Telecommunication and Information Technology > QUESTIONS & ANSWERS > University of the Cumberlands EMISS ISOL532 Telecommunications and network security. Chapters 11 & 1 (All)
University of the Cumberlands EMISS ISOL532 Telecommunications and network security. Chapters 11 & 12 Exam (1). 20 Q&A
Document Content and Description Below
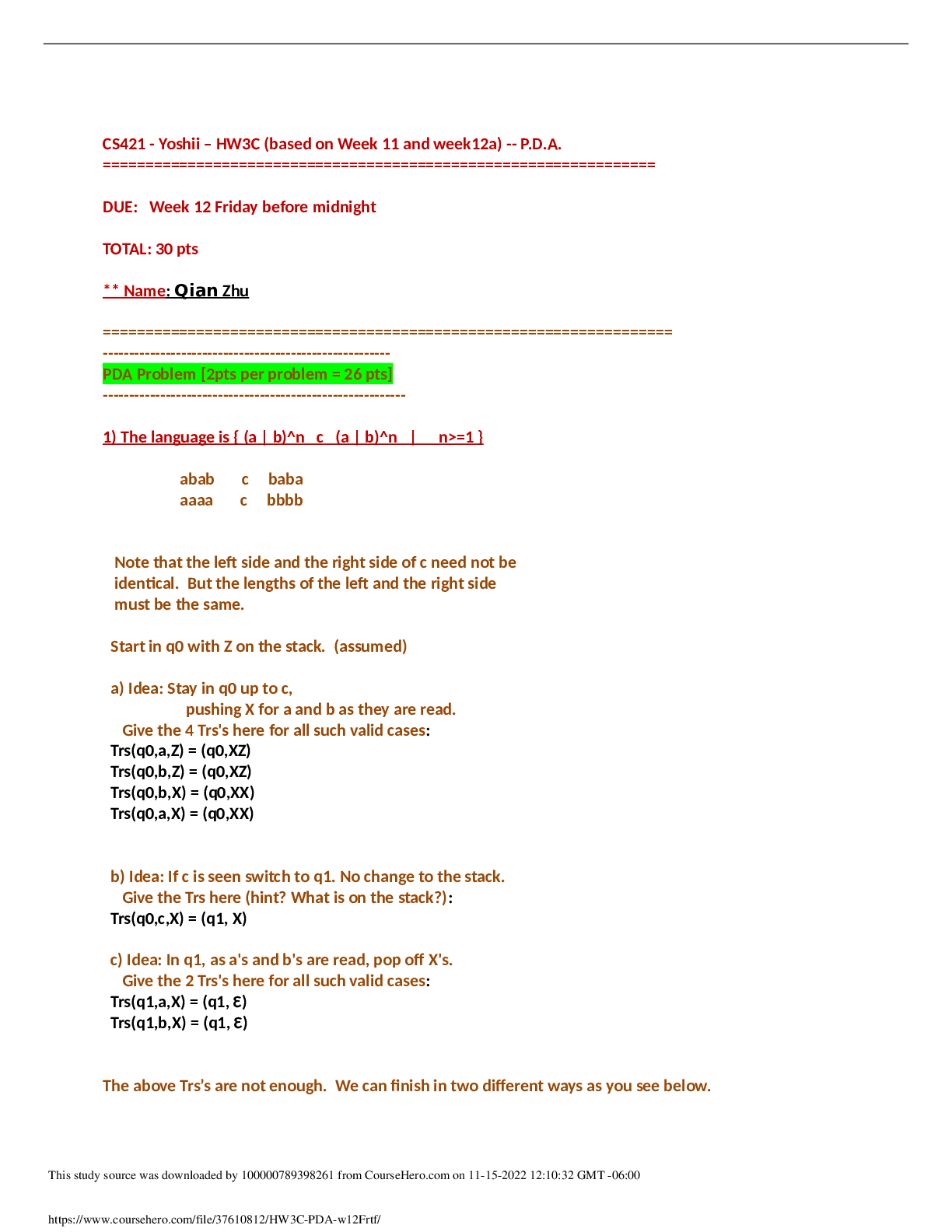
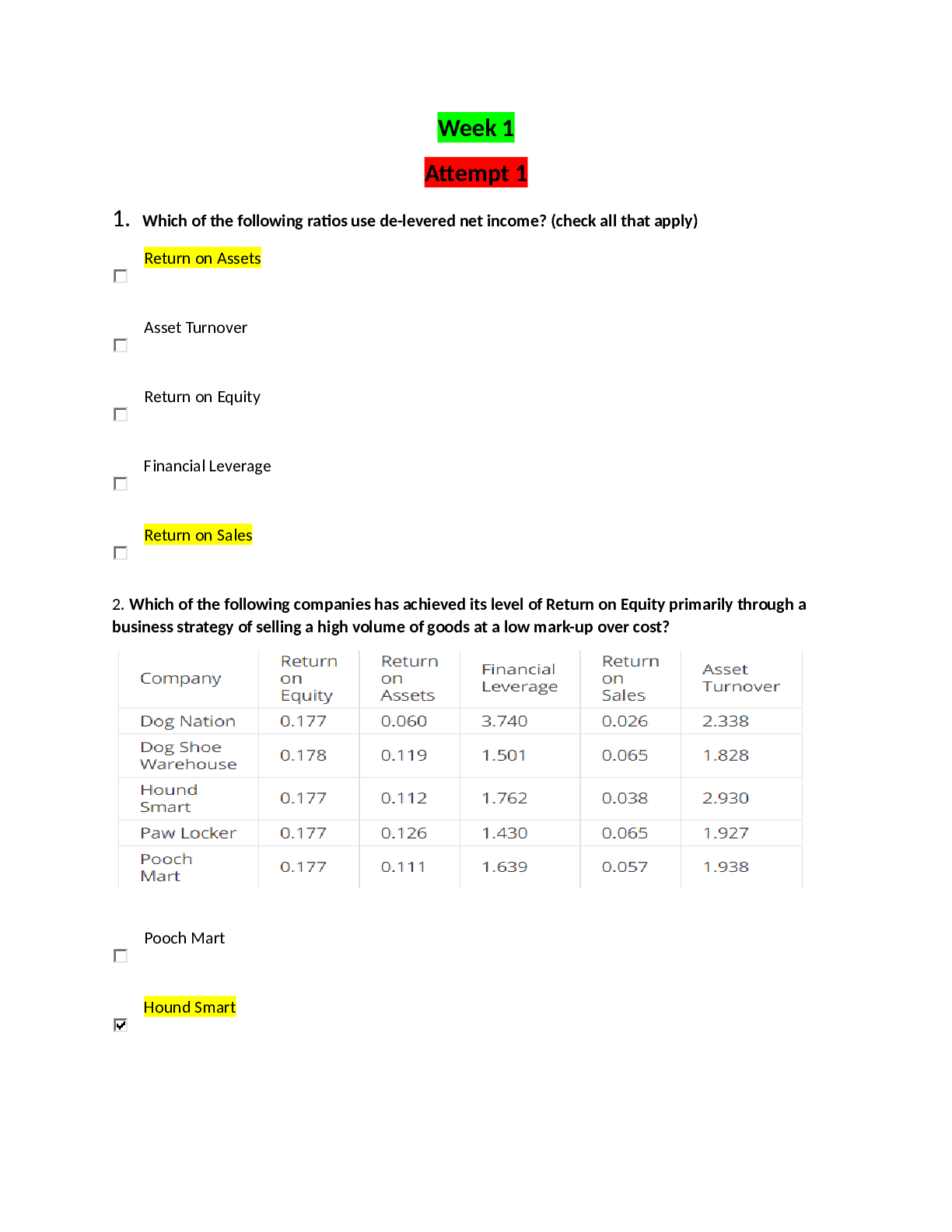
QUESTION 1 1. To prevent spoofing of transactions, IPv6 IPSec uses a cryptographic checksum that incorporates a shared encryption key so the receiver can verify that is was sent by the apparent sen... der. True False 5.00000 points QUESTION 2 1. Which of the following identifies, tracks, and mitigates known weaknesses on hosts or applications within a computing environment? BYOD policies Slideware Vulnerability management Hairpinning 5.00000 points QUESTION 3 1. Which of the following should specifically be included in the organization's VPN solution? The prohibiting of split tunneling Encouraging shared VPN credentials Types of VPN connections supported How scalable the VPN is 5.00000 points QUESTION 4 1. One of the most critical steps in VPN troubleshooting is determining whether the correction results in new problems. True False 5.00000 points QUESTION 5 1. Which of the following characteristics relates to authentication header (AH)? It is a document that defines or describes computer and networking technologies. These documents are published by the Internet Engineering Task Force, the standards body for Internet engineering specifications. RFCs exist for hardware, operating systems, protocols, security services, and much more. It is an older protocol largely replaced by IPSec and SSL/ TLS-based VPNs in production environments, but it is still in use in some older environments. It is an early proprietary protocol from Microsoft. It is a protocol that provides integrity protection for packet headers and data, as well as user authentication. 