Telecommunication and Information Technology > QUESTIONS & ANSWERS > University of the Cumberlands EMISS ISOL532 Telecommunications and network security. Chapters 13 & 1 (All)
University of the Cumberlands EMISS ISOL532 Telecommunications and network security. Chapters 13 & 14 Exam. 20 Q&A
Document Content and Description Below
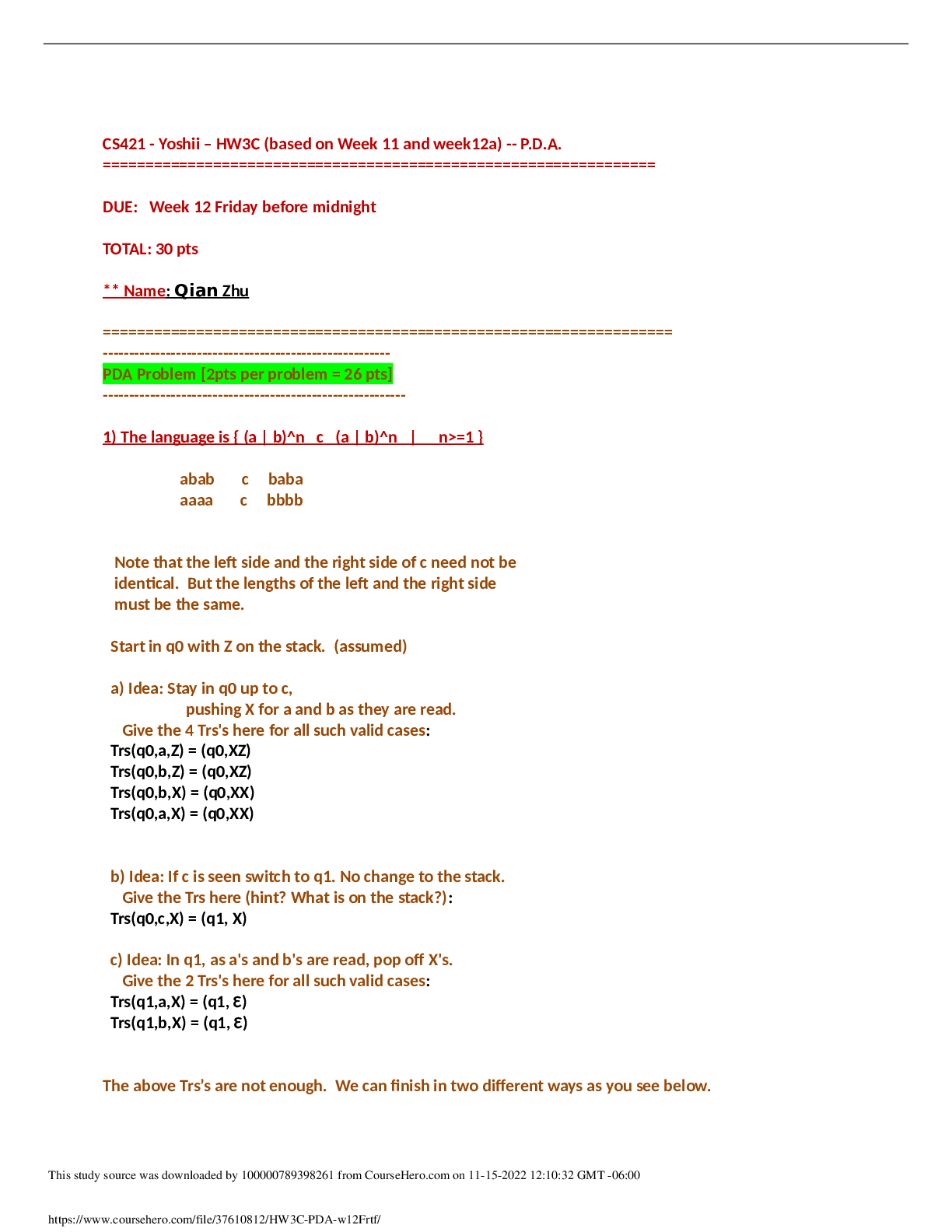
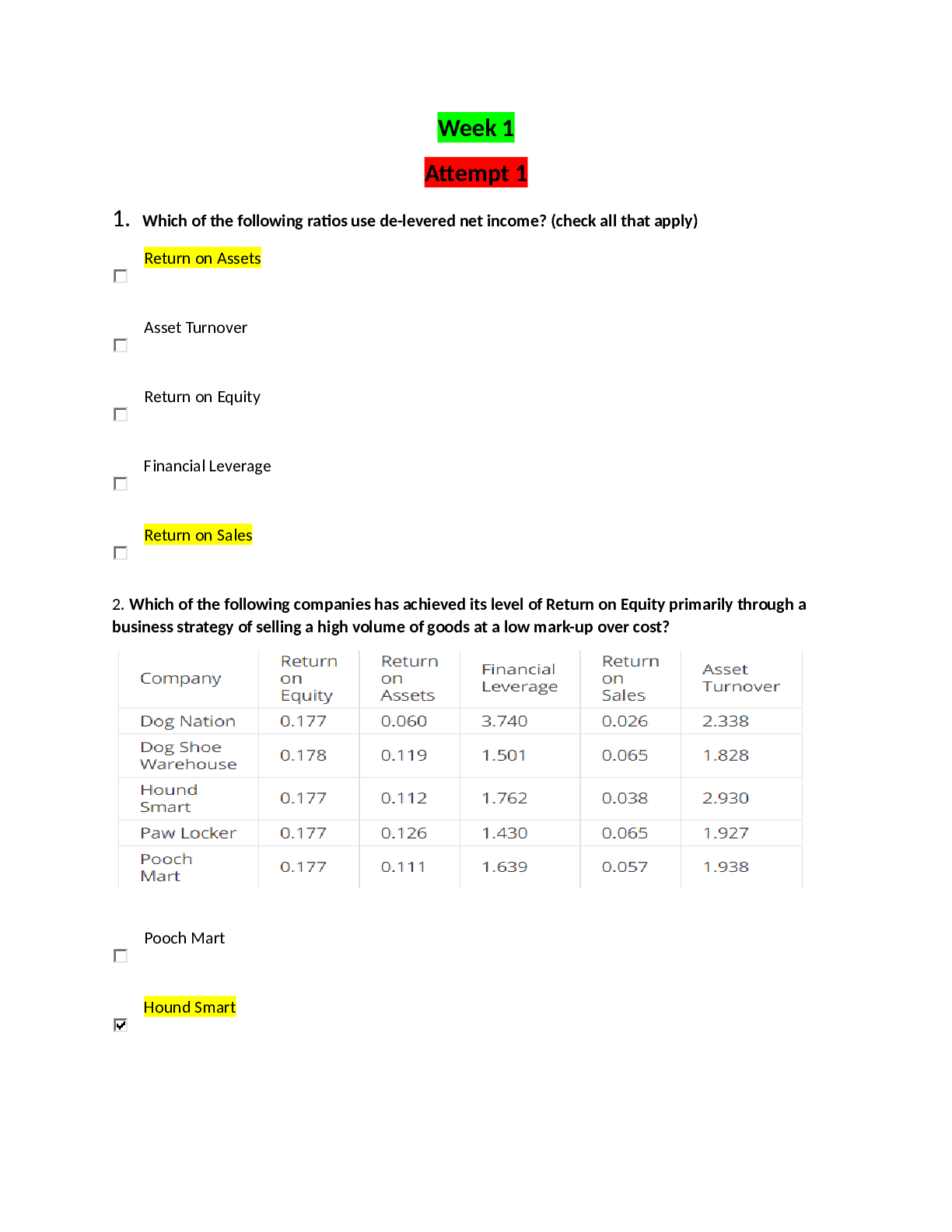
1. Which of the following offers keycard security and allows you to restrict the times that your computer can be remotely accessed? GoToMyPC LogMeIn NTRconne ct Internet café 5.00000 points ... QUESTION 2 1. Which of the following is a minimum requirement for running SmoothWall? Three NICs 10 GB hard drive 84MHZ processor 512 MB PC SDRAM 5.00000 points QUESTION 3 1. For which of the following does the mobile user take specific actions to connect to the VPN? Remote gateway Host-to-gateway VPN Gateway-to-gateway VPN VPN appliance 5.00000 points QUESTION 4 1. The degree to which a firewall can impose user access restrictions is known as which of the following? Security assurance Privilege control Authentication Audit capabilities 5.00000 points QUESTION 5 1. Used with compatible VPNs, IPSec guarantees the authenticity, integrity, and confidentiality of network traffic. True False 5.00000 points QUESTION 6 1. SOHO VPN hardware firewalls are generally built on unsecure VPNs when used for transfer e-mail and sensitive files. True False 5.00000 points QUESTION 7 1. GoToMyPC, LogMeIn, and NTRconnect allow you to use a Mac as the client, but only NTRconnect enables you to use a Mac as