18 1. If your home router is a wireless device, you should change the service set identifier (SSID) from the default setting. True False 5.00000 points QUESTION 19 1. The Containment phase of an incident response plan restrains further escalation of the incident. True False 5.00000 points QUESTION 20 1. Which of the following is a double-blind encapsulation system that enables anonymous but not encrypted Internet communications? The Onion Router (TOR) Cryptcat Back Orifice Remote Desktop Protocol (RDP) and Remote Assistance [Show More]
Last updated: 2 years ago
Preview 1 out of 5 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$8.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 09, 2022
Number of pages
5
Written in
Additional information
This document has been written for:
Uploaded
Aug 09, 2022
Downloads
0
Views
82





.png)
.png)
.png)
.png)
.png)
.png)
.png)