5.00000 points QUESTION 6 1. When considering training, one should determine the mechanism for training before gathering the appropriate information. True False 5.00000 points QUESTION 7 1. What is the Internet Engineering Task Force (IETF)? An early proprietary protocol from Microsoft An older protocol largely replaced by IPSec and SSL/ TLS-based VPNs in production environments, but still in use in some older environments A protocol that provides integrity protection for packet headers and data, as well as user authentication The standards body for Internet-related engineering specifications 5.00000 points QUESTION 8 1. To mitigate the risk of security threats and breaches, all installers should be trained before installing the VPN. True False 5.00000 points QUESTION 9 1. Which of the following describes Layer 2 Tunneling Protocol (L2TP)? The standards body for Internet-related engineering specifications An older protocol largely replaced by IPSec and SSL/ TLS-based VPNs in production environments, but still in use in some older environments The second core IPSec security protocol; it can perform authentication to provide integrity protection, although not for the outermost IP header An early proprietary protocol from Microsoft 5.00000 points QUESTION 10 1. Which of the following refers to an early communications protocol that competed with Point-to-Point Tunneling Protocol? Point-to-Point Tunneling Protocol (PPTP) Layer 2 Tunneling Protocol (L2TP) Layer 2 Forwarding (L2F) Protocol Internet Engineering Task Force (IETF) 5.00000 points QUESTION 11 1. The least common method for implementing a highly available VPN involves buying two VPN hardware units and configuring them as a highly available pair. True False 5.00000 points QUESTION 12 1. Which of the following characteristics relates to Point-to-Point Protocol (PPP)? The standards body for Internet-related engineering specifications A protocol that provides integrity protection for packet headers and data, as well as user authentication A protocol commonly used in establishing a direct connection between two networking nodes An older protocol largely replaced by IPSec and SSL/TLS-based VPNs in production environments, but still