the host. True False 5.00000 points QUESTION 8 1. To download the RPM version of Openswan, you must have the IPSectools RPM package installed on your system. True False 5.00000 points QUESTION 9 1. Which of the following risks can compromise the confidentiality of documents stored on the server? Risk that transaction data can be intercepted Risk that unauthorized individuals can breach the server’s document tree Risk that information about the server can be accessed Risk of denial of service attacks 5.00000 points QUESTION 10 1. An intranet is an external network. True False 5.00000 points QUESTION 11 1. While the Tor network does provide a level of anonymity, the user never knows what other computers the request will go through; data sent and received can be captured by any of these computers. True False 5.00000 points QUESTION 12 1. Whether you’re using a host-to-gateway or gateway-to-gateway configuration, you should not put the VPN server directly on the Internet but you should place it behind a firewall such as in a DMZ configuration. True False 5.00000 points QUESTION 13 1. Which of the following will generate a graph of network traffic every five minutes on a firewall? Asymmetric Digital Subscriber Line (ADSL) TCPdump RRDtool DDNS 5.00000 points QUESTION 14 1. Which of the following is a proprietary protocol developed by Microsoft that provides a user with a graphical interface to another computer? Secure Sockets Layer (SSL) Layer 2 Tunneling Protocol (L2TP) Point-to-Point Tunneling Protocol (PPTP) Remote Desktop Protocol (RDP) 5.00000 points QUESTION 15 1. Asymmetric Digital