in use in some older environments 5.00000 points QUESTION 13 1. One of the most important steps in VPN troubleshooting is documenting processes and procedures. True False 5.00000 points QUESTION 14 1. Which term describes an early proprietary protocol from Microsoft? Authentication Header (AH) Layer 2 Forwarding (L2F) Protocol Internet Engineering Task Force (IETF) Point-to-Point Tunneling Protocol (PPTP) 5.00000 points QUESTION 15 1. A VPN deployment plan does not need to take into consideration the support of encryption protocols. True False 5.00000 points QUESTION 16 1. Which type of architecture places a firewall in front of the VPN to protect it from Internet-based attacks as well as behind a firewall to protect the internal network? Bi-lateral architecture Two-prong approach Two-factor architecture DMZ architecture 5.00000 points QUESTION 17 1. Which of the following is commonly used with an authentication header to provide both confidentiality and integrity protection for communications? Internet Key Exchange (IKE) Layer 2 Forwarding (L2F) Encapsulating Security Payload (ESP) Point-to-Point Protocol (PPP) 5.00000 points QUESTION 18 1. Operating system virtualization is the emulation of an operating system environment hosted on another operating system. True False 5.00000 points QUESTION 19 1. Which component of Secure Shell (SSH) Protocol provides server authentication, confidentiality, and integrity with perfect forward secrecy? Rsync Connection Protocol Transport Layer Protocol User Authentication Protocol 5.00000 points QUESTION 20 1. When developing a deployment plan for the VPN, power, heating, and cooling requirements are generally covered in the VPN’s technical specifications. True False [Show More]
Last updated: 2 years ago
Preview 1 out of 5 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$8.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 09, 2022
Number of pages
5
Written in
Additional information
This document has been written for:
Uploaded
Aug 09, 2022
Downloads
0
Views
101





.png)
.png)
.png)
.png)
.png)
.png)
.png)