Subscriber Line (ADSL) is a form of the digital subscriber line technology, which enables faster data transmission over copper telephone lines than a conventional voice band modem can provide. True False 5.00000 points QUESTION 16 1. When installing SmoothWall, at least three network cards (NICs) are needed in the SmoothWall machine. True False 5.00000 points QUESTION 17 1. A bastion host allows the firewall to connect to the internal network and the perimeter network. True False 5.00000 points QUESTION 18 1. Which of the following requires PKI support and is used for encryption with newer tunneling protocols? Secure Socket Tunneling Protocol (SSTP) Layer 2 Tunneling Protocol (L2TP) Point-to-Point Tunneling Protocol (PPTP) Internet Key Exchange v2 (IKEv2) 5.00000 points QUESTION 19 1. Which of the following is a third-party tool that Symantec offers as a solution for organizations to access and securely manage remote computers? NTRconnect Remote Assistance pcAnywhere LogMeIn 5.00000 points QUESTION 20 1. Which of the following allows administrators to connect remotely into servers from their desktop computers? Terminal Services for Administration TS RemoteApp Terminal Services for Applications TS Web Access [Show More]
Last updated: 2 years ago
Preview 1 out of 5 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$8.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 09, 2022
Number of pages
5
Written in
Additional information
This document has been written for:
Uploaded
Aug 09, 2022
Downloads
0
Views
102





.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)










